A Zero-day vulnerability in the .NET framework is being actively exploited in the wild. The vulnerability has been assigned CVE-2017-8759. Exploiting this vulnerability results in the remote code execution on the target machine. The attack was disclosed by FireEye. The vulnerability is being used to distribute FINSPY malware. The affected .NET versions are listed below :-
Microsoft .NET Framework 3.5.1
Microsoft .NET Framework 3.5
Microsoft .NET Framework 4.5.2
Microsoft .NET Framework 4.6
Microsoft .NET Framework 4.6.2
Microsoft .NET Framework 2.0 Service Pack 2
Microsoft .NET Framework 4.6.1
Microsoft .NET Framework 4.7
Microsoft .NET Framework 4.6.2/4.7
Microsoft .NET Framework 4.6/4.6.1/4.6.2/4.7
Microsoft has addressed this CVE in its September patch release. Please refer to Microsoft Security Update Guide for the corresponding KB’s. Microsoft has rated this issue a Important.
Vulnerability:
CVE-2017-8759 is a code injection vulnerability in the WSDL parser for SOAP. Web Services Description Language (WSDL) is a description language used to describe details and capabilities of a Web Service. Developers use WSDL file to auto-generate code that knows how to interact with a web service.
The PrintClientProxy() method in wsdlparser.cs calls IsValidUrl(), neither PrintClientProxy or IsValidUrl check if the provided input contains a CRLF. CRLF is used to denote End of Line (EOL) in HTTP.
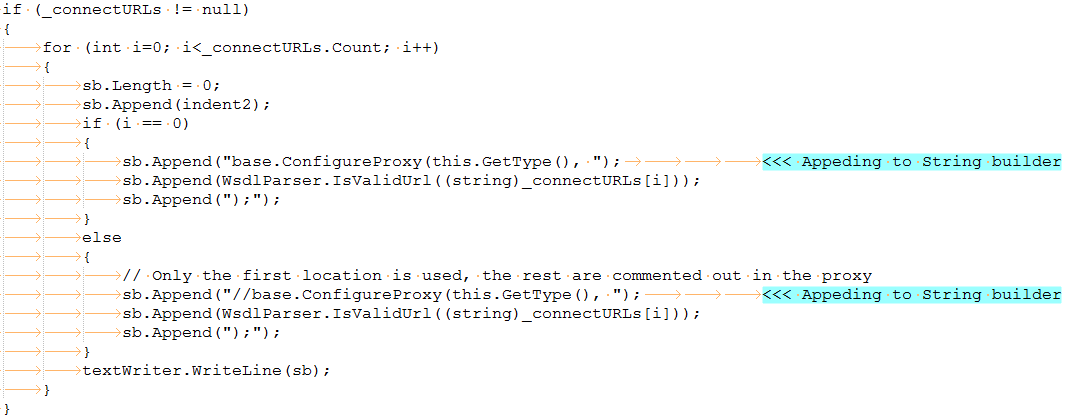
When there are multiple connections to URLs the code appends “//base.ConfigureProxy(this.GetType(),” to the StringBuilder variable and comments out the remaining addresses. If a CRLF is encountered the data following it will not be commented as it is pushed on to the next line. This means the attacker can control what data should not be commented.
In the samples observed by FireEye, Rich Text Format (.rtf) documents were used to exploit this vulnerability to inject a call to System.Diagnostics.Process.Start. The .rtf file contained a malicious SOAP WSDL definition. The .NET framework parses this definition to generate the appropriate .cs source file, compiles it as library file and loads it in to the Microsoft Office address space. More details about its execution cycle can be found here. At the end of the cycle the target machine is infected with FINSPY malware.
FINSPY:
FINSPY is commercial grade espionage malware sold by Gamma Group works. It is capable of remotely monitoring and controlling infected targets, employs covert communication methods for C&C activity, Skype monitoring, surveillance via webcam and microphone etc.
Mitigation:
We request organizations to scan their network with QID 91410 to detect vulnerable machines on the network and follow the Microsoft Security Update Guide to patch the corresponding machines.Windows Defender Antivirus detects this exploits as Exploit:RTF/Fitipol.A,Behavior:Win32/Fitipol.A and Exploit:RTF/CVE-2017-8759
Please continue follow ThreatProtect for more information on this vulnerabilities.
References:
FireEye Uncovers CVE-2017-8759: Zero-Day Used in the Wild to Distribute FINSPY
Understanding WSDL
CVE-2017-8759 | .NET Framework Remote Code Execution Vulnerability
Exploit for CVE-2017-8759 detected and neutralized
Joe Sandbox : CVE-2017-8759 malicious document