A remote command injection vulnerability has been identified in Palo Alto Expedition (Migration Tool) . Expedition tool is used for moving firewall configurations from another vendor to Palo Alto’s product. It makes the conversion process easier to accomplish. MITRE has assigned CVE-2018-10143 for this vulnerability.
Vulnerability Analysis:
This vulnerability exists in convertCSVtoParquet.php which accepts user controlled input in a path parameter. A payload similar to the one shown below can be used to exploit this command injection vulnerability:
1:2:/tmp/log && COMMAND_INJECTION
Let’s replace COMMAND_INJECTION with a command of our choosing.
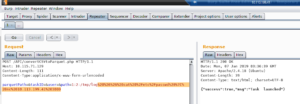
Next step is to run netcat in listen mode on a random port and wait for the output of the injected command in POST request.
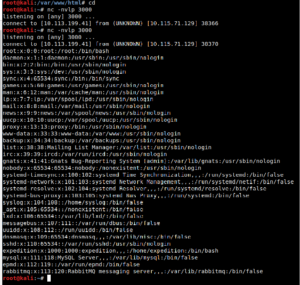
Conclusion:
Vendor has not confirmed the vulnerability. However customers can upgrade to the latest supported version of Expedition (Migration Tool).Customers are advised to scan their network remotely using QID#13385 to find vulnerable Expedition (Migration Tool) versions.