A privilege escalation vulnerability referred as “Dirty Sock” has been identified in the default installations of Ubuntu Linux. The actual vulnerability is in the Snapd daemon (snapd REST API), which is included by default with all recent Ubuntu versions and probably other Linux distros. Dirty Sock is a local privilege escalation flaw that lets attackers create root accounts. CVE-2019-7304 has been assigned to track this vulnerability. Snapd version 2.37.1 has been released to address this issue.
Affected versions:
Snapd versions 2.28 through 2.37 are all vulnerable.
About Snapd:
snapd is a REST API daemon for managing snap packages. It allows users to download and install apps in the .snap file format. systemd service called “snapd” handles the management of locally installed snaps and communication with it’s online store. In Ubuntu OS, this service is installed automatically and runs under the context of the “root” user.
Exploitation:
A local attacker can exploit this vulnerability by bypassing the access control restrictions imposed on this Snaps API server and gain access to restricted API functions to create new root-level accounts. A security researcher also published two proof-of-concept (PoC) codes for Ubuntu systems.
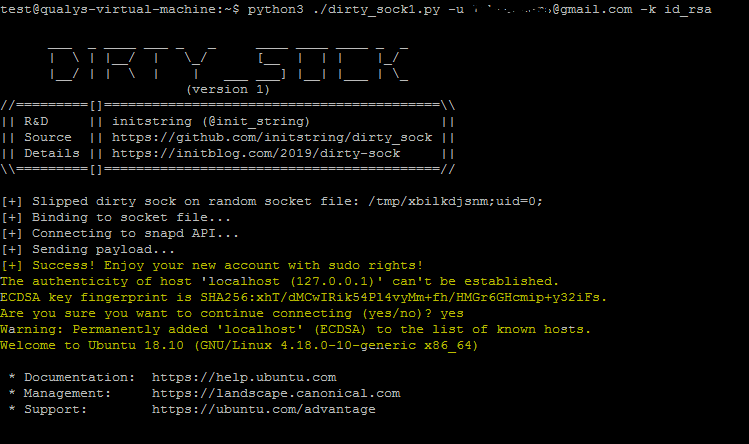
1. dirty_sockv1 : This Code leverages the ‘POST /v2/create-user’ API function to exploit the vulnerability. But in order to run the exploit, attacker would need a registered Ubuntu SSO email address and the associated SSH private key.
$ dirty_sockv1.py -u us**@***il.com -k id_rsa
2. dirty_sockv2 : This code uses the ‘POST /v2/snaps’ API to sideload an empty snap with an install hook that creates a new user. This works on systems that do not have the SSH service running and no internet connection. For successful exploitation, system would need some snapd components installed for sideloading.
Mitigation:
We request that organizations apply the latest fixes provided by the respective vendors. Qualys has released QID#197371 to detect affected systems. Qualys will continue to add more detections as vendors release their patches.
Please continue to follow Qualys Threat Protection for more coverage on this vulnerability.
References & Sources:
https://github.com/snapcore/snapd
https://github.com/snapcore/snapd/wiki/REST-API
https://people.canonical.com/~ubuntu-security/cve/2019/CVE-2019-7304.html