Summary:
Apache Tomcat has a vulnerability in the CGI Servlet which can be exploited to achieve remote code execution (RCE). Only Windows is exploitable while running in a non-default configuration in conjunction with batch files.
Description:
conf/context.xml as well conf/web.xml enables CGI in tomcat. Common Gateway Interface (CGI) is a standard protocol allows passing of command line arguments to the script or program being executed via URL parameters.
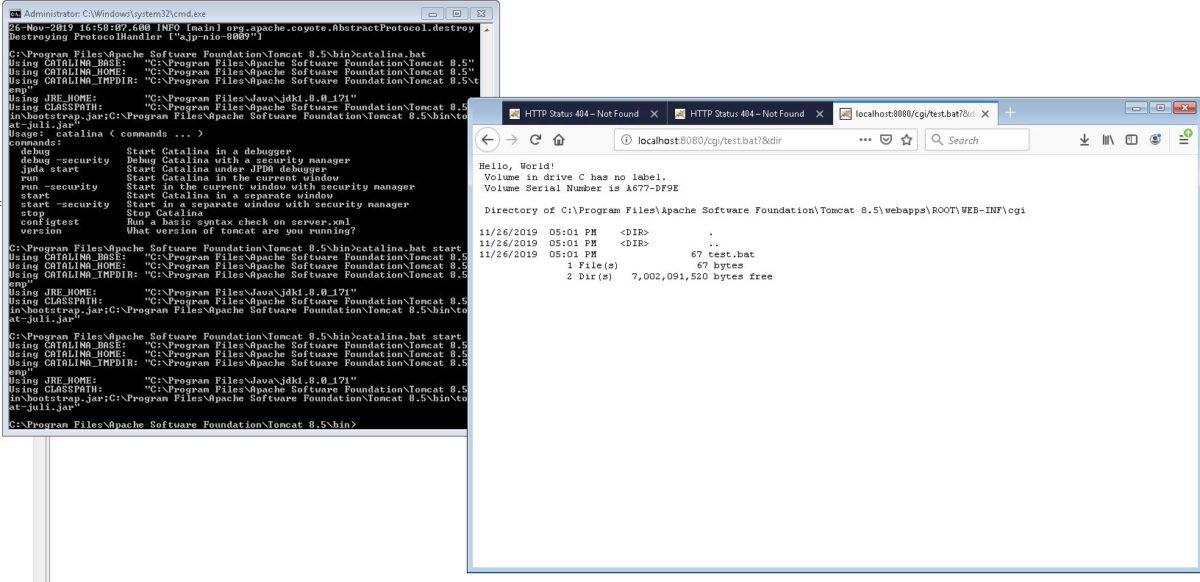
Sample URI: http://localhost:8080/cgi/test.bat?&dir converts to test.bat &dir
A special CGI servlet supports execution of CGI scripts in a non-default configuration in Apache Tomcat. Java Runtime Environment (JRE)’s java.lang.Runtime class, exec() function is the main parameter for actual execution of the CGI scripts.
A command injection is possible when command line argument passing and CGI support is enabled in Apache Tomcat in Windows , via parameter interpolation when calling a batch file (*.bat / *.cmd). This happens because “cmd.exe” performs interpolation on some special characters before execution which can cause other shell commands to be called.
NOTE: Neither Apache Tomcat nor the Windows JRE perform any kind of input validation for these special characters.
Prerequisites for the exploit to work:
– Install a Java Runtime Environment (JRE) in Windows.
– Download a vulnerable version of Tomcat and extract.
At, Qualys labs we have tried to generate a presentation. The presentation itself have steps to recreate and run the exploit. To retrieve the information from a Windows machine, POC is publicly available. This vulnerability leads to client compromise and was considered under CVE-2019-0232.
Tadaaaaaaaaaaaa…. RCE, gotchya..!!
Affected Products:
Apache Tomcat 9.0.0.M1 to 9.0.17, 8.5.0 to 8.5.39 and 7.0.0 to 7.0.93
Advisory:
https://tomcat.apache.org/security-9.html
Mitigation:
The vendor released a fix in Tomcat versions 7.0.94, 8.5.40 and 9.0.19.
Qualys customers can scan their network with QID#150240 and QID#87384 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://github.com/setrus/CVE-2019-0232
- https://www.exploit-db.com/exploits/47073
- https://ss64.com/nt/syntax-redirection.html
- https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-xp/bb490954(v=technet.10)#using-multiple-commands-and-conditional-processing-symbols