Description:
A kernel use-after-free vulnerability was identified in the XFRM netlink subsystem.There is an out-of-bounds array access in __xfrm_policy_unlink, which causes denial of service, because verify_newpolicy_info in net/xfrm/xfrm_user.c mishandles directory validation. This vulnerability also leads to local privilege escalation.This issue was assigned under CVE-2019-15666. For more details about the vulnerability please visit here.
Affected Products:
Linux kernel before 5.0.19
Exploitation:
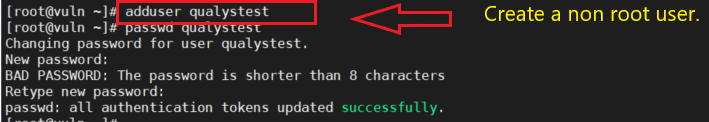
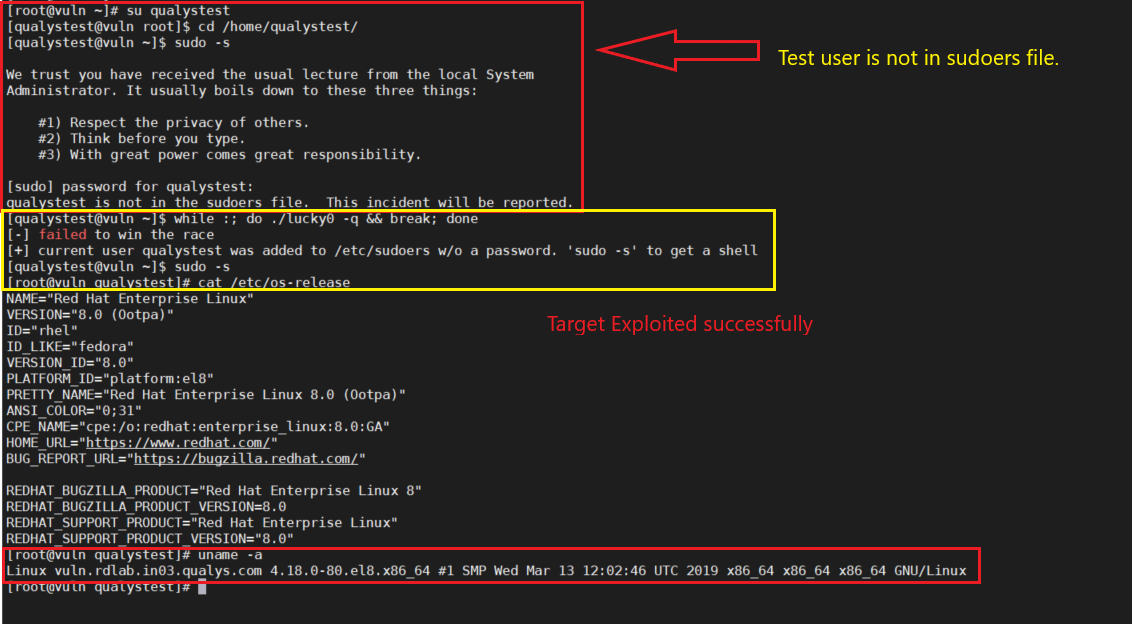
We have successfully tested the poc on our lab target.
Mitigation:
Upgrade to latest kernel versions available.
Qualys customers can scan their network with QID(s)# 172967,172805,158143,172756,172755,172626,158137,172578,177317,177316 to detect vulnerable assets.
Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://duasynt.com/blog/ubuntu-centos-redhat-privesc
- https://github.com/duasynt/xfrm_poc