Summary:
‘UNC path injection’ vulnerability was observed critically in Zoom client for Windows while the work form home and online education conferences are new normal. This leads remote attackers to steal login credentials for victims’ Windows systems.
Description:
A critical zero-day vulnerability in zoom video conferencing app. This vulnerability was found in windows client of the zoom. It allows limited RCE remote code execution, which can allow leaking network information. The app has vulnerability in handling of Uniform Resource Identifier paths, which can result in Universal Naming Convention (UNC) injection.
The attack involves the ‘SMBRelay technique’ wherein Windows automatically exposes a user’s login username and NTLM password hashes to a remote server, when attempting to connect and download a file hosted on it.
When sending a chat message, any URLs that are sent are converted into hyperlinks so that other members can click on them to open a web page in their default browser. If a user clicks on a UNC path link, Windows will attempt to connect to the remote site using the SMB file-sharing protocol to open the remote file or whatever has been shared as links over chat in meetings.
When doing this, by default Windows will send the user’s login name and their NTLM password hash, which can be cracked using free tools like Hashcat to dehash, or reveal, the user’s password.
What makes this particularly problematic is that with the current power of our graphics cards and CPUs, a program like Hashcat can dehash passwords quickly. Anyone can add malicious links to chat like to expose computer name or domain or windows hashed password. These links can have Microsoft Excel, which can execute the malicious code when opened. Once anyone has your hash password it’s not very difficult to hack the network or other server. This also allows creating backdoor or run malware on target device.
POC would look like:
\\localhost\c$\Windows\System32\cmd.exe
OR
\\127.0.0.1\c$\Windows\System32\cmd.exe
The flaw affects Zoom’s Windows client only. On Apple’s macOS, the Zoom client doesn’t make the links clickable.
The Boston branch of the law enforcement agency said it has received multiple reports of Zoom conferences being disrupted by pornographic and/or hate images and threatening language.
The video conferencing app late last month updated its iOS app to remove the software development kit (SDK) that was providing users’ data to Facebook through the Login with Facebook feature.
Affected Products:
Zoom Client versions prior to 4.6.9 (19253.0401) on Windows are vulnerable.
Advisory:
https://blog.zoom.us/wordpress/2020/04/01/a-message-to-our-users/
Mitigation:
Zoom has updated the patch and released for this zero day UNI-injection.
For those who do not want to wait for a fix, there is a Group Policy that can be enabled that prevents your NTLM credentials from automatically being sent to a remote server when clicking on a UNC link.
This policy is called ‘Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers‘ and is found under the following path in the Group Policy Editor.
Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers
If this policy is configured to Deny All, Windows will no longer automatically send your NTLM credentials to a remote server when accessing a share.
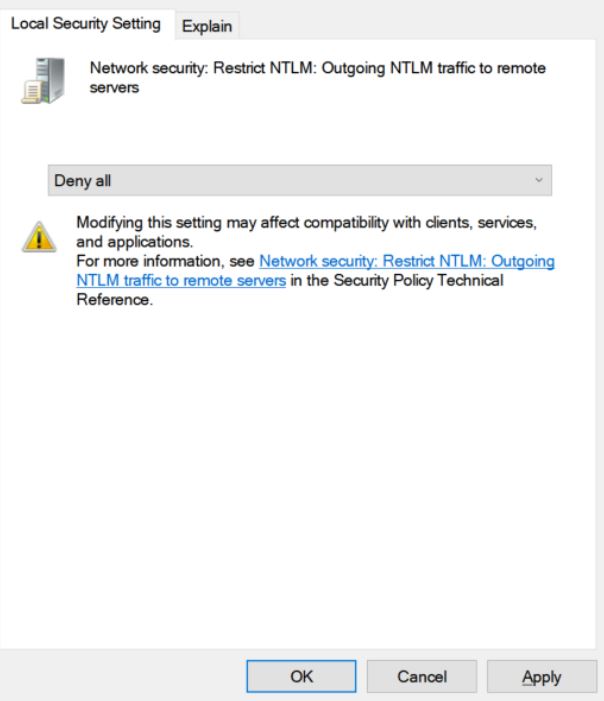
Image Source: bleepingcomputer
It should be noted that when this policy is configured on domain-joined machines, it could cause issues when attempting to access shares. You can view this article to learn more about adding exceptions to the above policy. If you are a Windows 10 Home user, you will not have access to the Group Policy Editor and will have to use the Windows Registry to configure this policy.
This can be done by creating the RestrictSendingNTLMTraffic Registry value under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0 key and setting it to 2.
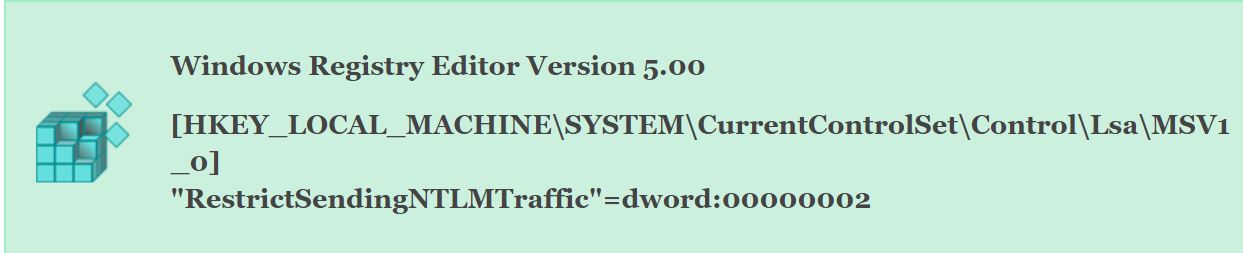
Image Source: bleepingcomputer
To properly create this value, Windows users will need to launch the Registry Editor as an Administrator. When the above Registry settings are properly configured, the RestrictSendingNTLMTraffic value will look like the following image.
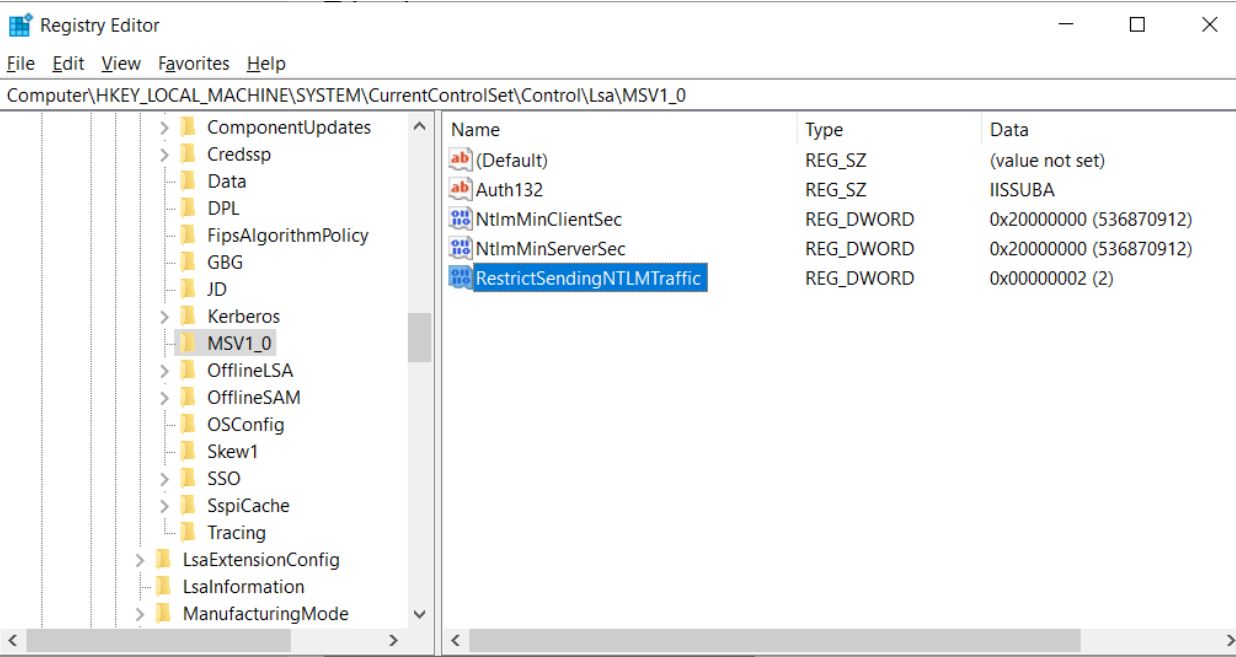
Image Source: bleepingcomputer
To revert to the default Windows behavior of sending your NTLM credentials, you can just disable the policy by deleting the RestrictSendingNTLMTraffic value.
Qualys customers can scan their network with QID(s)# 372477 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://www.bleepingcomputer.com/news/security/zoom-lets-attackers-steal-windows-credentials-run-programs-via-unc-links/