Overview
On January 14, 2020, Oracle disclosed the critical vulnerability CVE-2020-2551 . Vulnerability has been discovered in the Oracle WebLogic Server, component of Oracle Fusion Middleware using IIOP protocol. Flaw existed the way WebLogic Server handled IIOP deserialization. It led to remote code execution using IIOP protocol via Malicious JNDI Lookup.
Before looking into vulnerability, let us first understand some of the below concepts.
Weblogic server is an application server used to develop and deploy multi-tier distributed applications.
RMI (Remote Method Invocation) allows an object running on one Java virtual machine(JVM) and also can access the other object running in a different JVM.
CORBA (Common Object Request Broker Architecture) allows objects across different platforms to communicate with each other.
IIOP (Internet Inter ORB Protocol) used by CORBA objects to communicate over the internet. IIOP enables servers and browsers to exchange complex objects.
WebLogic Server supports RMI over IIOP. It combines the advantages of both technologies. WebLogic Server has IIOP enabled by default. The transmission of objects in IIOP is carried out through serialization and deserialization.
Vulnerability Analysis
Let’s have a quick glance at this vulnerability. Two important factors in this vulnerability are JtaTransactionManager and WLInitialContextFactory class. Vulnerability occurs due to the wrong filtering of JtaTransactionManager class.
JtaTransactionManager plays an important role in JNDI Injection. JNDI is a Java API (such as ‘InitialContext.lookup(String name)’) that takes one string parameter, and if this parameter comes from an untrusted source, leads to remote code execution.
WLInitialContextFactory creates initial contexts for accessing the naming service. It uses IIOP protocol for data interaction classes.
IIOP then automatically serializes and deserializes the object during the transmission. If we send the malicious serialized object on port 7001 of Weblogic server it results in remote code execution.
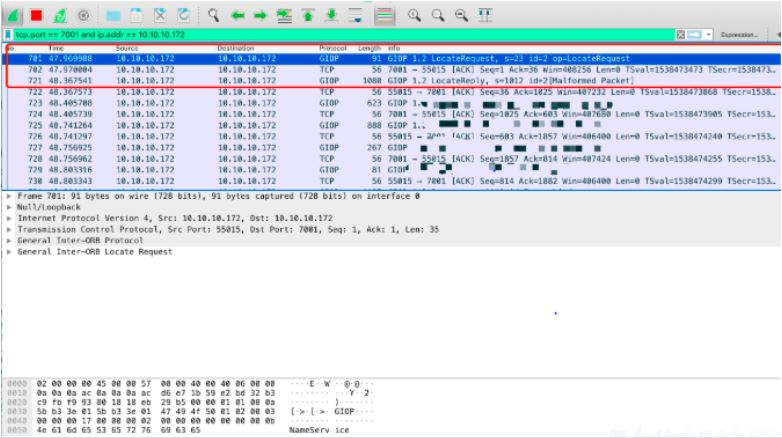
From the above image it can be seen that the packet response through IIOP as IIOP content information, IIOP is a protocol that exchanges GIOP (Common Object Request Inter-Agent Communication Protocol) information through a TCP connection.
The complete POC can be found on github.
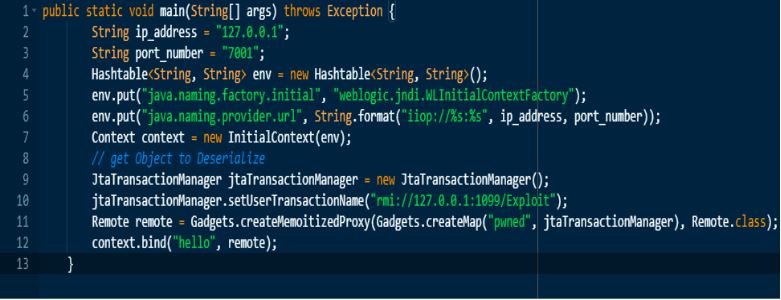
Image Source: Medium
Based on the above POC, the principle of the entire vulnerability has actually been clarified as follows:
- Get the corresponding InitialContext object by setting the value of java.naming.provider.url to iiop://127.0.0.1:7001, and then bind the serialized object and send it to IIOP Server.
- When a Weblogic server gets requested byte stream, it performs de-serialization to trigger the vulnerability.
Impact of the vulnerability
Affected versions are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0 and 12.2.1.4.0. Exploitable vulnerability allows unauthenticated remote attackers via IIOP to compromise Oracle WebLogic Server. Successful attacks of such vulnerability can result in the takeover of Oracle WebLogic Server.
Advisory
https://www.oracle.com/security-alerts/cpujan2020.html
Mitigation
Qualys Threat Research Lab provides protection with the QID(s)# 372334 and 87411. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://github.com/Y4er/CVE-2020-2551
- https://medium.com/@qazbnm456/cve-2020-2551-unauthenticated-remote-code-execution-in-iiop-protocol-via-malicious-jndi-lookup-119bac7c1eb2