Overview:
On May 2020, Microsoft has fixed an Out of Bound Write vulnerability CVE-2020-1054, found in the DrawIconEx function of windows driver file. The bug was reported by CheckPoint Security Researcher Yoav Alon and Netanel Ben-Simon. Vulnerability occurs due to the Windows kernel-mode driver fails to properly handle objects in memory. This flaw allows local attacker to escalate privileges on vulnerable installations of Microsoft Windows.
Description:
Vulnerability has been found in the DrawIconEx function in win32kfull.sys. Researchers provided following parameters values in a call to DrawIconEx which successfully exploits and escalated privileges to SYSTEM.
![]()
Image Source: CheckPoint
On GitHub, researcher provided the demonstration of privilege escalation to SYSTEM by exploiting the out of Bound Write vulnerability CVE-2020-1054.
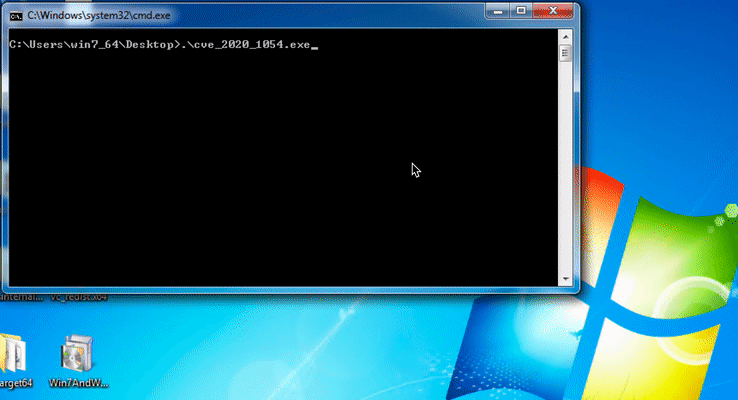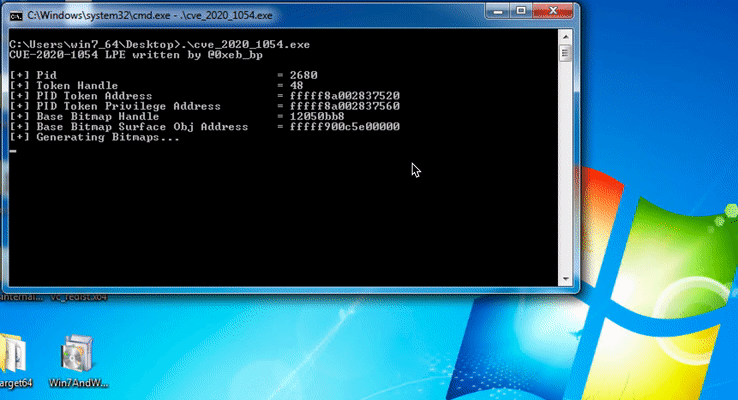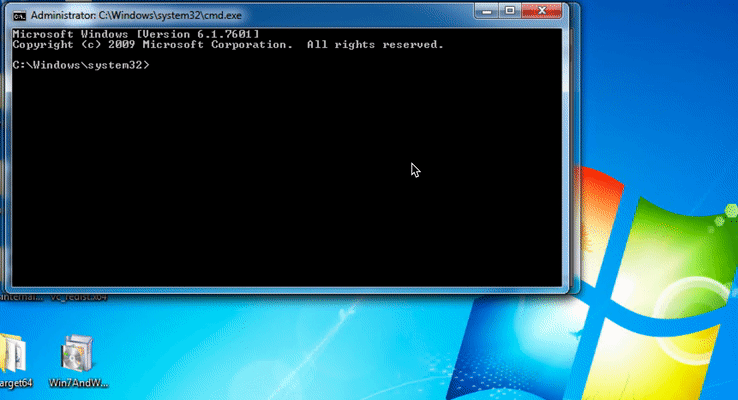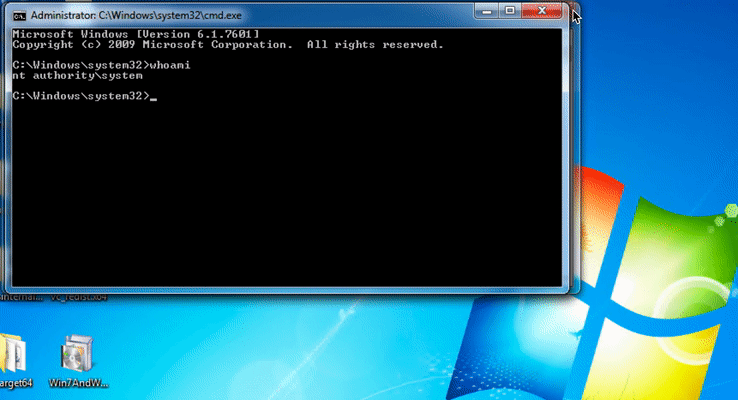
Image Source: GitHub 0xeb-bp repository
For windows 7 x64 and Windows 10 x64, POC is available on GitHub and CheckPoint.
Specific Windows KB required to run the exploit.
Affected Products:
- Windows 10 for 32-bit and x64 based Systems
- Windows 10 Version 1607 for 32-bit and x64 based Systems
- Windows 10 Version 1709 for 32-bit, x64 and ARM64-based Systems
- Windows 10 Version 1803 for 32-bit x64 and ARM64-based Systems
- Windows 10 Version 1809 for 32-bit x64 and ARM64-based Systems
- Windows 10 Version 1903 for 32-bit x64 and ARM64-based Systems
- Windows 10 Version 1909 for 32-bit x64 and ARM64-based Systems
- Windows 7 for 32-bit Service Pack 1 and x64-based Systems
- Windows 8.1 for 32-bit and x64-based systems
- Windows RT 8.1
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
- Windows Server 2008 for Itanium-Based and x64-based Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
- Windows Server 2008 R2 for Itanium-Based and x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
- Windows Server 2012
- Windows Server 2012 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 R2 (Server Core installation)
- Windows Server 2016
- Windows Server 2016 (Server Core installation)
- Windows Server 2019
- Windows Server 2019 (Server Core installation)
- Windows Server, version 1803 (Server Core Installation)
- Windows Server, version 1903 (Server Core installation)
- Windows Server, version 1909 (Server Core installation)
Advisory:
Update your system with latest patch available on following Microsoft webpage.
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1054
Mitigations:
Qualys Threat Research Lab provides protection with the QID(s)# 91636. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
https://cpr-zero.checkpoint.com/vulns/cprid-2153/
https://github.com/0xeb-bp/cve-2020-1054
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1054