Overview
On February 23, 2021, VMware released an update to fix three vulnerabilities – CVE-2021-21972, CVE-2021-21973, and CVE-2021-21974. Out of these, CVE-2021-21972 is a critical remote code execution vulnerability with the highest CVE score (9.8). The bug exists in the vROPs (vRealize Operations) plugin of VMware vCenter Server. Successful exploitation of this vulnerability could allow an unauthenticated user to execute arbitrary code on the target system.
PoC is available on GitHub.
Description
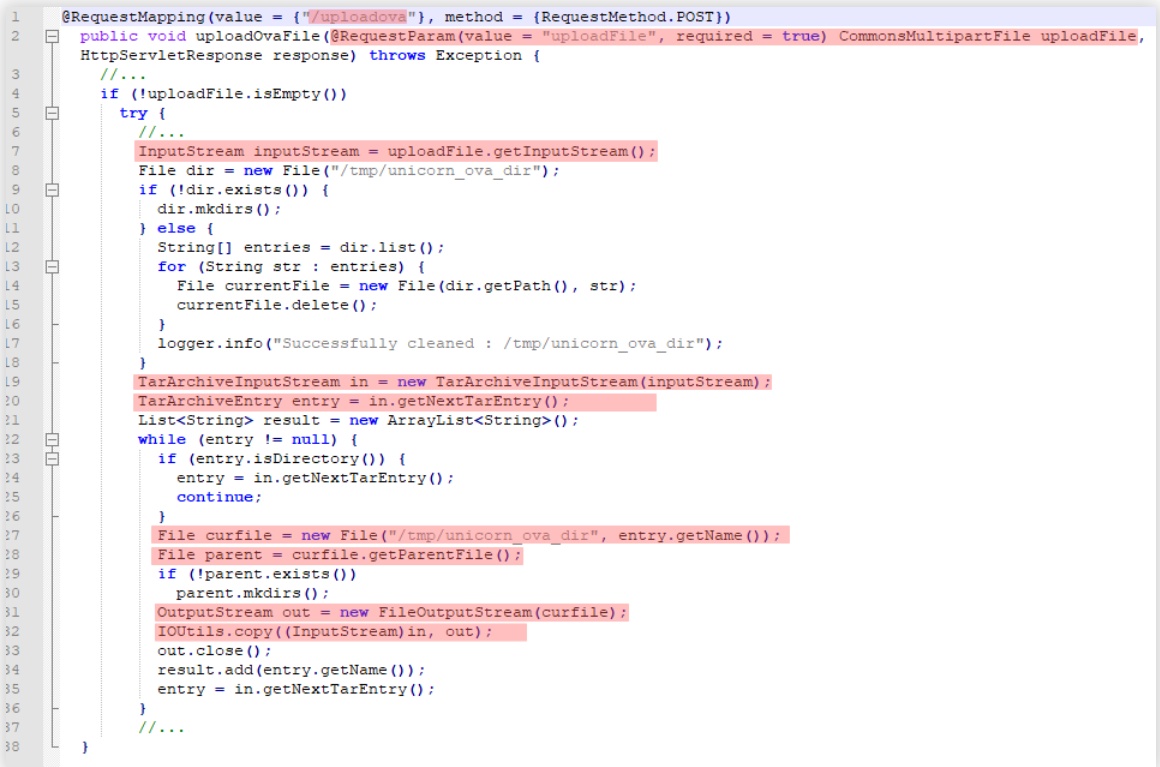
This RCE vulnerability, reported by Security Researcher Mikhail Klyuchnikov, existed due to the lack of authentication while uploading files through vRealize Operations vCenter Plugin (vropspluginui plugin). The vulnerable code was present in the uploadOvaFile function, using which the file was uploaded via an HTTP POST request to the URL /ui/vropspluginui/rest/services/uploadova.
Below is the code snippet of vulnerable function uploadOvaFile:
Image Source: ptsecurity
The researcher has demonstrated the exploitation of this vulnerability on Windows and Linux operating systems.
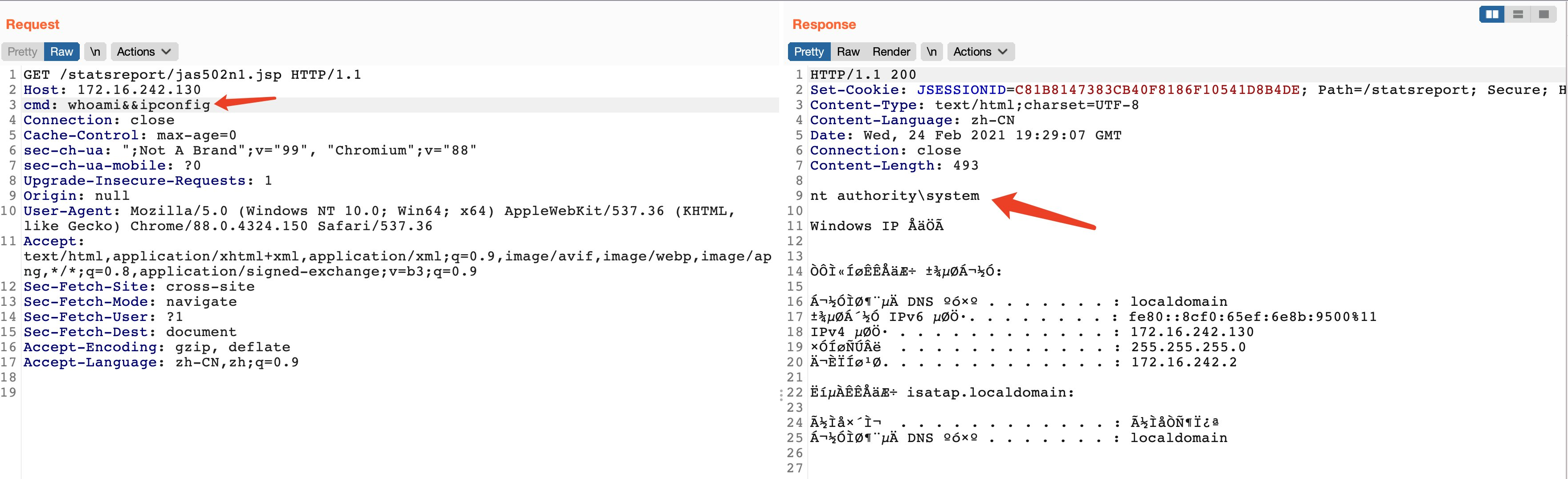
For Windows OS, we have to upload the specially crafted .jsp file on the target system using this vulnerability.
Image Source: Twitter
After successful exploitation, one can execute commands on the vulnerable system with NT AUTHORITY\SYSTEM privileges.
Image Source: Twitter
For Linux OS, private and public keys have to be generated using an SSH key, use these public keys to create a .tar archive file and then upload this tar file using the vulnerability. Following this, one can connect to the vulnerable host via SSH. After successful exploitation, the target system can be accessed with the current user rights.
Exploitation
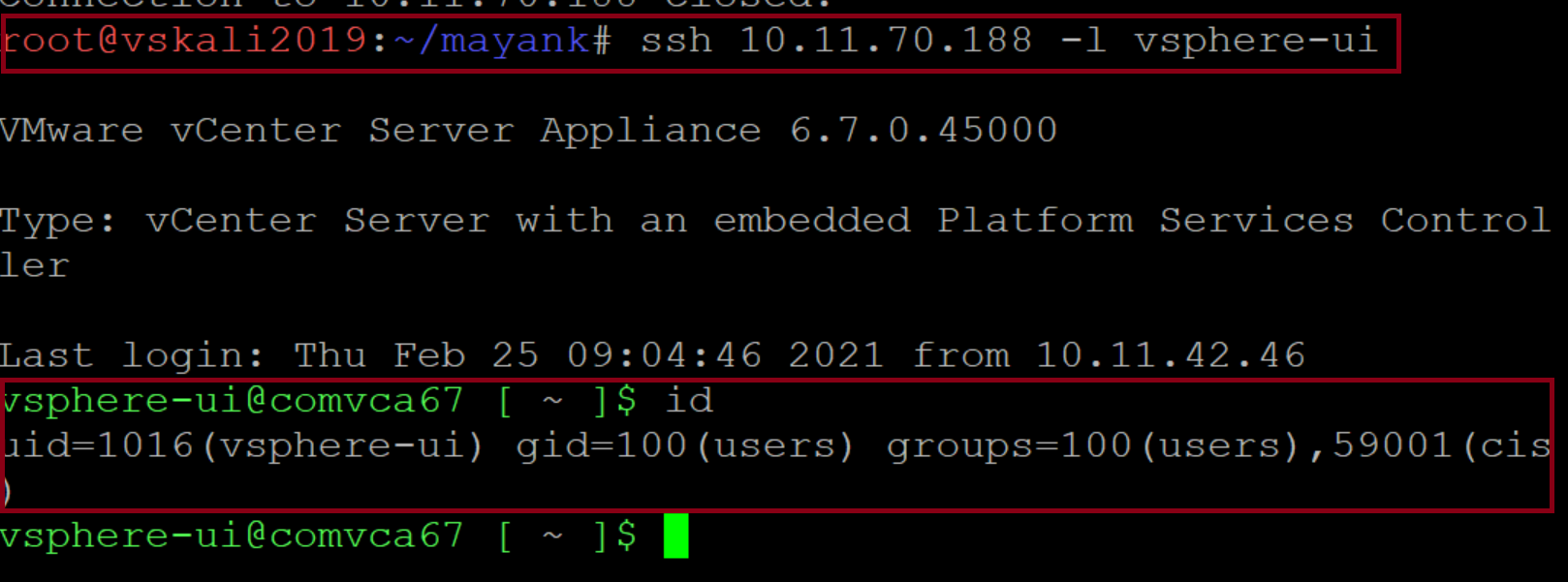
At Qualys Lab, we have tried to reproduce the issue reported for CVE-2021-21972 on Linux. We have used a publicly available PoC on GitHub.
Image Source: Qualys Lab
After successful exploitation, got access to the target system with the current user right vsphere-ui
Affected products
- vCenter Server 7.0 before 7.0 U1c
- vCenter Server 6.7 before 6.7 U3l
- vCenter Server 6.5 before 6.5 U3n
Detection
Qualys customers can scan their network with QIDs 11699, 216256, 216257, 216258 to detect vulnerable assets.
Kindly continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
Workaround
- SSH to vCSA and take a backup of the following files:Linux : /etc/vmware/vsphere-ui/compatibility-matrix.xml (vCSA)
Windows: C:\ProgramData\VMware\vCenterServer\cfg\vsphere-ui (Windows VC) - As per your target OS, insert the following line in the file mentioned above:
 The file would look a shown below:
The file would look a shown below: Image Source: VMware
Image Source: VMware - Restart the vsphere-ui service, using the command service-control –restart vsphere-ui
- Navigate to the https://<VC-IP-or-FQDN>/ui/vropspluginui/rest/services/checkmobregister. This page displays the 404/Not Found error.
- Check the status of the VMWare vROPS plugin in the client plugin. It should be displayed as incompatible.
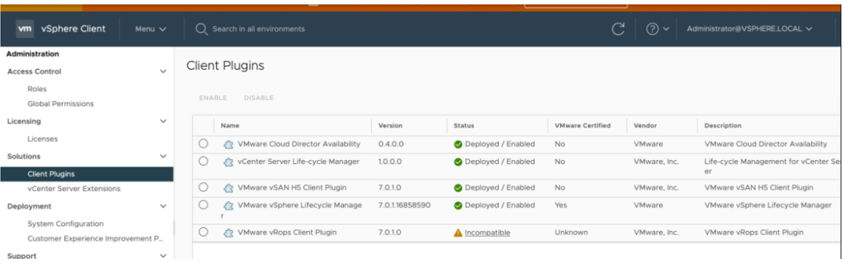 Image Source: VMware
Image Source: VMware
References