Unpatched SAP applications are vulnerable and actively exploited in the wild as per the report jointly published by SAP and Onapsis on Tuesday. Applications such as enterprise resource planning, customer relationship management software, and supply chain systems are being targeted. Onapsis researchers have recorded more than 300 successful exploit attempts from the middle of 2020 until now. CISA has also issued an alert on these activities.
In their warning, SAP stated, “These are the applications that 92 percent of the Forbes Global 2000 have standardized on SAP to power their operations and fuel the global economy. With more than 400,000 organizations using SAP, 77 percent of the world’s transactional revenue touches an SAP system. These organizations include the vast majority of pharmaceutical, critical infrastructure and utility companies, food distributors, defense and many more.”
Majorly, 6 CVEs were reported to have CVSS score – from 10 to 6.4. PoCs of a few of the CVEs are available on Github.
- CVE-2020-6287 – SAP RECON vulnerability
- CVE-2020-6207 – Missing Authentication Check in SAP Solution Manager
- CVE-2018-2380 – Insufficient validation of path information in SAP CRM
- CVE-2016-9563 – XML External Entity (XXE) in SAP NetWeaver AS Java
- CVE-2016-3976 – SAP NetWeaver AS JAVA directory traversal vulnerability
- CVE-2010-5326 – Unauthenticated arbitrary code execution on SAP NetWeaver AS Java
CVE-2020-6287 is an authentication bypass in SAP NetWeaver Application Server Java leading to complete compromise of the server.
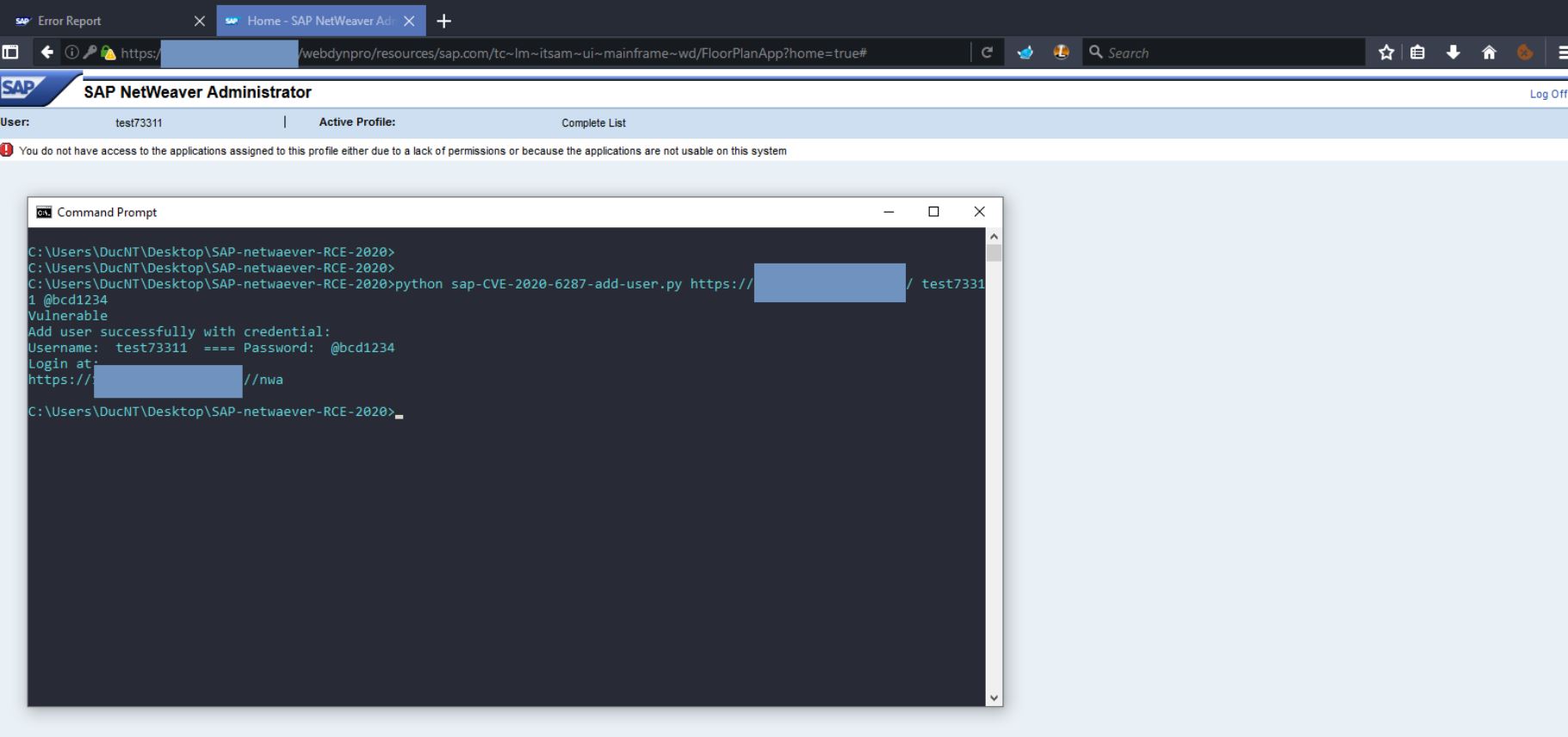
Image Source: Github
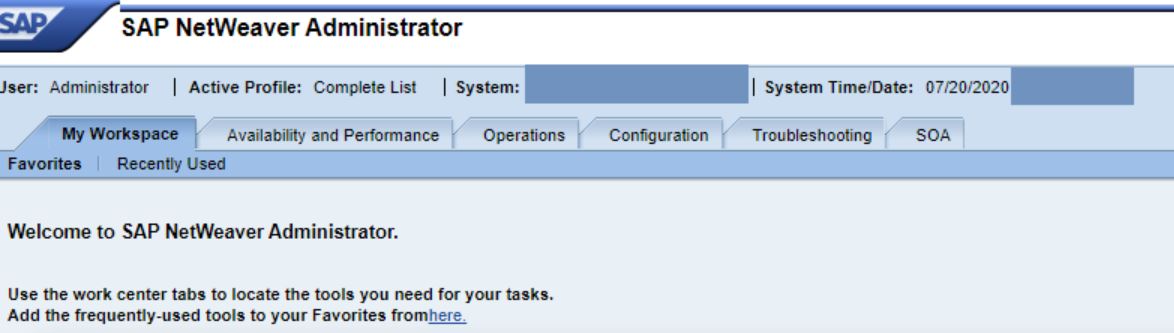
Image Source: Github
Whereas, CVE-2020-6207 is an authentication bypass in SAP Solution Manager.
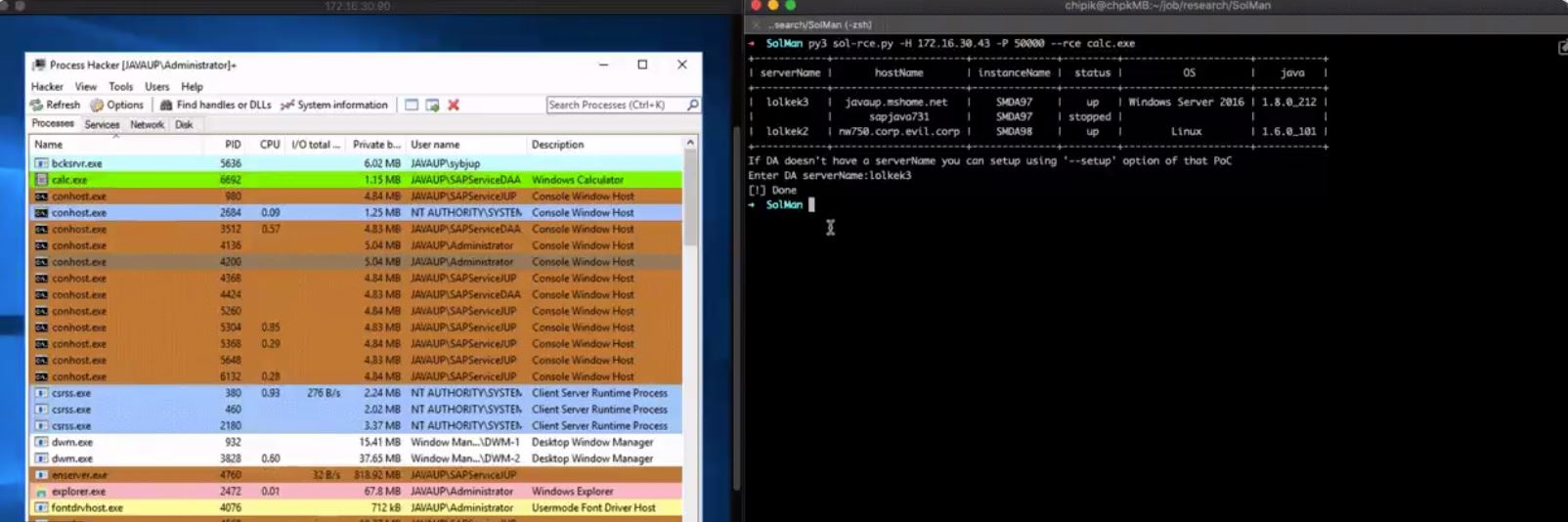
Image Source: Twitter_chipik
Mitigation
The primary way to mitigate such risks is to patch the vulnerabilities. Any web-facing accounts must have unique passwords to disallow automated brute-force attempts to break in; and any systems that don’t need to face the public web should be taken offline.
Affected products
- SAP Solution Manager
- SAP NetWeaver AS Java
- SAP CRM
Qualys Detection
Qualys customers can scan their network with QIDs 13849, 150303, 87437, 87446, 87447 and 12834 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://github.com/duc-nt/CVE-2020-6287-exploit
https://github.com/chipik/SAP_RECON
https://www.exploit-db.com/raw/39996
https://www.youtube.com/watch?v=MgCM_ieS390