Rajvardhan Agarwal, a security researcher, recently tweeted about a zero-day remote code execution vulnerability creating havoc in the browser-based vulnerability trend. Hereleased a working proof-of-concept exploit for the RCE for the V8 JavaScript engine in Chromium-based browsers.
This zero-day concerns a remote code execution vulnerability in the V8 JavaScript rendering engine that powers the web browsers. The exploit needs to be chained with another flaw that can allow it to escape Chrome’s sandbox protections, meaning the –no-sandbox flag should be enabled prior to the browser’s launch.
Once the sandbox is disabled, the PoC exploits browsers to launch the Calculator app on Windows 10 devices. Below snapshot was tested on Google Chrome 89.0.4389.114.
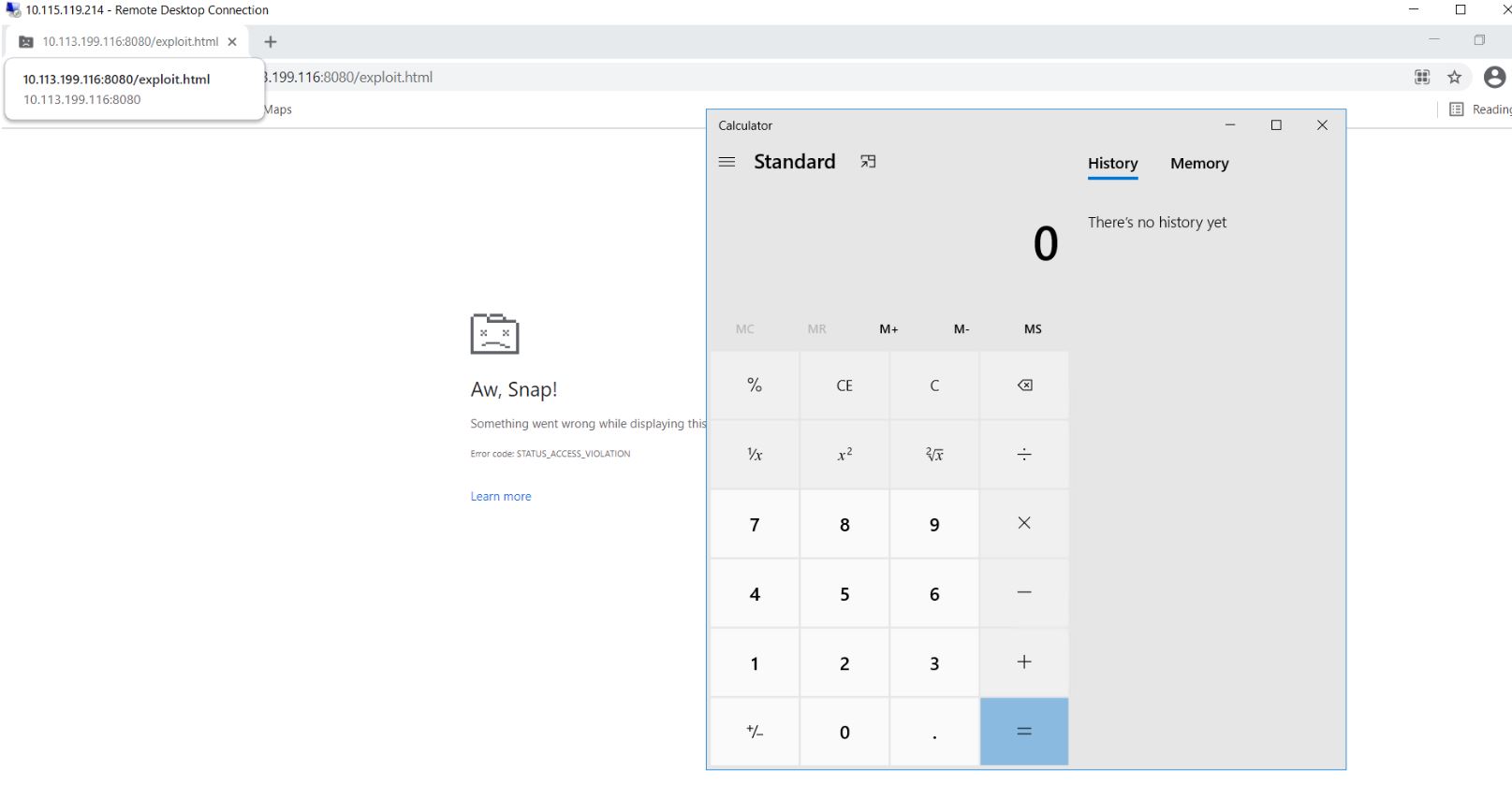
Image Source: Qualys
According to latest updates, Google has updated the stable channel for Chrome to 89.0.4389.128 for Windows, Mac, and Linux. This version addresses vulnerabilities and hence above PoC does not work, that an attacker could exploit to take control of an affected system.
NOTE: There have been so such updates for Microsoft Edge, yet.
Affected products
- Google Chrome prior to 89.0.4389.114
- Microsoft Edge prior to 89.0.774.76
Qualys Detection
Qualys customers can scan their network with QID(s) 375445 and 375446 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://twitter.com/TheHackersNews/status/1381517090633355266
https://thehackernews.com/2021/04/rce-exploit-released-for-unpatched.html
https://twitter.com/r4j0x00/status/1381643526010597380
https://github.com/r4j0x00/exploits/tree/master/chrome-0day
https://us-cert.cisa.gov/ncas/current-activity/2021/04/13/google-releases-security-updates-chrome