The Qualys Research Team has discovered a size_t-to-int type conversion vulnerability in the Linux Kernel’s filesystem layer affecting most Linux operating systems. Any unprivileged user can gain root privileges on a vulnerable host by exploiting this vulnerability in a default configuration.
The Linux file system interface is implemented as a layered architecture, separating the user interface layer from the file system implementation and from the drivers that manipulate the storage devices. It is the most important function of any operating system and is ubiquitous on all major Linux operating systems.
Successful exploitation of this vulnerability allows any unprivileged user to gain root privileges on the vulnerable host. Qualys security researchers have been able to independently verify the vulnerability, develop an exploit, and obtain full root privileges on default installations of Ubuntu 20.04, Ubuntu 20.10, Ubuntu 21.04, Debian 11, and Fedora 34 Workstation. Other Linux distributions are likely vulnerable and probably exploitable.
The Qualys exploit, also known as Sequoia, has three stages to exploit Linux Kernel. A user with less/no privilege is logged in to exploit a LPF to Linux kernel.
- Build mounts the path created in exploit in an unprivileged user namespace and call remote directory function on it.
- Creates a thread that allocates a small eBPF program, block this thread once eBPF program gets validated by kernel eBPF verifier, but compiled just in time. Here, in the unprivileged user namespace, the attacker open()s and read()s /proc/self/mountinfo and start reading the long path of bind mount directory, allowing an attacker to write a 10 byte string ~ 2GB, below the previously allocated buffer. In return, we transform an uncontrolled Out-Of-Bounds write into an information leak as well as controlled and very limited Out-Of-Bounds read and write.
- In the final stage, this limited Out-of-Bounds write into arbitrary read and write of the Kernel memory. Inside this Kernel memory, the arbitrary read is used to locate modprobe_path whereas arbitrary write is used to replace the path with executables, which in turn allows the attacker to gain full root privileges.
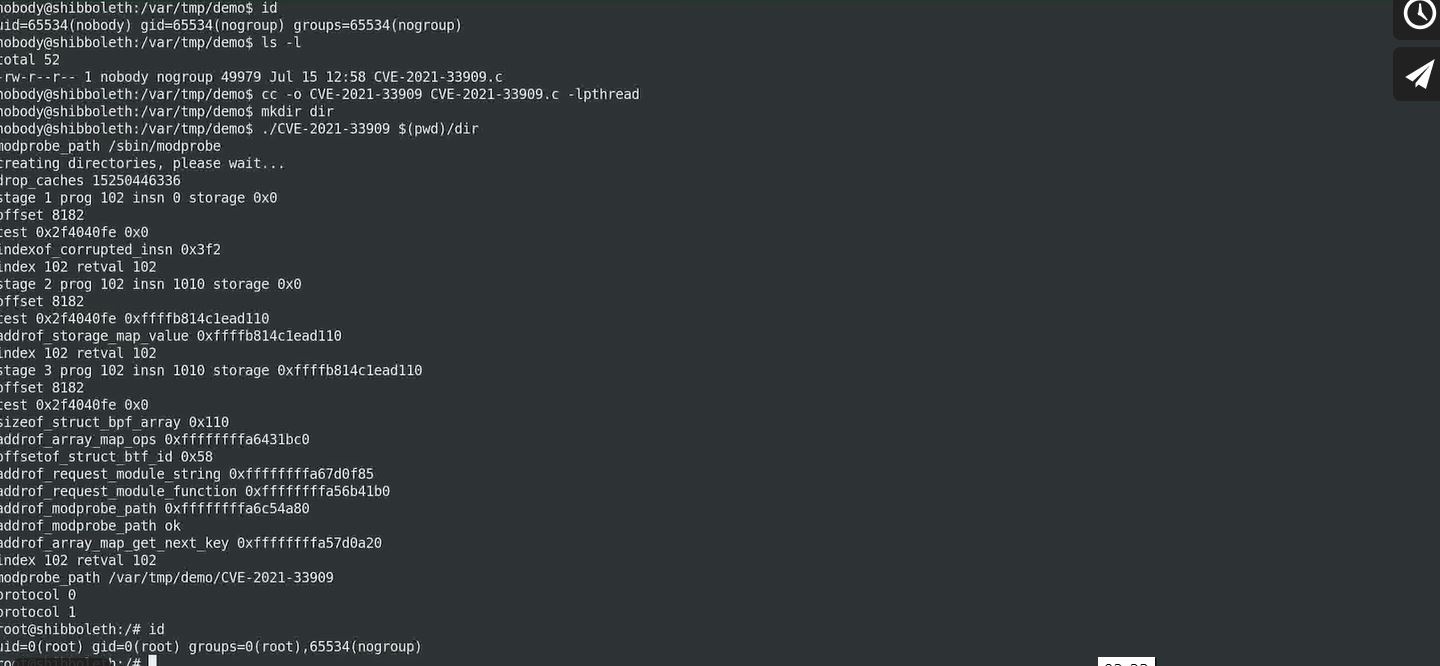
Image Source: Qualys Research Team
Long story short, if an unprivileged local attacker creates, mounts, and deletes a deep directory structure whose total path length exceeds 1GB, and if the attacker open()s and read()s /proc/self/mountinfo, results into Local Privilege Escalation.
At Qualys Research Labs, we’ve tried to put the whole exploitation in a video presentation.
Affected products
Most Linux Operating Systems
Mitigation
The following mitigations prevent only our specific exploit from working (but other exploitation techniques may exist); to completely fix this vulnerability, the kernel must be patched.
- Set /proc/sys/kernel/unprivileged_userns_clone to 0, to prevent an attacker from mounting a long directory in a user namespace. However, the attacker may mount a long directory via FUSE instead; we have not fully explored this possibility, because we accidentally stumbled upon CVE-2021-33910 in systemd: if an attacker FUSE-mounts a long directory (longer than 8MB), then systemd exhausts its stack, crashes, and therefore crashes the entire operating system (a kernel panic).
- Set /proc/sys/kernel/unprivileged_bpf_disabled to 1, to prevent an attacker from loading an eBPF program into the kernel. However, the attacker may corrupt other vmalloc()ated objects instead (for example, thread stacks), but we have not investigated this possibility.
Qualys Detection
Qualys customers can scan their network with QID(s) 239506, 239505, 239504, 239502, 239501, 239500, 239498, 239497, 239495, 750851, 198438, 198437, 198436, 198435, 750848, 178714, 178713, 178712, 750847, 750844, 178710 and 375710 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References and Sources