Microsoft has released security updates for 79 vulnerabilities in its September 2022 Patch Tuesday Edition. This month’s security updates also addressed two zero-days (CVE-2022-37969 and CVE-2022-23960). Microsoft mentioned in the advisory that CVE-2022-37969 is being exploited in the wild. Out of the 79 vulnerabilities, five are rated critical (CVE-2022-35805, CVE-2022-34700, CVE-2022-34722, CVE-2022-34721, and CVE-2022-34718).
Microsoft also included 16 updates for Microsoft Edge (Chromium-based) vulnerabilities in this Patch Tuesday edition. These vulnerabilities were patched earlier this month and addressed remote code execution and use after free flaws.
The advisory covers a total of 38 products, features, and roles, including Azure arc, Microsoft Exchange Server, .NET and Visual Studio, Microsoft Graphics Component, Windows DNS Server, Windows Group Policy, Windows IKE Extension, and many more.
The vulnerabilities are classified as follows:
- Denial of Service Vulnerability: 7
- Elevation of Privilege Vulnerability: 18
- Information Disclosure Vulnerability: 7
- Security Feature Bypass Vulnerability: 1
- Remote Code Execution Vulnerability: 30
Zero-day vulnerabilities addressed in Patch Tuesday, September 2022 Edition
Arm: CVE-2022-23960 Cache Speculation Restriction Vulnerability
This is a cache speculation vulnerability known as Branch History Injection (BHI) or Spectre-BHB. This flaw affects Windows 11 for ARM64-based Systems. This is like Spectre v2, with the exception that malicious code affects incorrectly anticipated branches within the victim’s own hardware context by using the shared branch history (stored in the CPU Branch History Buffer, or BHB).
An attacker can take advantage of the shared branch history in the Branch History Buffer (BHB) to influence incorrectly anticipated branches. Cache allocation can give the attacker access to private data.
For more information, please refer to Spectre-BHB on arm Developer.
CVE-2022-37969: Windows Common Log File System Driver Elevation of Privilege (EoP) Vulnerability
The vulnerability existing in the Windows Common Log File System (CLFS) Driver was discovered by four different security companies. To exploit this vulnerability, an attacker must be able to access the target system and run commands on it. On successful exploitation, an attacker could gain SYSTEM privileges. If the attacker does not already have access to the target machine, this approach does not permit remote code execution.
Some of the critical vulnerabilities addressed in Patch Tuesday, September 2022 Edition
CVE-2022-34718: Windows TCP/IP Remote Code Execution (RCE) Vulnerability
This vulnerability could allow an unauthenticated attacker to execute code with elevated privileges on affected systems without user interaction. By exploiting this vulnerability, an unauthenticated attacker could send a specially crafted IPv6 packet to a Windows node where IPSec is enabled, which could enable remote code execution exploitation on that machine.
NOTE: This vulnerability only affects systems with the IPSec service running. Systems with IPv6 disabled on the target machine will not be affected by this vulnerability.
CVE-2022-34721, CVE-2022-34722: Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution (RCE) Vulnerability
These vulnerabilities were discovered by Yuki Chen from Cyber KunLun. Both vulnerabilities exist in the Windows Internet Key Exchange (IKE) Protocol Extensions. These vulnerabilities allow an unauthenticated attacker to send a specially crafted IP packet to a target machine that is running Windows and has IPSec enabled, which could enable remote code execution exploitation.
NOTE: This vulnerability only impacts IKEv1, not IKEv2. However, all Windows Servers are affected because they accept both V1 and V2 packets.
CVE-2022-35805, CVE-2022-34700: Microsoft Dynamics CRM (on-premises) Remote Code Execution Vulnerability
This vulnerability was discovered by Microsoft’s security researcher Fabian Schmidt. This could allow an authenticated user to run a specially crafted trusted solution package to execute arbitrary SQL commands. This will then help the attacker to escalate and execute commands as db_owner within their Dynamics 365 database.
Evaluating workaround using Qualys Policy Compliance (PC)
Qualys Policy Compliance customers can evaluate workarounds based on the following Controls:
CVE-2022-38007 – Azure Guest Configuration and Azure Arc-enabled servers Elevation of Privilege Vulnerability
For checking Azure Arc-enabled servers on Linux:
14112 Status of the services installed on the Linux/UNIX host (stopped, running, failed, dead, …)
CVE-2022-34718 – Windows TCP/IP Remote Code Execution Vulnerability
3720 Status of the ‘IPSEC Services’ service
14916 Status of Windows Services
CVE-2022-35838 – HTTP V3 Denial of Service Vulnerability
24717 Status of the ‘HTTP/3’ service
CVE-2022-33647 – Windows Kerberos Elevation of Privilege Vulnerability
17197 Status of the ‘KDC support for claims, compound authentication, and Kerberos armoring’ setting
17109 Status of the ‘Kerberos client support for claims, compound authentication, and Kerberos armoring’ setting
17108 Status of the ‘KDC support for claims, compound authentication and Kerberos armoring’ setting (Enabled / Disabled)
CVE-2022-33679 – Windows Kerberos Elevation of Privilege Vulnerability
17197 Status of the ‘KDC support for claims, compound authentication, and Kerberos armoring’ setting
17109 Status of the ‘Kerberos client support for claims, compound authentication, and Kerberos armoring’ setting
17108 Status of the ‘KDC support for claims, compound authentication and Kerberos armoring’ setting (Enabled / Disabled)
CVE-2022-38004 Windows Fax Service Remote Code Execution Vulnerability
1161 Status of the ‘Fax’ service
14916 Status of Windows Services
CVE-2022-34721 – Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability
14916 Status of Windows Services
4026 Status of the Windows IKE and AuthIP IPsec Keying Modules service
Executing workaround using Qualys Custom Assessment and Remediation (CAR)
Customers can perform the provided mitigation steps by creating a PowerShell script and executing it on vulnerable assets.
For CAR free trial or schedule a demo: https://www.qualys.com/apps/custom-assessment-remediation/
Scripts are available in our Library.
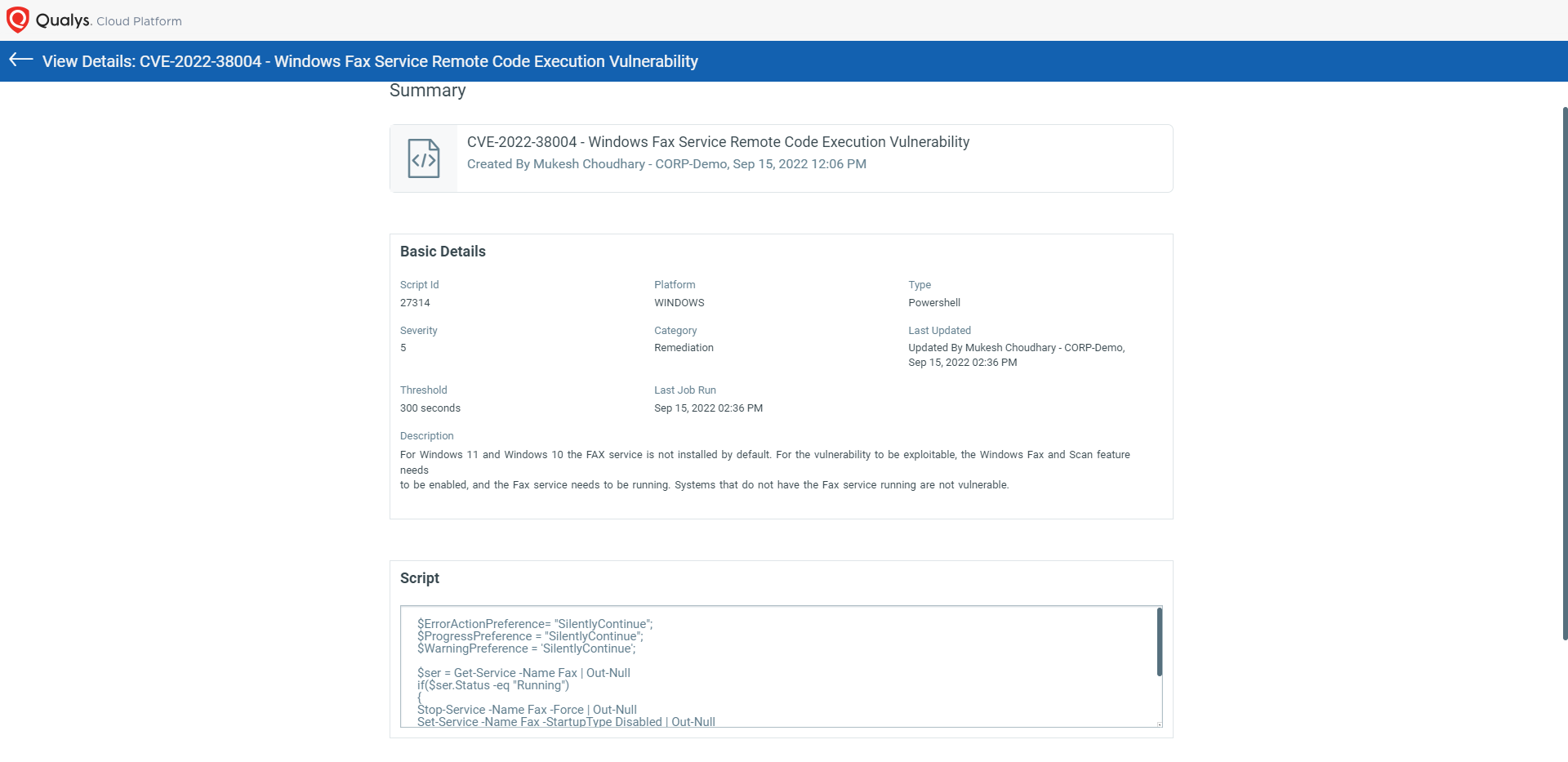
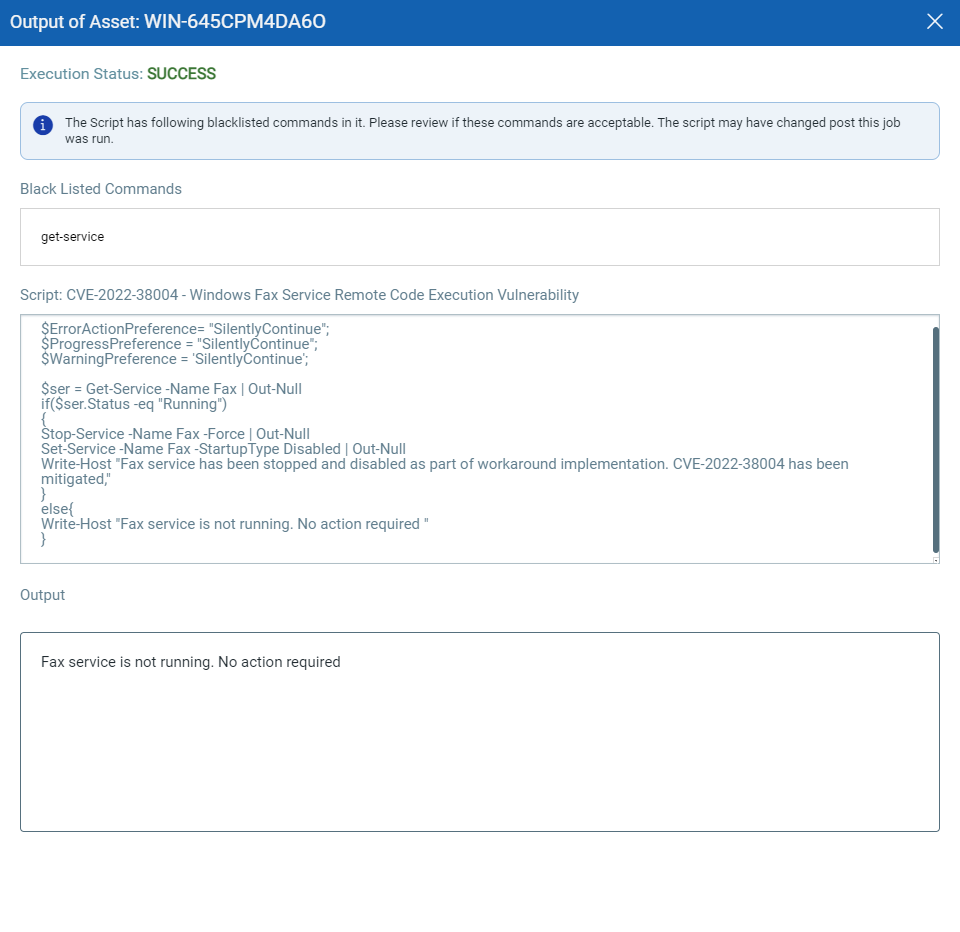
CVE-2022-38004 – Windows Fax Service Remote Code Execution Vulnerability
NOTE: For Windows 11 and Windows 10 the FAX service is not installed by default. For the vulnerability to be exploitable, the Windows Fax and Scan feature needs to be enabled, and the Fax service needs to be running. Systems that do not have the Fax service running are not vulnerable.
Script Details:
Script Output:
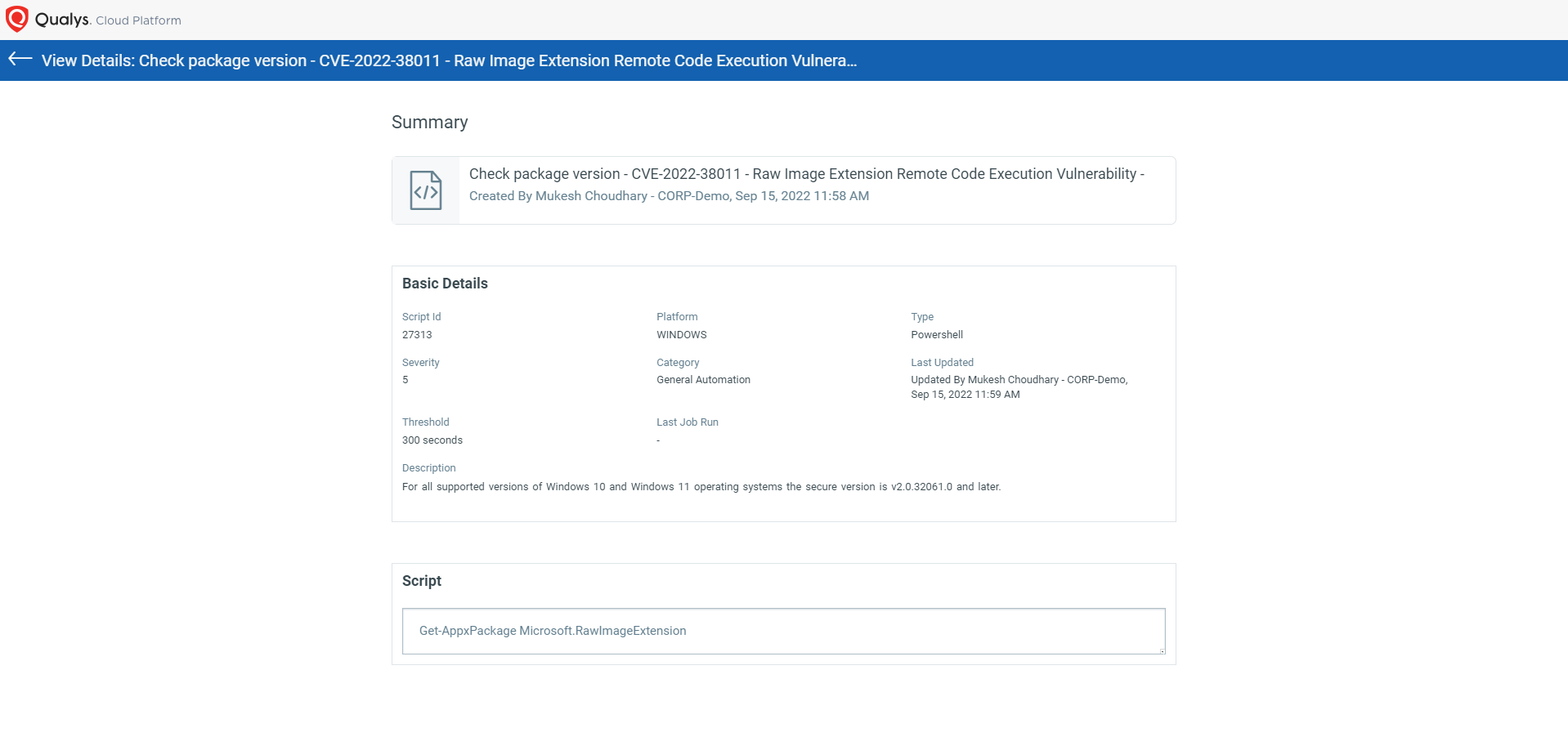
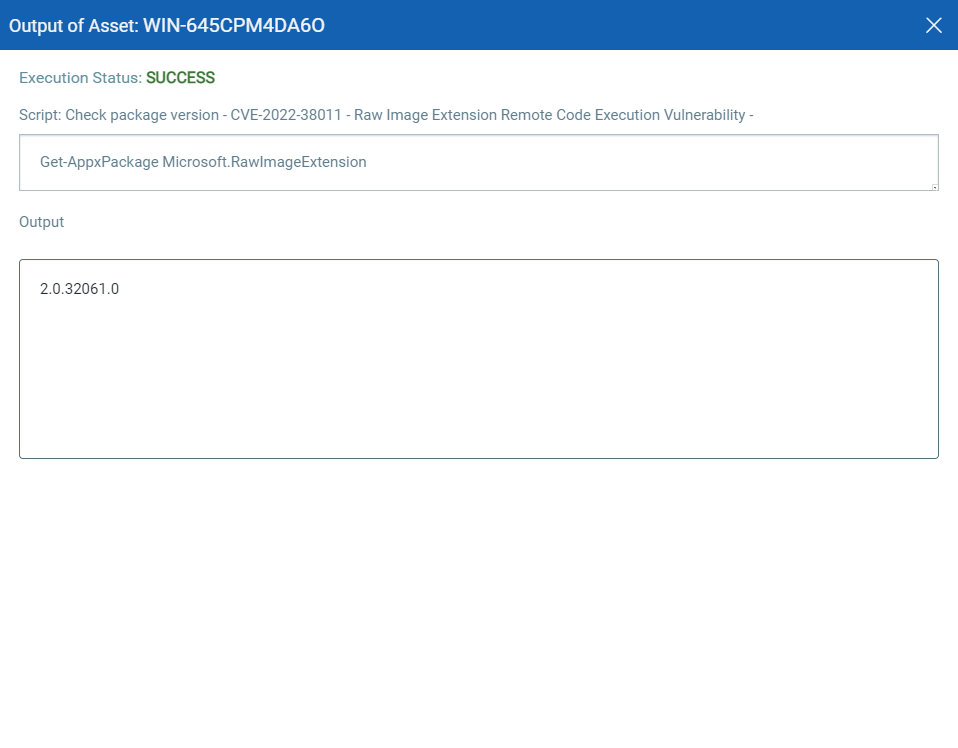
CVE-2022-38011 – Raw Image Extension Remote Code Execution Vulnerability
NOTE: For all supported versions of Windows 10 and Windows 11 operating systems the secure version is v2.0.32061.0 and later.
Script Details:
Script Output:
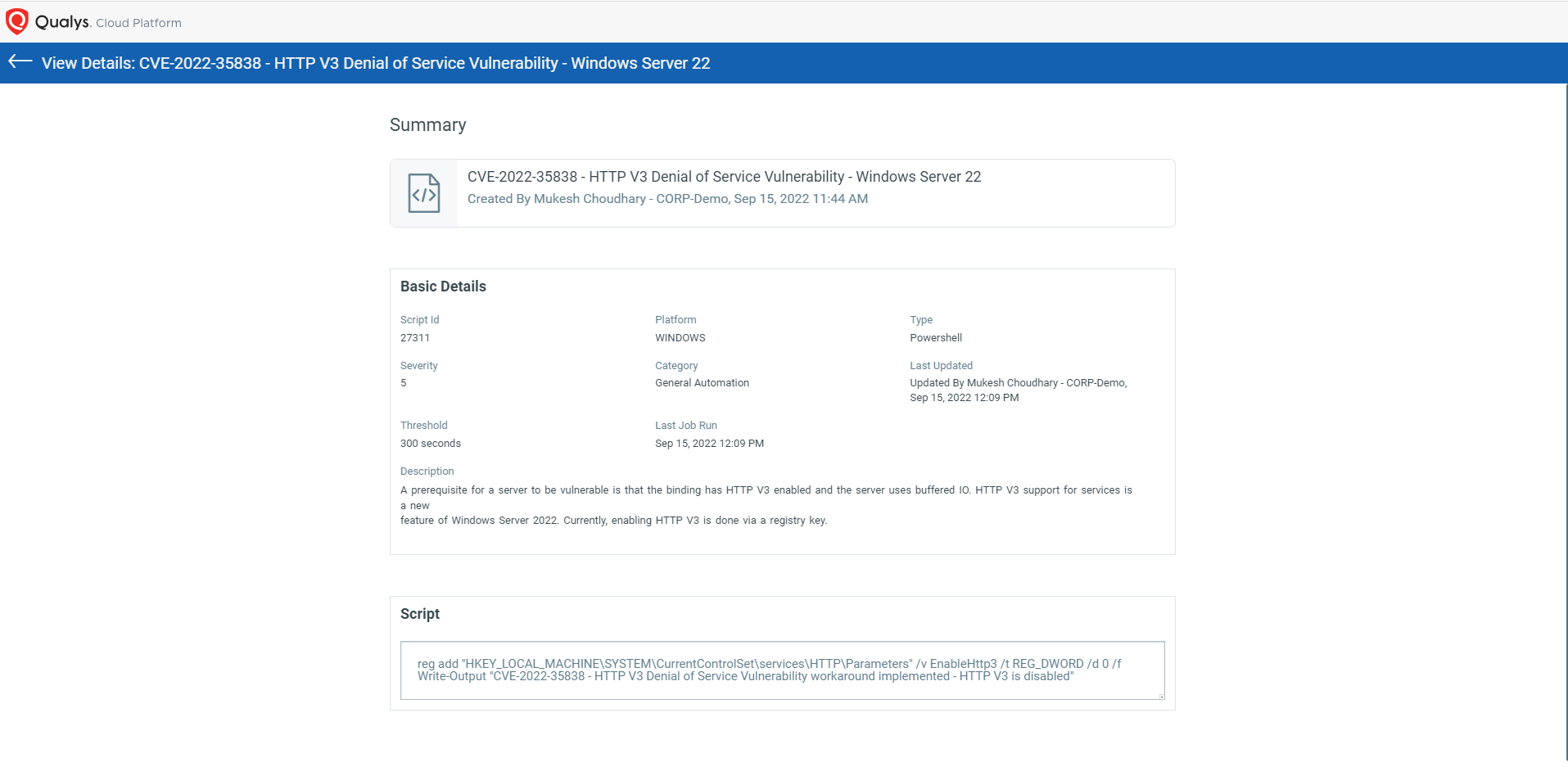
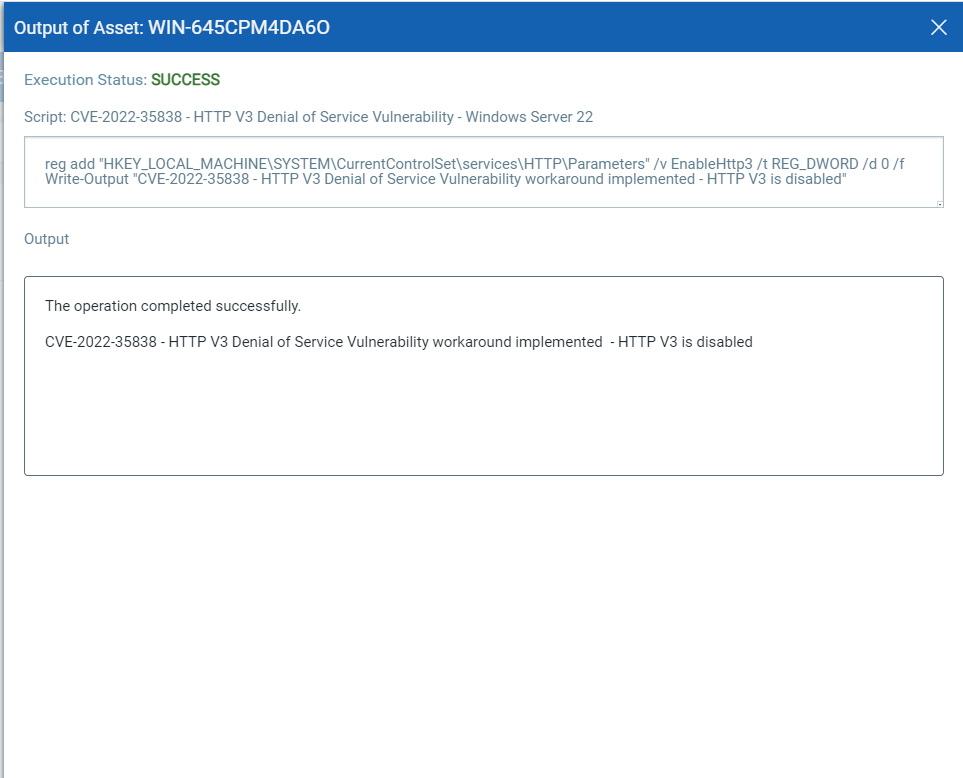
CVE-2022-35838 – HTTP V3 Denial of Service Vulnerability
NOTE: A prerequisite for a server to be vulnerable is that the binding has HTTP/3 enabled and the server uses buffered I/O. HTTP/3 support for services is a new feature of Windows Server 2022.
Script Details:
Script Output:
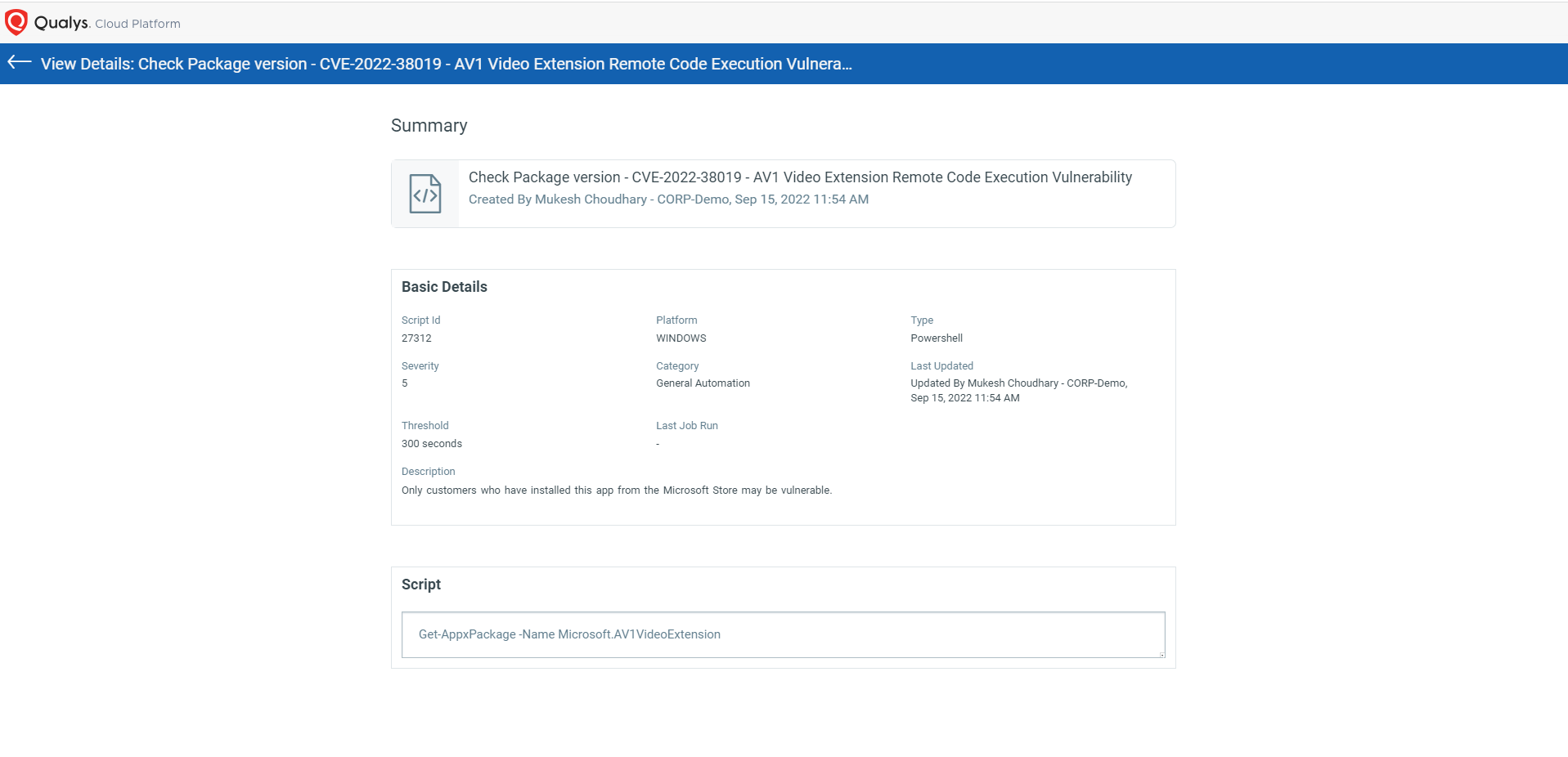
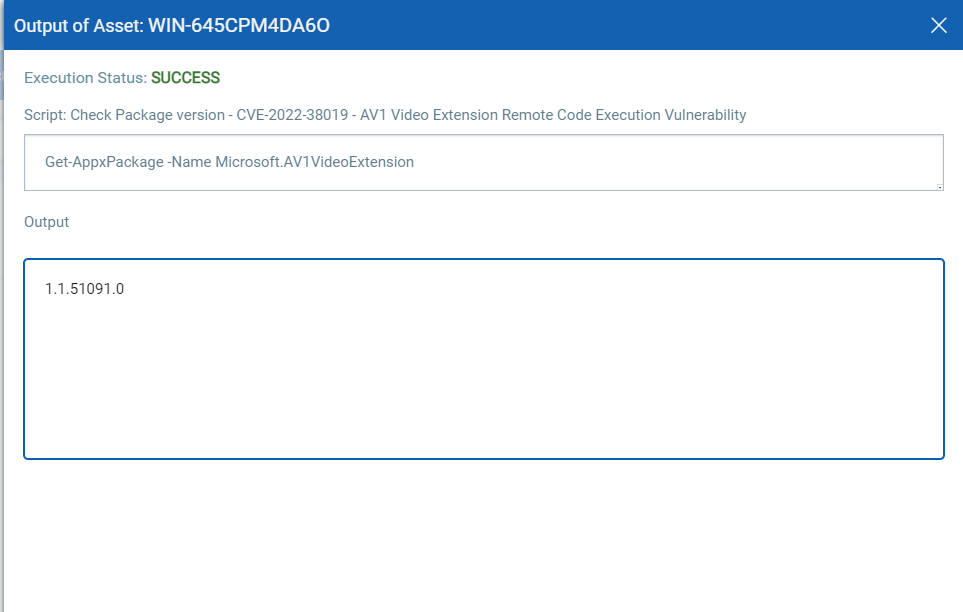
CVE-2022-38019 – AV1 Video Extension Remote Code Execution Vulnerability
NOTE: App package versions 1.1.51091.0 and later contain this update.
Script Details:
Script Output:
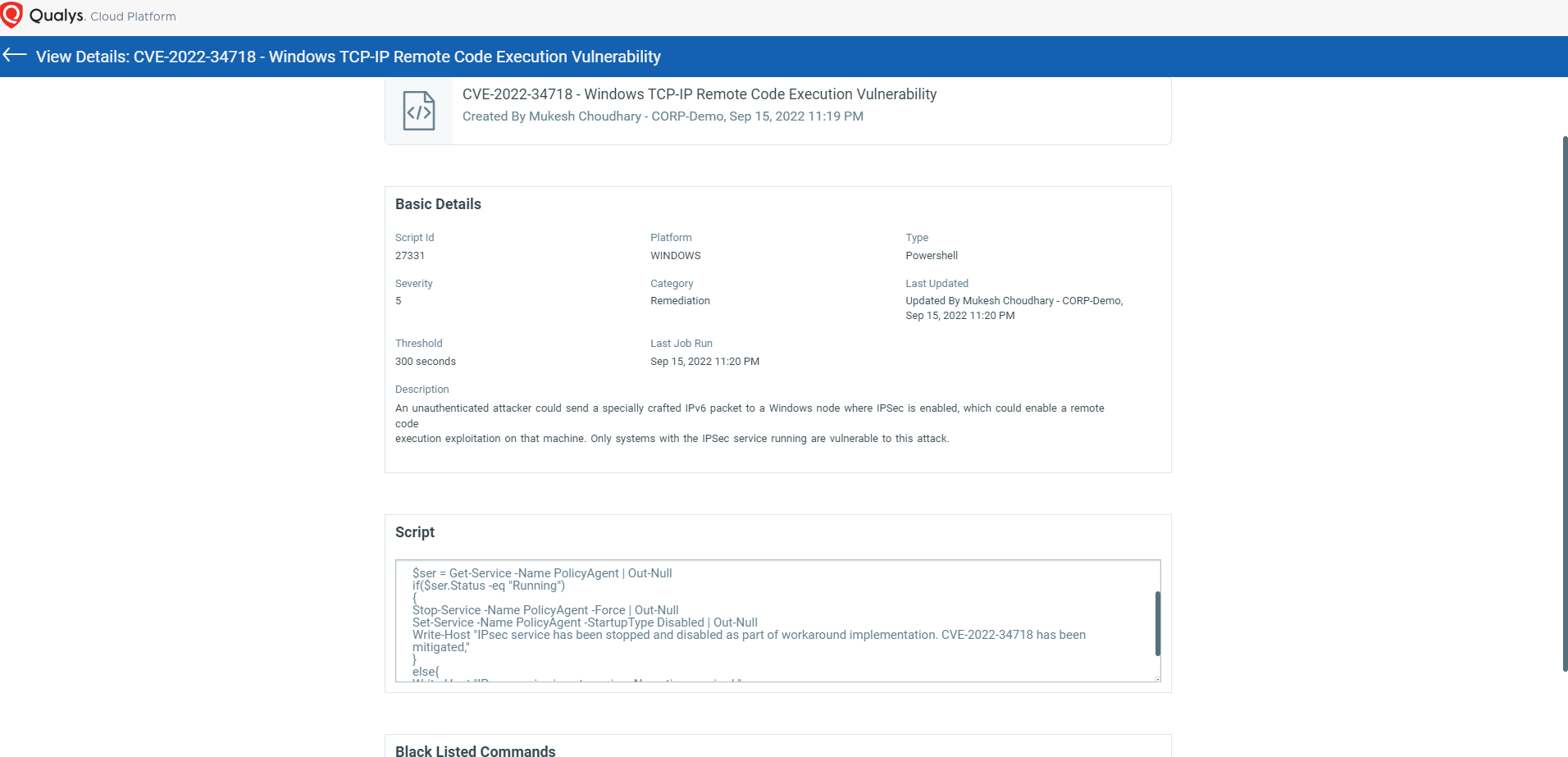
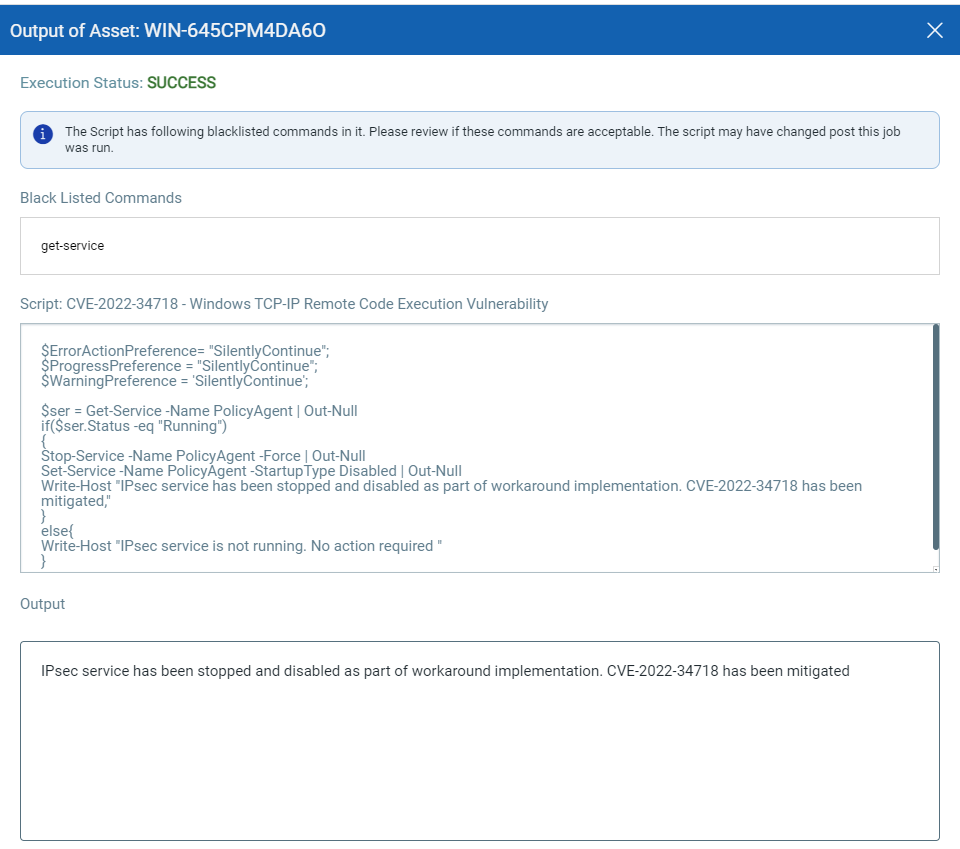
CVE-2022-34718 – Windows TCP/IP Remote Code Execution Vulnerability
An unauthenticated attacker could send a specially crafted IPv6 packet to a Windows node where IPSec is enabled, which could enable remote code execution exploitation on that machine.
NOTE: Only systems with the IPSec service running are vulnerable to this attack.
Script Details:
Script Output:
Visit the September 2022 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 110415, 110416, 377590, 91947, 91946, 91945, 91944, 91943, 91942, 91941, 91940, 91939, 91938, 91937 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide/releaseNote/2022-Sep
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-37969
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-23960
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-34718
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-34721
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-34722
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-35805
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-34700