3CX Desktop Application is currently facing ongoing multi-stage Supply Chain attacks targeted at the company’s customers. The hacker groups have used the trojanized Voice Over Internet Protocol (VOIP) desktop client to stage the attacks. The vulnerability has been termed “SmoothOperator.” The vulnerability has been assigned with CVE-2023-29059.
Post exploitation, attackers can spawn an interactive command shell and deploy second-stage payloads. The vulnerability affects the 3CX PBX phone system, which could allow an attacker to add an installer that communicates with various command-and-control (C2) servers.
3CXDesktopApp is a voice and video conferencing PBX phone system available on Windows, Linux, Android, and iOS. The system is used in automotive, food & beverage, hospitality, manufacturing, and other industries.
Description
A vulnerable 3CXDesktopApp application acts as a shellcode loader, executing the shellcode from heap memory. The shellcode loads a DLL removing the “MZ” at the start.
The ffmpeg.dll file contains an embedded URL that retrieves a malicious encoded .ico payload. The malicious loader (ffmpeg.dll) is used to queue up the payload. 3CX has provided ffmpeg.dll in its installation directory all along. 3CX has not provided any update regarding how the dll was modified and added along with the legitimate installer.
These DLL files are then used to execute the next stage of the attack.
The DLL files are used to download icon files from the GitHub repository. The ICO files are appended with a Base64 string at the end. The data is then decoded and results in downloading the final payload. The DLL appears to be a previously unidentified infostealer designed to interact with browser data.
The infostealer feature is implemented in the last stage, which includes acquiring system and browser information from Chrome, Edge, Brave, and Firefox browsers. For Firefox-based and Chrome-based browsers, this also entails accessing browsing history and information from the Locations and History tables.
Note: The GitHub repository hosting the malicious icons has been taken down.
Affected Versions
- 3CX Desktop Client for Windows version 18.12.407
- 3CX Desktop Client for Windows version 18.12.416
- 3CX Desktop Client for MacOS version 18.11.1213
- 3CX Desktop Client for MacOS version 18.12.402
- 3CX Desktop Client for MacOS version 18.12.407
- 3CX Desktop Client for MacOS version 18.12.416
Mitigation
Vendor has released an advisory stating, “Currently, we’re working on a new Windows App that does not have the issue. We’ve also decided to issue a new certificate for this app.”
The vendor has suggested that customers use an entirely web-based PWA app instead.
For more information, please refer to the 3CX Security Advisory.
Executing workaround using Qualys Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation (CAR) can be leveraged to remediate this vulnerability. You need to execute this uninstallation script provided by Qualys. This script checks for 3CX Desktop App’s vulnerable versions 18.12.407.0 and 18.12.416.0 for Windows. If any of the versions are installed on the system, it will uninstall it.
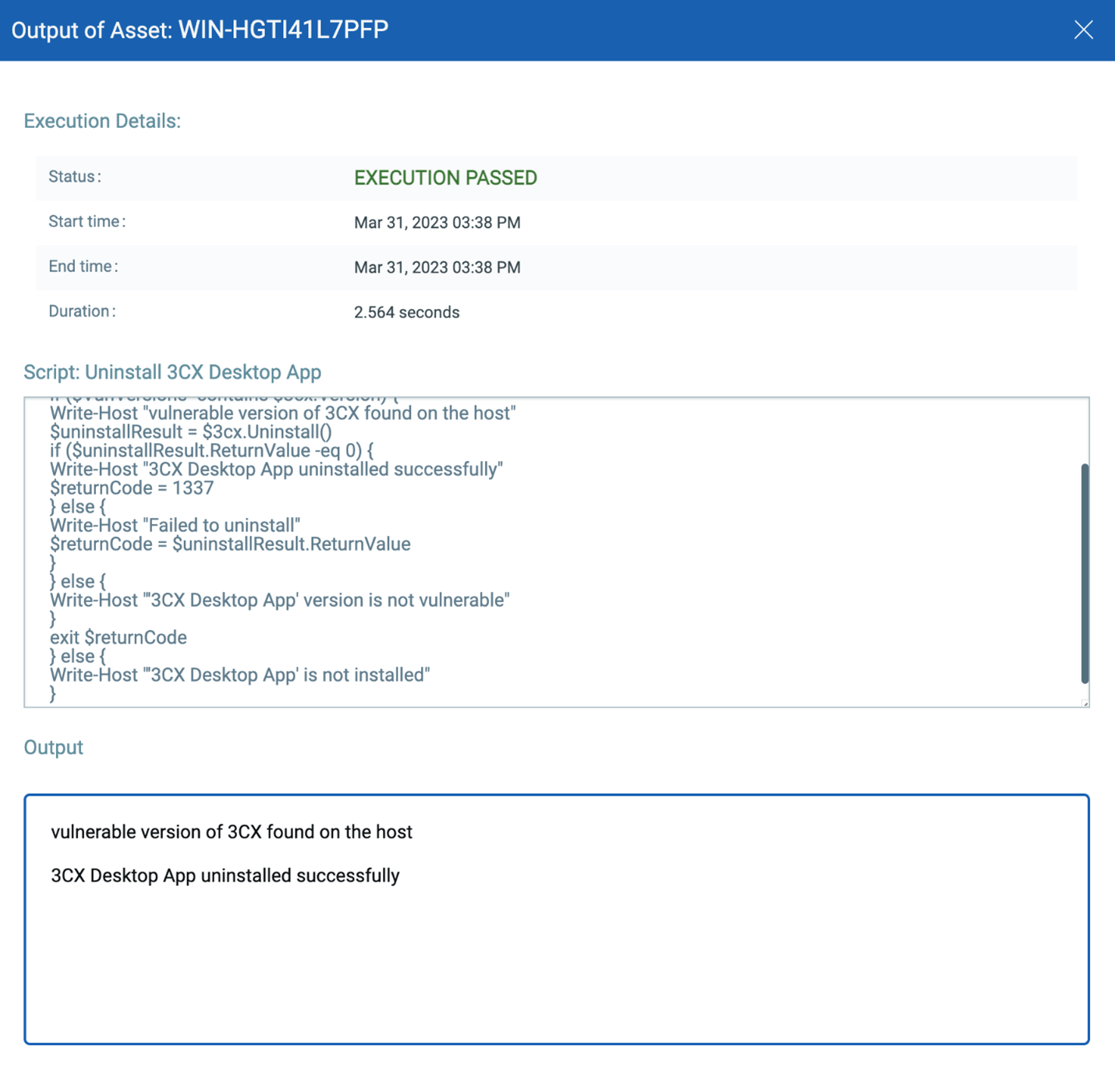 You can create dashboards for better visualization.
You can create dashboards for better visualization.
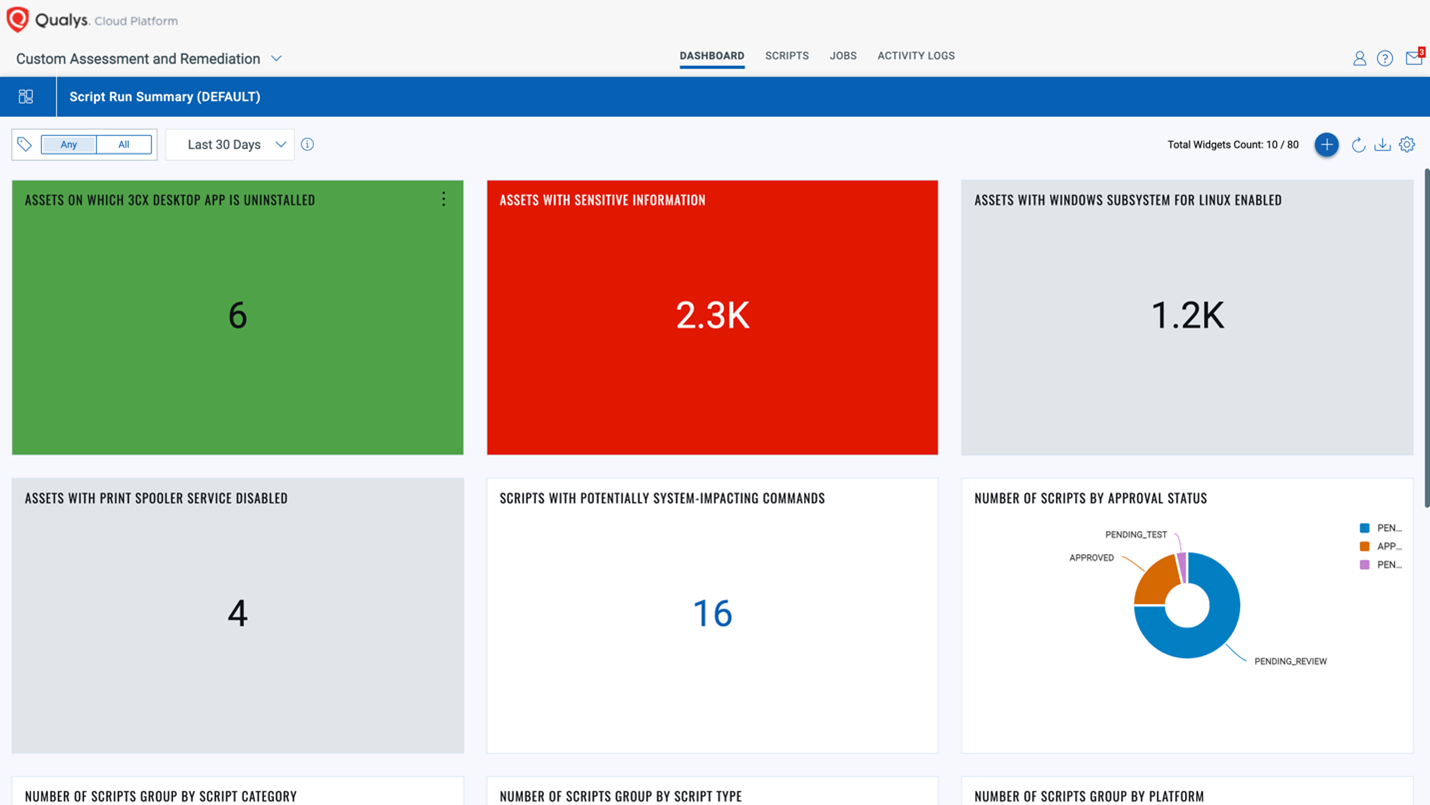
Qualys Detection
Qualys customers can scan their devices with QID 378327 to detect vulnerable assets. The QID checks for vulnerable versions of the 3CX Desktop Client by checking the file version of the 3CXDesktopApp.exe file.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.3cx.com/blog/news/desktopapp-security-alert/
https://news.sophos.com/en-us/2023/03/29/3cx-dll-sideloading-attack/
https://www.bleepingcomputer.com/news/security/hackers-compromise-3cx-desktop-app-in-a-supply-chain-attack/
https://www.sentinelone.com/blog/smoothoperator-ongoing-campaign-trojanizes-3cx-software-in-software-supply-chain-attack/