Cacti, a widely used operational monitoring tool, is vulnerable to a SQL injection flaw that may allow an attacker to perform code execution on successful exploitation. CVE-2023-39361 has a critical severity rating with a CVSS score of 9.8. The vulnerability may allow an unauthenticated user to execute arbitrary code on a Cacti server if a specific data source was selected for any monitored device.
Cacti is a network monitoring and graphing tool that provides RRDTool’s data storage and graphing functionality. This open-source, web-based tool offers robust and adaptable operational monitoring and fault management frameworks for users worldwide.
As per Shodan, there are more than 3000 internet-exposed Cacti servers at the time of writing.
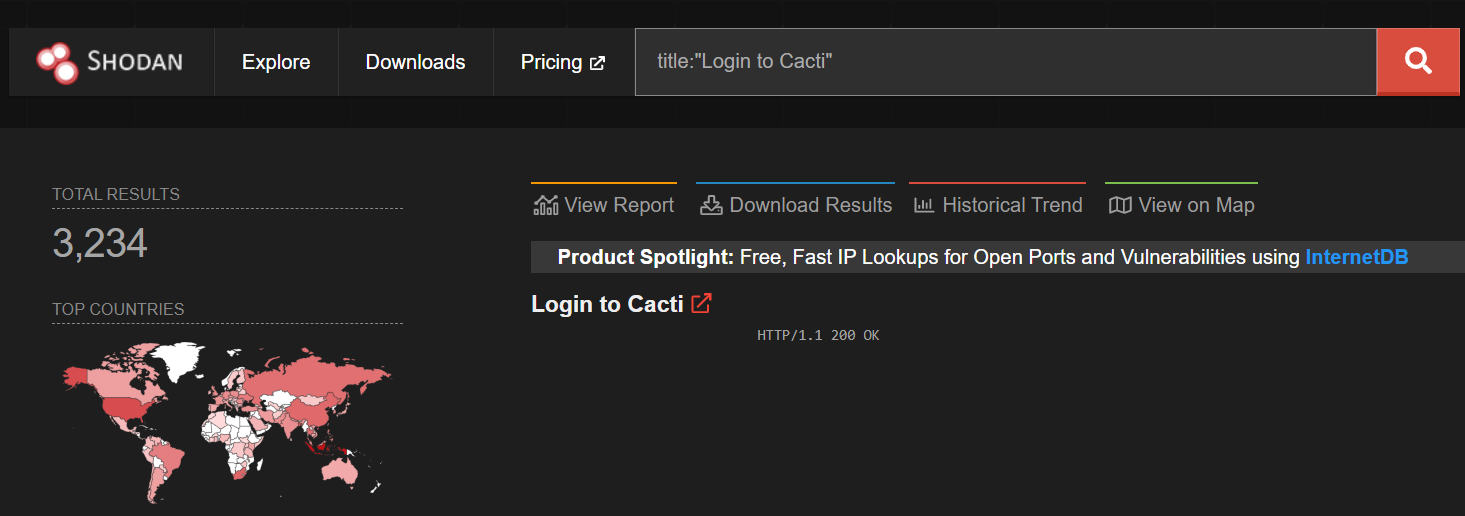
Image Source: Shodan
Vulnerability Description
The vulnerability exists in the graph_view.php file. The guest users can access graph_view.php without authentication by default, which results in the SQL Injection vulnerability when used in an enabled condition. An attacker may exploit this vulnerability to perform remote code execution or usurpation of administrative rights.
The grow_right_pane_tree function contains the vulnerability that is invoked from the graph_view.php file. The user input is validated through the html_validate_tree_vars function in the tree_content case. Following this, the grow_right_pane_tree function is invoked if the tree_id parameter is greater than 0.
graph_view.php
switch (get_nfilter_request_var('action')) { // ... case 'tree_content': html_validate_tree_vars(); // ... if ($tree_id > 0) { if (!is_tree_allowed($tree_id)) { header('Location: permission_denied.php'); exit; } grow_right_pane_tree($tree_id, $node_id, $hgdata); }
The user input parameter rfilter is used directly by the grow_right_pane_tree function in the WHERE clause with RLIKE. The html_validate_tree_vars function of graph_view.php validates the rfilter parameter, but this validation simply verifies that rfilter is valid as a regular expression, not guaranteeing that it does not contain SQL code.
lib/html_tree.php
function grow_right_pane_tree($tree_id, $leaf_id, $host_group_data) { // ... if (($leaf_type == 'header') || (empty($leaf_id))) { $sql_where = ''; if (get_request_var('rfilter') != '') { $sql_where .= ' (gtg.title_cache RLIKE "' . get_request_var('rfilter') . '" OR gtg.title RLIKE "' . get_request_var('rfilter') . '")'; } // ... $graph_list = get_allowed_tree_header_graphs($tree_id, $leaf_id, $sql_where); }
The Qualys Threat Research Unit verified the SQL Injection Vulnerability by triggering a time delay.
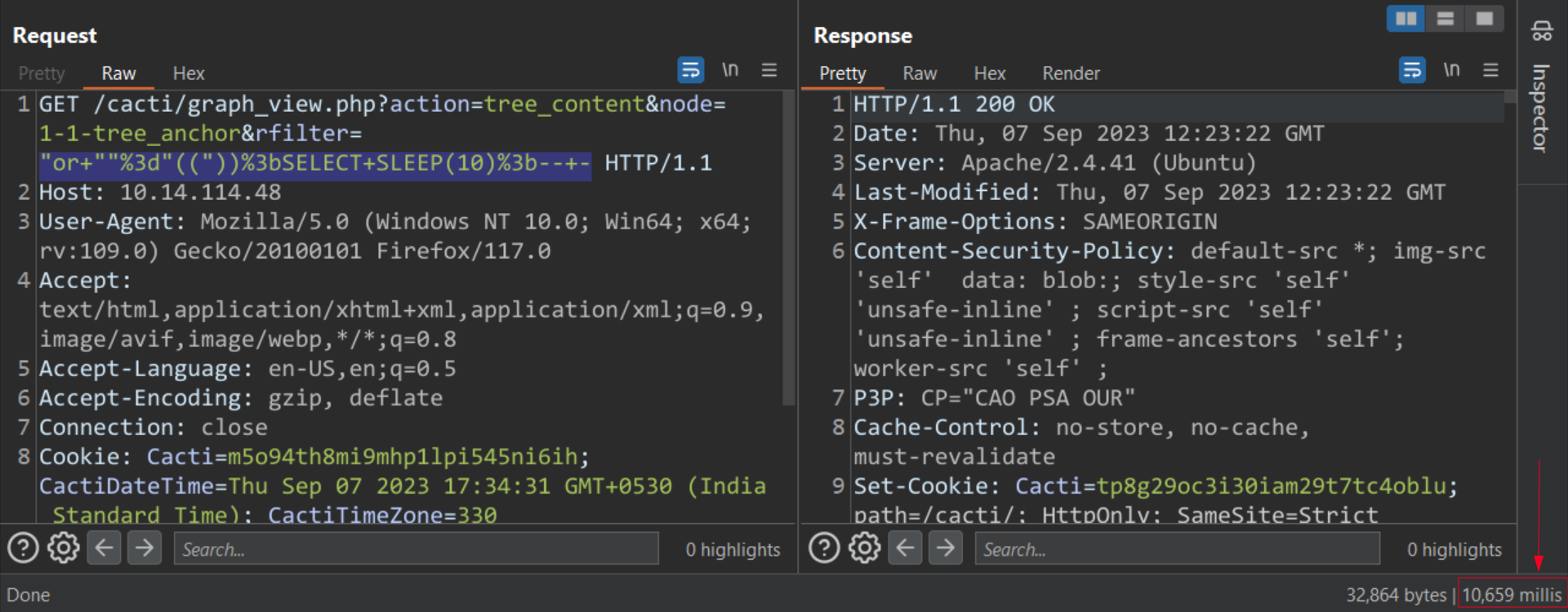
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
The vulnerability affects Cacti v1.2.24.
Mitigation
Cacti has recommended its customers to upgrade to Cacti 1.2.25, 1.3.0, or later to patch the vulnerability.
For more information, please refer to the Security Advisory (GHSA-6r43-q2fw-5wrg).
Qualys Detection
Qualys customers can scan their devices with QID 730897 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://github.com/Cacti/cacti/security/advisories/GHSA-6r43-q2fw-5wrg