Cisco is aware of the active exploitation of a privilege escalation vulnerability in Cisco IOS XE Software Web UI. Tracked as CVE-2023-20198, the vulnerability may allow a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access. An attacker may use the compromised account to gain control of the affected system.
CISA has also acknowledged the exploitation of the vulnerability by adding it to its Known Exploited Vulnerabilities Catalog, requesting users to patch it before October 20, 2023.
CISA has also added CVE-2023-20273 to its Known Exploited Vulnerabilities Catalog, requesting users to patch it before October 27, 2023.
Cisco IOS XE is an open and flexible operating system used for enterprise wired and wireless access, aggregation, core, and WAN. The software reduces business and network complexity. The software provides enhanced platform integrity and security.
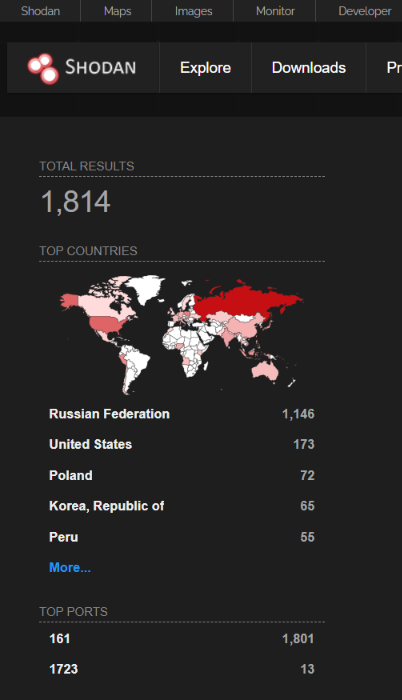
As per Shodan, there are more than 1800 internet-exposed targets at the time of writing.
NOTE: Cisco updated the advisory on October 22, 2023, with fixed versions and another exploited vulnerability (CVE-2023-20273) information.
Cisco has mentioned in its advisory that attackers may exploit another component of the web UI feature. The vulnerabilities (CVE-2023-20198 and CVE-2023-20273) can be exploited in a chain attack. An attacker may first exploit CVE-2023-20198 to gain initial access and log in with normal user access. CVE-2023-20273 may allow an attacker to exploit another component of the web UI feature. Successful exploitation of the vulnerability would allow an attacker to the new local user to elevate privilege to root and write the implant to the file system.
Vulnerability Description
The web UI is an embedded GUI-based system-management tool that allows the system provision, simplifies system deployment and manageability, and enhances the user experience. The tool comes with the default image. It does not require enabling or installing any license on the system. The web UI can also build configurations, monitor, and troubleshoot the system without CLI expertise.
It is essential for the user to not expose the web UI and management services to the internet or untrusted networks.
Prerequisites
This vulnerability affects Cisco IOS XE Software if the web UI feature is enabled. The web UI feature is enabled through the ip http server or ip http secure-server commands.
Determine the HTTP Server Configuration
To determine whether the HTTP Server feature is enabled for a system, the customer can do the following:
- Log in to the system
- Use the show running-config | include ip http server|secure|active command in the CLI.
The presence of the ip http server or the ip http secure-server command in the global configuration will confirm whether the HTTP Server feature is enabled for the system.
Note: The presence of either command or both commands in the system configuration indicates that the web UI feature is enabled.
If the ip http server command is present and the configuration contains ip http active-session-modules none, the vulnerability is not exploitable over HTTP.
If the ip http secure-server command is present and the configuration contains ip http secure-active-session-modules none, the vulnerability is not exploitable over HTTPS.
Indicators of Compromise
Here are the checks that can be performed to determine whether a system may have been compromised:
- Check the system logs for the presence of any of the following log messages where the user could be cisco_tac_admin, cisco_support, or any configured local user that is unknown to the network administrator:
%SYS-5-CONFIG_P: Configured programmatically by process SEP_webui_wsma_http from console as user on line
%SEC_LOGIN-5-WEBLOGIN_SUCCESS: Login Success [user: user] [Source: source_IP_address] at 03:42:13 UTC Wed Oct 11 2023
Note: The %SYS-5-CONFIG_P message will be present for each instance a user has accessed the web UI. Customers should look for new or unknown usernames in the message.
- Check the system logs for the following message where the filename is unknown and does not correlate with an expected file installation action:
%WEBUI-6-INSTALL_OPERATION_INFO: User: username, Install Operation: ADD filenam
Cisco Talos has provided the following command to check for the presence of the implant, where systemip is the IP address of the system to check. The following command should be issued from a workstation with access to the system in question:
curl -k -X POST “https://systemip/webui/logoutconfirm.html?logon_hash=1“
If the request returns a hexadecimal string, the implant is present.
Note: If the system is configured for HTTP access only, use the HTTP scheme in the command example.
The following Snort rule IDs are also available to detect exploitation:
- 3:50118:2 – can alert for initial implant injection
- 3:62527:1 – can alert for implant interaction
- 3:62528:1 – can alert for implant interaction
- 3:62529:1 – can alert for implant interaction
Affected Versions
The following Cisco IOS XE Software versions are affected by the vulnerabilities:
- 17.9
- 17.6
- 17.3
- 16.12 (Catalyst 3650 and 3850 only)
Mitigation
Customers must upgrade to the following Cisco IOS XE Software versions to patch the vulnerabilities:
- 17.9.4a
- 17.6.6a
- 17.3.8a
- 16.12.10a
NOTE: The availability of the Cisco IOS XE Software versions 17.6.6a, 17.3.8a, and 16.12.10a are yet to be announced.
Customers can refer to the Cisco Security Advisory (cisco-sa-iosxe-webui-privesc-j22SaA4z) for information about the vulnerability.
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now. These security controls are not recommended by any industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best-practice existing in a default state that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been published to support the evaluation of recommended mitigations:
- 26885 Status of Active Session Modules and HTTP Server
- 26886 Status of Secure Active Session Modules and HTTPS Server
Qualys Detection
Qualys customers can scan their devices with QID 317376 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.