Ivanti released an advisory to address a critical severity vulnerability impacting Ivanti Virtual Traffic Manager. Tracked as CVE-2024-7593, the vulnerability has a CVSS score of 9.8. A remote, unauthenticated attacker may bypass authentication and create administrative users on successful exploitation. The vulnerability originates from an incorrect implementation of an authentication algorithm.
Ivanti mentioned in the advisory that they were unaware of any exploitation of the vulnerability at the time of disclosure. The advisory says, “However, a Proof of Concept is publicly available, and we urge customers to upgrade to the latest patched version.”
CISA acknowledged the active exploitation of CVE-2024-7593 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before October 15, 2024.
Ivanti Virtual Traffic Manager is a software-based Application Delivery Controller (ADC) designed to deliver a faster, high-performance user experience with more reliable access to public websites and enterprise applications, whether they run in public.
Affected Versions
- Ivanti Virtual Traffic Manager 22.2
- Ivanti Virtual Traffic Manager 22.3
- Ivanti Virtual Traffic Manager 22.3R2
- Ivanti Virtual Traffic Manager 22.5R1
- Ivanti Virtual Traffic Manager 22.6R1
- Ivanti Virtual Traffic Manager 22.7R1
Mitigation
- Ivanti Virtual Traffic Manager 22.2R1 (released)
- Ivanti Virtual Traffic Manager 22.3R3 (releasing next week)
- Ivanti Virtual Traffic Manager 22.3R3 (releasing next week)
- Ivanti Virtual Traffic Manager 22.5R2 (releasing next week)
- Ivanti Virtual Traffic Manager 22.6R2 (releasing next week)
- Ivanti Virtual Traffic Manager 22.7R2 (released)
Please refer to the Ivanti Security Advisory for more information.
Workaround
This vulnerability is accessible over the management interface. To limit the exploitability of this vulnerability, Ivanti advised limiting Admin Access to the Management Interface internal of the network through the private/corporate network.
- On the VTM server, navigate to System > Security, then click the drop-down for the page’s Management IP Address and Admin Server Port section.
- In the bindip drop-down, select the Management Interface IP Address. Customers can also use the setting directly above the “bindip” setting to restrict access to trusted IP addresses, restricting who can access the interface.
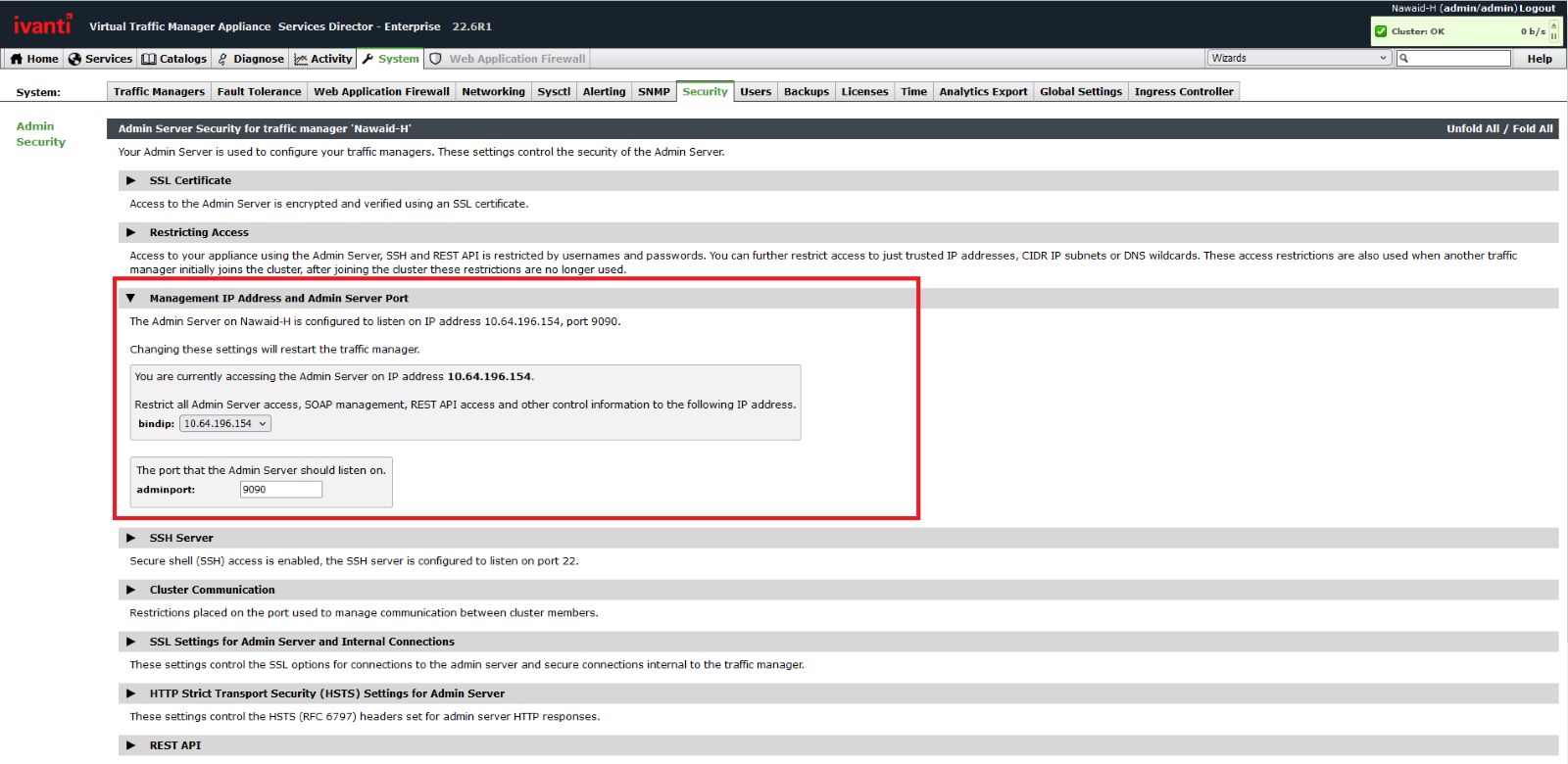 Image Source: Ivanti Security Advisory
Image Source: Ivanti Security Advisory
Qualys Detection
Qualys customers can scan their devices with QIDs 731703 and 731741 to detect vulnerable assets. This QID checks for vulnerable Ivanti Virtual Traffic Manager (vTM) versions by sending an HTTP GET request to the /apps/zxtm/login.cgi endpoint.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.