Zabbix server is vulnerable to a critical severity flaw tracked as CVE-2024-42327. The vulnerability has a CVSS score of 9.9. Successful exploitation of the vulnerability may allow attackers to escalate privileges and gain complete control of vulnerable Zabbix servers.
Márk Rákóczi discovered and reported the vulnerability through the HackerOne bug bounty platform.
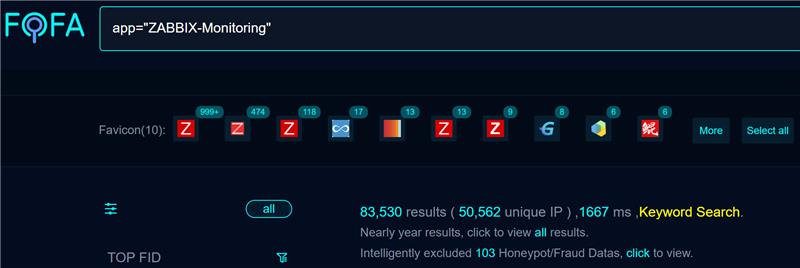
A quick search revealed more than 83,000 targets on Fofa at the time of writing.
Zabbix is an open-source monitoring tool that collects, stores, manages, and analyzes information from IT infrastructure. Zabbix can monitor various IT components, including networks, servers, virtual machines (VMs), and cloud services. Zabbix also offers reporting and data visualization features that can be accessed through a web-based frontend.
Vulnerability Details
The vulnerability exists in the user.get API endpoint that can be exploited by a non-admin user with API access, including accounts with the default User role. The SQL injection flaw exists in the CUser class in the addRelatedObjects function. This function is being called from the CUser.get function, which is available to users with API access. An attacker may inject SQL commands by manipulating API calls. Successful exploitation of the vulnerability may allow an attacker to gain unauthorized access and control.
Affected Versions
- 6.0.0 – 6.0.31
- 6.4.0 – 6.4.16
- 7.0.0
Mitigation
Zabbix released the following versions to patch the vulnerability:
- 6.0.32rc1
- 6.4.17rc1
- 7.0.1rc1
For more information, please refer to the Zabbix Security Advisory (ZBX-25623).
Qualys Detection
Qualys customers can scan their devices with QID 382447 to detect vulnerable assets and QID 152460 to detect vulnerable web applications.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://support.zabbix.com/browse/ZBX-25623