Closing out 2024, Microsoft’s December Patch Tuesday highlights the importance of year-end maintenance with updates tackling critical vulnerabilities. As cyber threats remain persistent, these patches serve as a vital reminder of the ongoing need for robust system security.
Microsoft Patch Tuesday, December 2024 edition addressed 73 vulnerabilities, including 16 critical and 54 important severity vulnerabilities. In this month’s updates, Microsoft has addressed one zero-day vulnerability known to be exploited in the wild.
Microsoft has addressed two vulnerabilities in Microsoft Edge (Chromium-based) in this month’s updates. Microsoft Patch Tuesday, December edition includes updates for vulnerabilities in Microsoft Defender for Endpoint, Windows Hyper-V, Windows Cloud Files Mini Filter Driver, Windows Remote Desktop, Windows Message Queuing, Windows Mobile Broadband, Windows Kernel-Mode Drivers, and more.
Microsoft has fixed several flaws in multiple software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, and Remote Code Execution (RCE).
The December 2024 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 1 | Important: 1 |
| Denial of Service Vulnerability | 5 | Important: 5 |
| Elevation of Privilege Vulnerability | 27 | Important: 27 |
| Information Disclosure Vulnerability | 7 | Important: 7 |
| Remote Code Execution Vulnerability | 30 | Critical: 16 Important: 14 |
Zero-day Vulnerabilities Patched in December Patch Tuesday Edition
CVE-2024-49138: Windows Common Log File System Driver Elevation of Privilege Vulnerability
The Common Log File System (CLFS) is a general-purpose logging service used by software clients running in user or kernel mode. CLFS can be used for data management, database systems, messaging, Online Transactional Processing (OLTP) systems, and other kinds of transactional systems.
Upon successful exploitation, an attacker could gain SYSTEM privileges.
CISA added the CVE-2024-49138 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before December 31, 2024.
Critical Severity Vulnerabilities Patched in December Patch Tuesday Edition
CVE-2024-49117: Windows Hyper-V Remote Code Execution Vulnerability
Windows Hyper-V is a Microsoft virtualization technology that allows users to create and run Virtual Machines (VMs) on a physical host.
An authenticated attacker on a guest VM must send specially crafted file operation requests to hardware resources on the VM to exploit the vulnerability. Upon successful exploitation, an attacker may execute a cross-VM attack, compromising multiple virtual machines and expanding the attack’s impact beyond the initially targeted VM.
CVE-2024-49124: Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Vulnerability
The Lightweight Directory Access Protocol (LDAP) operates a layer above the TCP/IP stack. The directory service protocol helps connect, browse, and edit online directories. The LDAP directory service is based on a client-server model that enables access to an existing directory. LDAP stores data in the directory and authenticates users to access the directory.
An unauthenticated attacker must win a race condition and send a specially crafted request to a vulnerable server to exploit the vulnerability. Successful exploitation of the vulnerability may allow an attacker to execute code in the context of the SYSTEM account.
CVE-2024-49126: Windows Local Security Authority Subsystem Service (LSASS) Remote Code Execution Vulnerability
Local Security Authority Subsystem Service (LSASS) is a process in Microsoft Windows operating systems responsible for enforcing the security policy on the system. It verifies users logging on to a Windows computer or server, handles password changes, and creates access tokens.
An unauthenticated attacker must win a race condition to exploit the vulnerability. Successful exploitation of the vulnerability may result in remote code execution in the context of the server’s account through a network call.
CVE-2024-49122 & CVE-2024-49118: Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability
Message Queuing (MSMQ) is a protocol developed by Microsoft to ensure reliable communication between Windows computers across different networks, even when a host is temporarily not connected (by maintaining a message queue of undelivered messages).
To exploit this vulnerability, an attacker must send a malicious MSMQ packet to an MSMQ server. On successful exploitation, an attacker may perform remote code execution on the server side.
CVE-2024-49112: Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
An unauthenticated attacker may exploit the vulnerability by sending a specially crafted set of LDAP calls. Upon successful exploitation an attacker may execute arbitrary code within the context of the LDAP service.
CVE-2024-49127: Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
An unauthenticated attacker may send a specially crafted request to a vulnerable server. Successful exploitation of the vulnerability may result in remote code execution in the context of the SYSTEM account.
CVE-2024-49106, CVE-2024-49108, CVE-2024-49115, CVE-2024-49116, CVE-2024-49119, CVE-2024-49120, CVE-2024-49123, CVE-2024-49128, & CVE-2024-49132: Windows Remote Desktop Services Remote Code Execution Vulnerability
Windows Remote Desktop Services (RDS) licensing, also known as Remote Desktop Protocol (RDP) licensing, is a Windows component allowing users to control a remote computer over a network connection. RDS licensing is important when setting up RDS environments, and the Remote Desktop License Server is a critical element of this process.
An attacker may exploit the vulnerability by connecting to a system with the Remote Desktop Gateway role. An attacker could trigger the race condition to create a use-after-free scenario and perform remote code execution.
Other Microsoft Vulnerability Highlights
- CVE-2024-49070 is a remote code execution vulnerability in Microsoft SharePoint. Successful exploitation of the vulnerability may lead to remote code execution.
- CVE-2024-49093 is an elevation of privilege vulnerability in Windows Resilient File System (ReFS). Upon successful exploitation, an attacker may gain SYSTEM privileges.
- CVE-2024-49114 is an elevation of privilege vulnerability in Windows Cloud Files Mini Filter Driver. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-49088 & CVE-2024-49090 are elevation of privilege vulnerabilities in Windows Cloud Files Mini Filter Driver. Upon successful exploitation, an attacker may gain SYSTEM privileges.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, System Center Operations Manager, Microsoft Office, Microsoft Edge (Chromium-based), Microsoft Office SharePoint, GitHub, Microsoft Office Word, Microsoft Office Excel, Windows Task Scheduler, Windows Remote Desktop Services, Windows Virtualization-Based Security (VBS) Enclave, Microsoft Office Publisher, Windows IP Routing Management Snapin, Windows Wireless Wide Area Network Service, Windows File Explorer, Windows Kernel, Windows Routing and Remote Access Service (RRAS), Windows Common Log File System Driver, DNS Server, Windows Resilient File System (ReFS), Windows PrintWorkflowUserSvc, Remote Desktop Client, WmsRepair Service, Windows LDAP – Lightweight Directory Access Protocol, Windows Local Security Authority Subsystem Service (LSASS), and Microsoft Office Access.
Mitigative Controls for CVE-2024-49112
Microsoft suggests that ensuring domain controllers are not configured to access the internet or deny RPC inbound traffic from untrusted networks. Example commands that customers can run on domain controllers are:
Block All Outbound:
netsh advfirewall firewall add rule name="Block All Outbound" dir=out action=block
Block RPC Inbound:
netsh advfirewall firewall add rule name="Block RPC Inbound" dir=in action=block protocol=TCP localport=135
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: (qid:110482 or qid:110483 or qid: 92197 or qid: 92198 or qid: 92199 or qid: 92200)
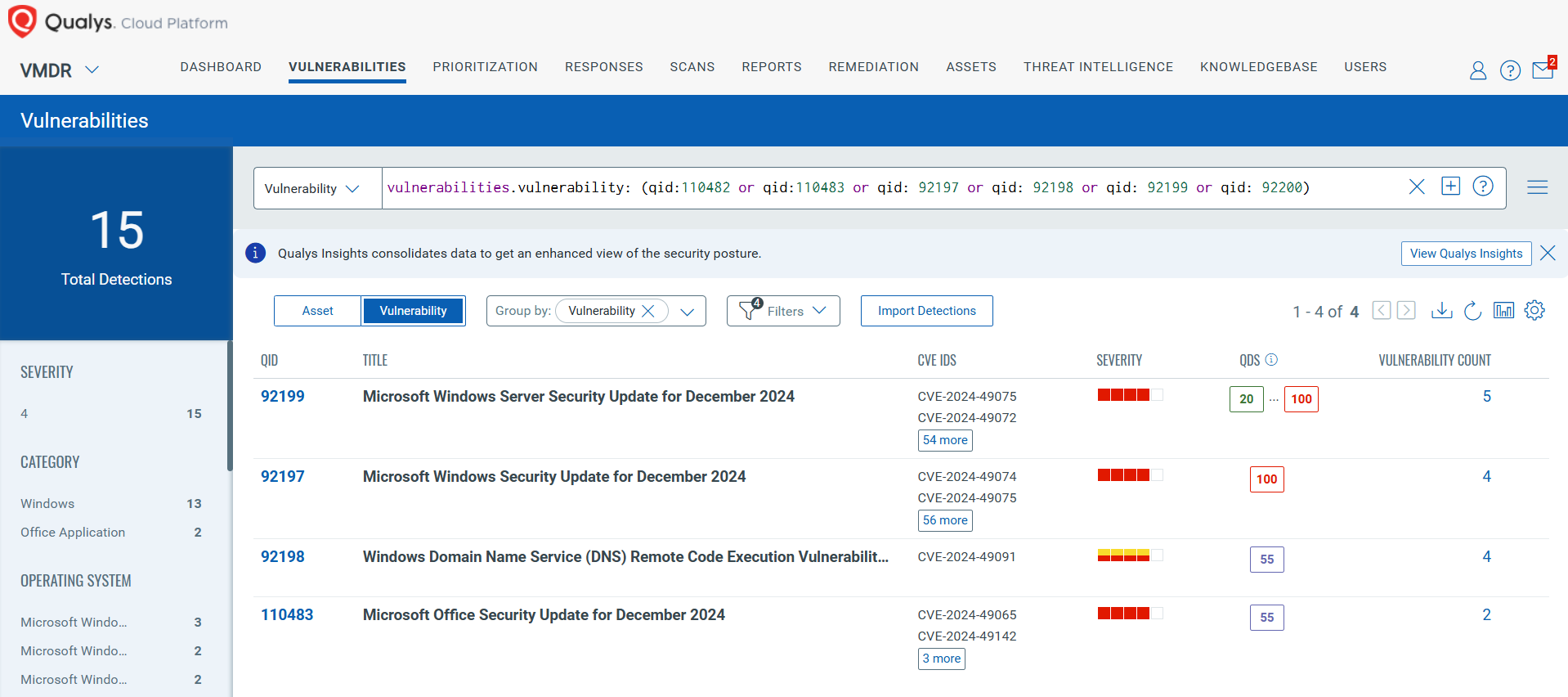
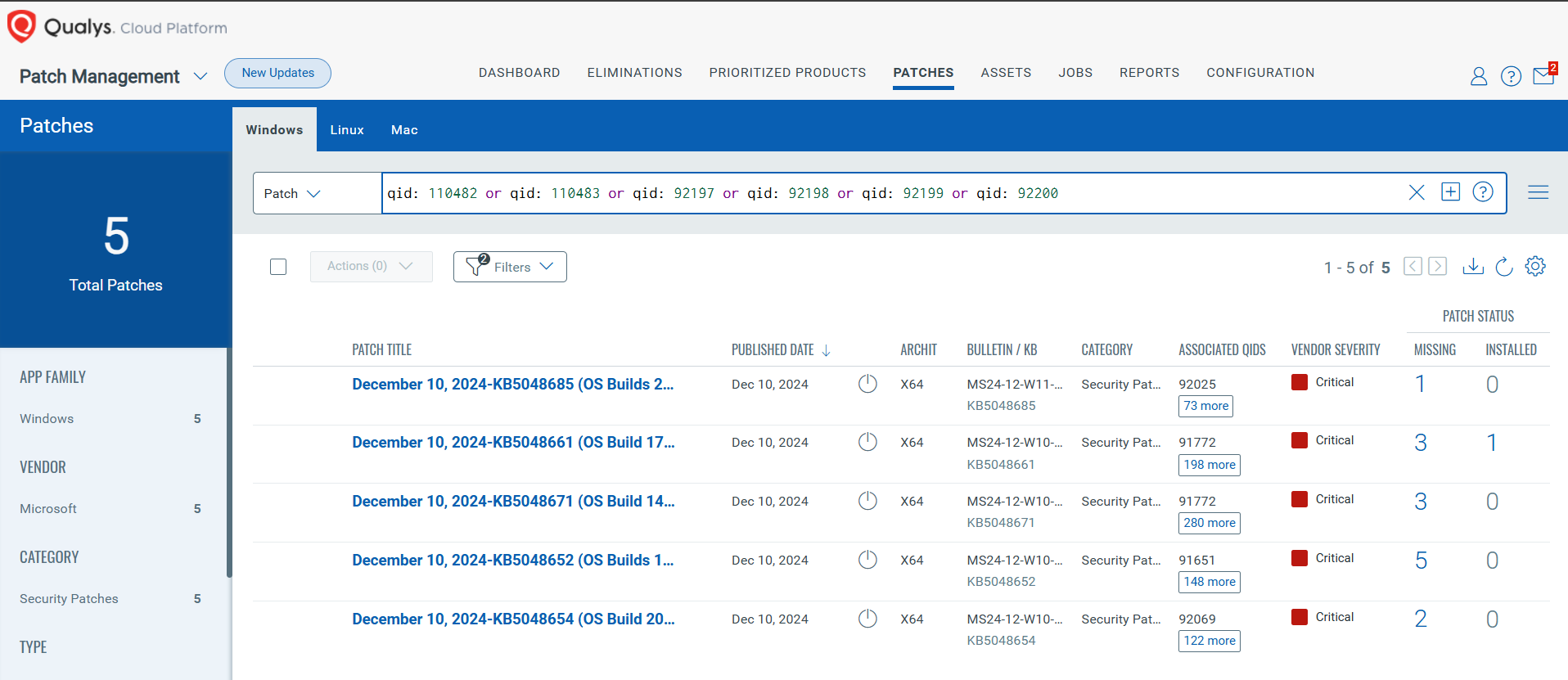
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid: 110482 or qid: 110483 or qid: 92197 or qid: 92198 or qid: 92199 or qid: 92200 )
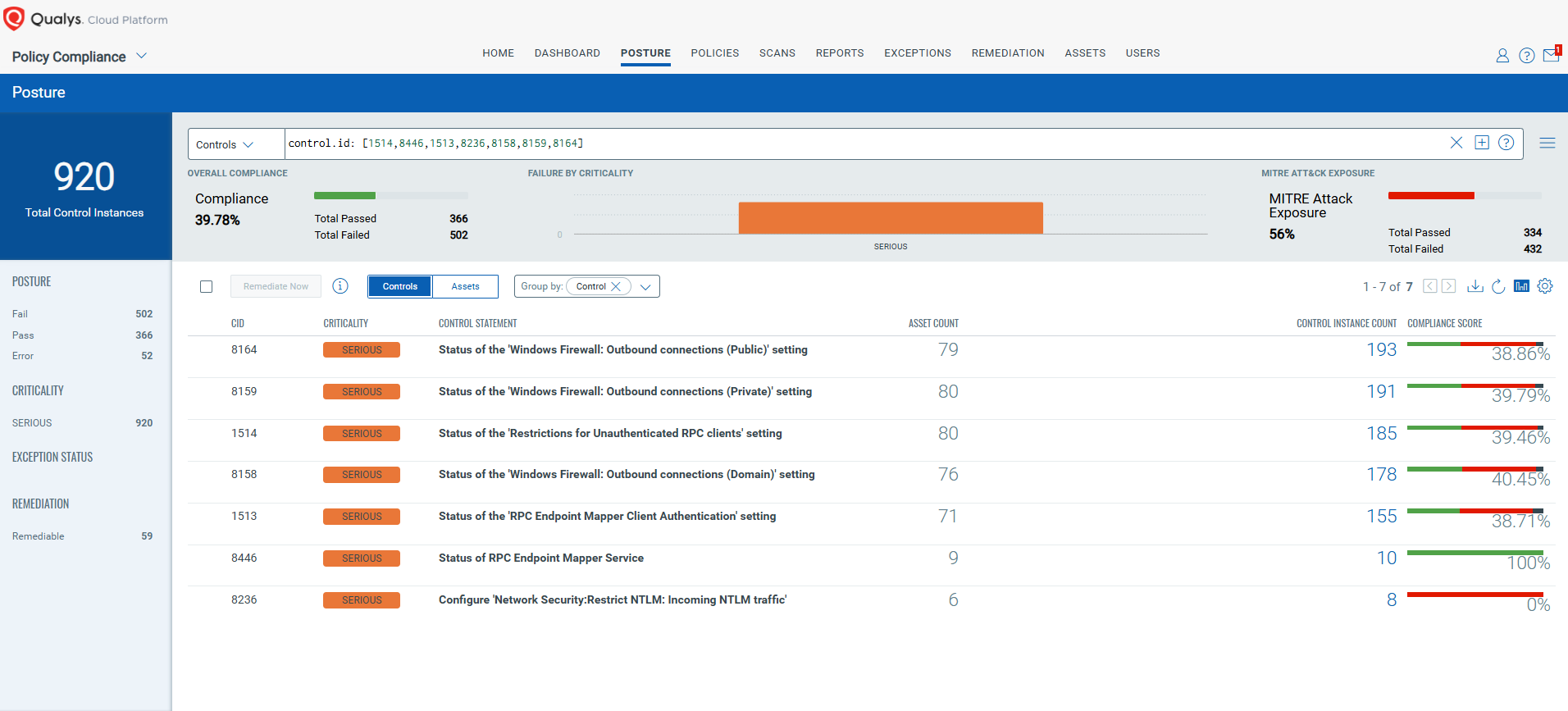
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/Patch) cannot be done now. These security controls are not recommended by industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best-practice existing in a default state that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2024-49112: Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
This vulnerability has a CVSS: 3.1 9.8 / 8.5 Policy Compliance Control IDs (CIDs):
- 1514 Status of the ‘Restrictions for Unauthenticated RPC clients’ setting
- 8446 Status of RPC Endpoint Mapper Service
- 1513 Status of the ‘RPC Endpoint Mapper Client Authentication’ setting
- 8236 Configure ‘Network Security:Restrict NTLM: Incoming NTLM traffic’
- 8158 Status of the ‘Windows Firewall: Outbound connections (Domain)’ setting
- 8159 Status of the ‘Windows Firewall: Outbound connections (Private)’ setting
- 8164 Status of the ‘Windows Firewall: Outbound connections (Public)’ setting
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [1514,8446,1513,8236,8158,8159,8164]
Visit the December 2024 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 110482, 110483, 92197, 92198, 92199, and 92200 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide
https://msrc.microsoft.com/update-guide/releaseNote/2024-Dec
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49132
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49128
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49123
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49120
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49119
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49116
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49115
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49108
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49106
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49127
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49112
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49118
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49122
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49126
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49124
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-49117
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-49138
Second month in a row where the QQL you provide is wrong. If you copy and paste the QQL you provided to be entered in to VMDR (vulnerabilities.vulnerability.qid:110482 or qid:110483 or qid: 92197 or qid: 92198 or qid: 92199 or qid: 92200) it will ONLY display the first QID NOT the rest of the them.
I had to created this QQL in order to see ALL related QIDs (vulnerabilities.vulnerability.qid:110482 or vulnerabilities.vulnerability.qid:92197 or vulnerabilities.vulnerability.qid:92198 or vulnerabilities.vulnerability.qid:92199 or vulnerabilities.vulnerability.qid:92200)
If there is something I’m doing wrong please let me know.
*UPDATED*
You can use this QQL to detect properly:
vulnerabilities.vulnerability: (qid:110482 or qid:110483 or qid: 92197 or qid: 92198 or qid: 92199 or qid: 92200)
The omission of the properly placed round brackets is the fix.